Cyber Command
Cyber Command Corporation is an IRS approved 501(c)(3) nonprofit, public charity that offers cybersecurity awareness training and develops viable cybersecurity defense software.
Mission Statement
Cybersecurity concerns are one of the most critical threats facing the security of our nation, which impacts all United States citizens, including individuals, families, businesses of all sizes and verticals, and government organizations.
Our mission is to reduce threat risk by promoting cybersecurity education and awareness, facilitating research, advancing development, and enabling dissemination of cybersecurity defense products and services to USA individuals, public and private organizations.
Want to organize a free virtual or in-person cybersecurity class for seniors in your neighborhood? Please contact us below and we’ll get the process started!
Cybersecurity Intelligence Feed & Resources
This section contains free cybersecurity related articles and knowledge to help learn critical cybersecurity lessons.
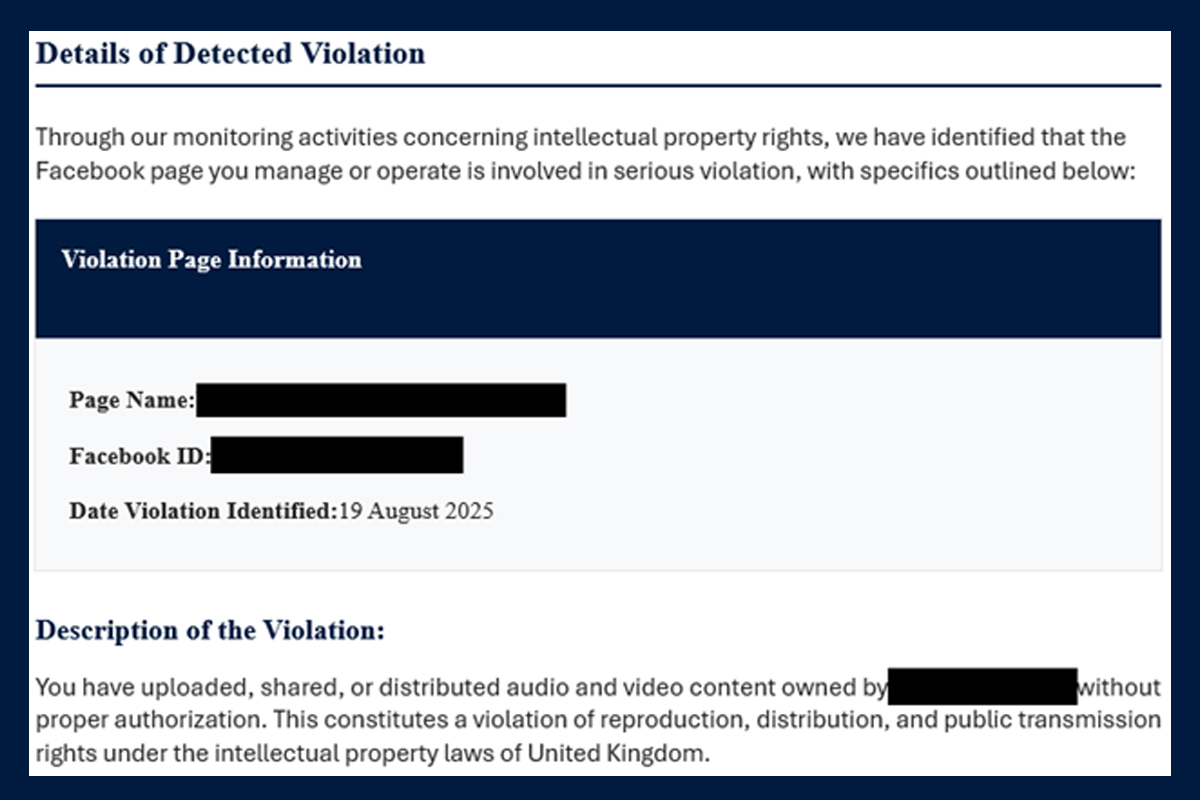
Phishing Scam Exploits Google AppSheet
The NJCCIC received reports of a phishing scam sent to New Jersey State employees, abusing the legitimate and trusted Google AppSheet, a no-code application development platform for mobile, tablet, and web applications. In this phishing scam, threat actors...
Uptick in Investment Schemes
Over the past several weeks, the NJCCIC observed an uptick in investment schemes, resulting in losses between $900 and $1.8 million. Threat actors pose as experienced investment advisors or registered professionals as part of an investment group.
Multiple Vulnerabilities in Commvault Backup
Multiple vulnerabilities have been discovered in Commvault Backup & Recovery, which when chained together, could allow for remote code execution. Commvault Backup & Recovery is a comprehensive data protection solution that offers a range of services for safeguarding data.
Vulnerabilities in Cisco Security Products
Multiple vulnerabilities have been discovered in Cisco security products that could allow for arbitrary code execution. Successful exploitation of the most severe of these vulnerabilities could allow for arbitrary code execution in the context of the user associated with the service.
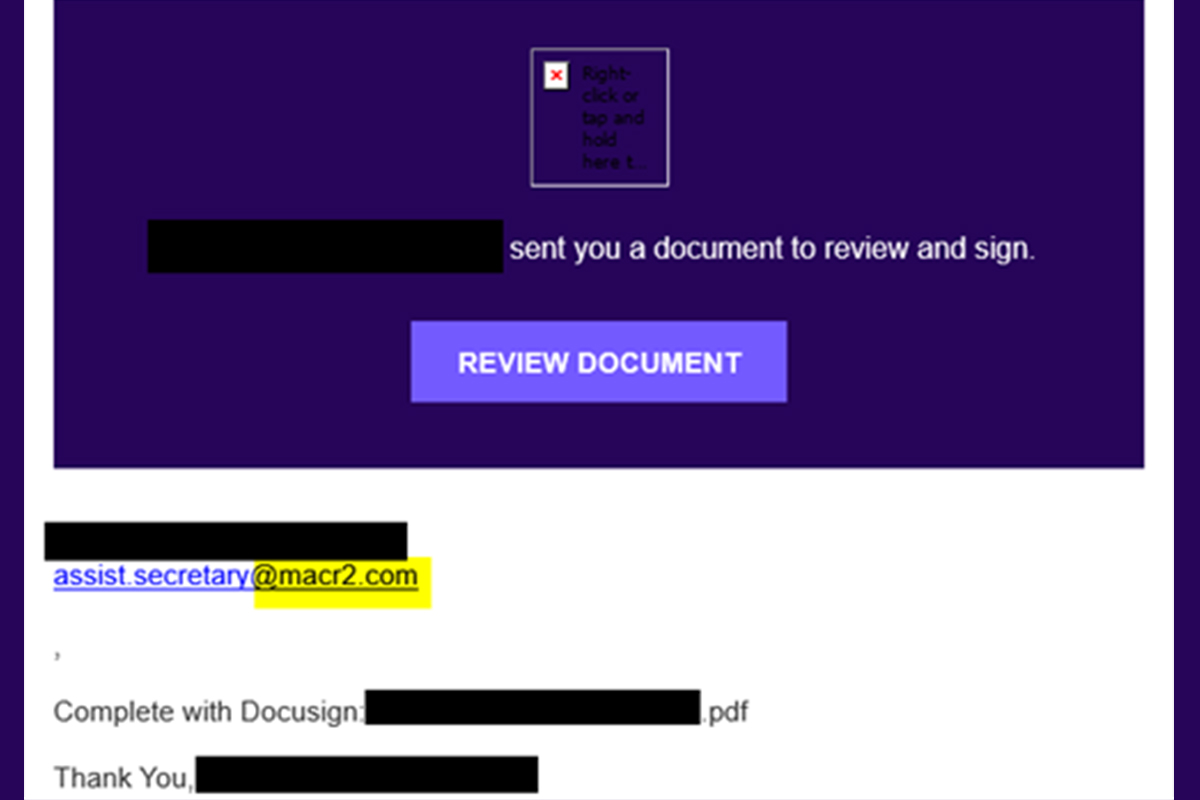
Abuse of Legitimate Docusign Platform
The NJCCIC received reports of a phishing scam abusing the legitimate Docusign platform and impersonating a New Jersey organization. In the Docusign envelope email notification, the impersonated organization’s name appears in the sender’s display name and the body of the email.
PDQ Connect Abused to Gain Remote Access
The NJCCIC observed multiple campaigns in which threat actors attempted to trick users into downloading the PDQ Connect Agent. PDQ Connect is a platform that allows agent-based device management for both remote and local devices. Once installed, threat actors can utilize...
Multiple Vulnerabilities in Fortinet Products
Multiple vulnerabilities have been discovered in Fortinet products, the most severe of which could allow for remote code execution. Successful exploitation of the most severe of these vulnerabilities could allow for remote code execution in the context of the affected service account.
Multiple Vulnerabilities in Adobe Products
Multiple vulnerabilities have been discovered in Adobe products, the most severe of which could allow for arbitrary code execution. Successful exploitation of the most severe of these vulnerabilities could allow for arbitrary code execution in the context of the logged on user.
Critical Patches Issued for Microsoft Products
Multiple vulnerabilities have been discovered in Microsoft products, the most severe of which could allow for remote code execution in the context of the logged on user. Depending on the privileges associated with the user, an attacker could install programs; view, change, or delete data.
Our Services
C3 helps reduce the risk of compromise by promoting cybersecurity education and awareness, and by facilitating research, development and dissemination of viable cybersecurity defense products and services to individuals, public and private organizations in the United States.
In-Person Training Classes
Virtual Classes
Phishing Simulations
Security Posture Analysis
Credential Leak Checks
Policies, Procedures & Plans
Phishing Attack Prevention
Network Intrusion Protection
Actionable Intelligence
Cyber Command is a registered 501(c)(3) nonprofit, public charity. EIN 93-2718000.
Our Board of Directors

Joshua Weiss, President

Arthur Warady, Treasurer

Kelly Whitis, Secretary
Contact Us
We’d love to hear from you. Please use the contact form below to reach us.