Cyber Command
Cyber Command Corporation is an IRS approved 501(c)(3) nonprofit, public charity that offers cybersecurity awareness training and develops viable cybersecurity defense software.
Mission Statement
Cybersecurity concerns are one of the most critical threats facing the security of our nation, which impacts all United States citizens, including individuals, families, businesses of all sizes and verticals, and government organizations.
Our mission is to reduce threat risk by promoting cybersecurity education and awareness, facilitating research, advancing development, and enabling dissemination of cybersecurity defense products and services to USA individuals, public and private organizations.
Want to organize a free virtual or in-person cybersecurity class for seniors in your neighborhood? Please contact us below and we’ll get the process started!
Cybersecurity Intelligence Feed & Resources
This section contains free cybersecurity related articles and knowledge to help learn critical cybersecurity lessons.
Multiple Vulnerabilities in Cisco Products
Multiple vulnerabilities have been discovered in Cisco products, the most severe of which could allow for remote code execution. Cisco is a leading technology company best known for its networking hardware and software, such as routers and switches.
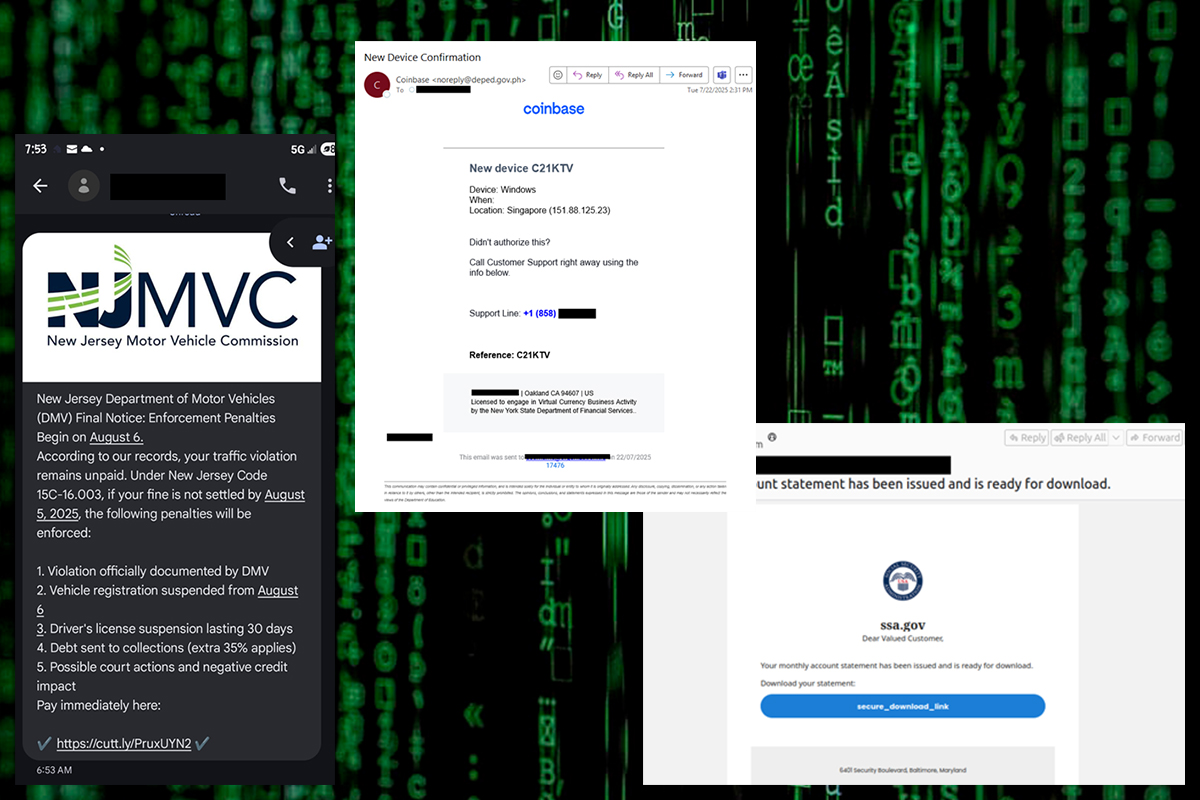
The “Smishing Triad” Campaign
Have you received a text message regarding an unpaid toll or package misdelivery lately? You are not the only one. Researchers discovered a SMiShing (SMS text phishing) campaign attributed to the "Smishing Triad" that has been circulating since April 2024.
Legitimate Jotform Platform Exploited
Jotform is used to create online forms and apps to collect data, process payments, and automate workflows without coding. It is a versatile tool for businesses and individuals in legitimate use cases. However, Jotform can also create opportunities for threat actors to exploit it.
A Vulnerability in Control Web Panel
A vulnerability has been discovered in CWP (aka Control Web Panel or CentOS Web Panel), which could allow for remote code execution. CWP, or Control Web Panel, is a free server administration tool for enterprise-based Linux distributions like CentOS, which simplifies managing web...
Conduent Business Services, LLC
Conduent Business Services, LLC (“Conduent”) is a third-party service provider for services related to printing and mailroom, document processing, payment integrity, government benefits, and other back-office support services. On January 13, Conduent discovered...
MFA Fatigue Phishing Campaign
Account compromises typically occur due to phishing emails, credential compromise, a lack of multi-factor authentication (MFA), exploited vulnerabilities, and data breaches. The NJCCIC recently received a report of a compromised account due to MFA fatigue (or MFA prompt bombing) .
A Rant Against Clicking Unverified Links
A mysterious email arrives in your inbox, promising treasures beyond your dreams if you visit the provided website within the hour. With only thoughts of a dream vacation, you click the link, and the page loads, asking for a CAPTCHA verification to continue.
Microsoft Exchange Security Best Practices
The Cybersecurity and Infrastructure Security Agency (CISA) and the National Security Agency (NSA) collaborated with international cybersecurity partners to develop a guide to help network defenders harden on-premises Exchange servers against exploitation.
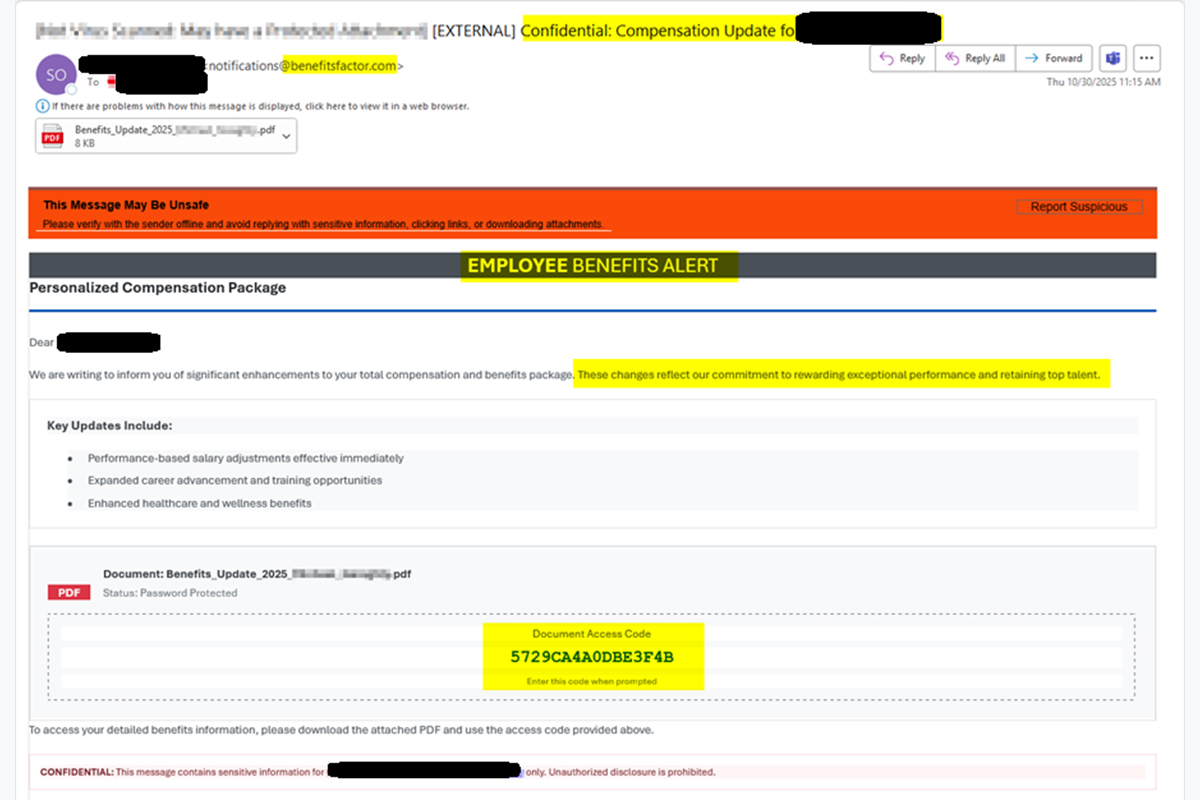
Phishing Impersonates Benefits Provider
The NJCCIC observed a phishing campaign targeting several public sector organizations in New Jersey. These emails are sent from accounts ending in the domain "benefitsfactor[.]com" and contain subject lines similar to "Confidential: Compensation Update for (recipient)."
Our Services
C3 helps reduce the risk of compromise by promoting cybersecurity education and awareness, and by facilitating research, development and dissemination of viable cybersecurity defense products and services to individuals, public and private organizations in the United States.
In-Person Training Classes
Virtual Classes
Phishing Simulations
Security Posture Analysis
Credential Leak Checks
Policies, Procedures & Plans
Phishing Attack Prevention
Network Intrusion Protection
Actionable Intelligence
Cyber Command is a registered 501(c)(3) nonprofit, public charity. EIN 93-2718000.
Our Board of Directors

Joshua Weiss, President

Arthur Warady, Treasurer

Kelly Whitis, Secretary
Contact Us
We’d love to hear from you. Please use the contact form below to reach us.