2023 Cybersecurity Lessons – Geopolitics
Global Attacks
December 28, 2023
Throughout 2023, cyberattacks affected organizations, governments, businesses, and private residents in New Jersey, resulting in monetary loss, degradation and interruption of services and resources, reputational damage, exposure of sensitive information, emotional distress, and more. In an era dominated by digital connectivity, the importance of cybersecurity cannot be overstated. Reflecting on the evolving threat landscape is crucial as we approach the end of the year. This 3-part series explores different contributing factors to the cyber threat landscape.
Geopolitical Tensions
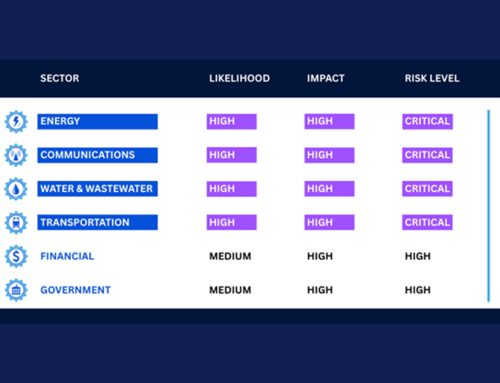
2023 has been marked by heightened geopolitical unrest. Nation-state threat actors carry out cyberattacks to advance their political and economic interests and influence, threatening critical information, services, and information systems, as well as public health and safety. This year, the Russia-Ukraine war entered its second year and hacktivist groups in support of Russia’s invasion of Ukraine launched distributed denial-of-service (DDOS) attacks across the United States. In the fall, armed conflict broke out between Israel and the Hamas militant group. These events triggered an uptick in cyberattacks against critical infrastructure sectors globally, including the United States, as nation-states sought to destabilize their adversaries.
Utilities
In November, water and wastewater utilities nationwide were targeted in a series of cyberattacks attributed to CyberAv3ngers, an Iranian-backed advanced persistent threat (APT) group. In these incidents, the threat actors compromised Unitronics programmable logic controllers (PLCs) used mainly in the Water and Wastewater sector but also implemented in other industries, including energy, food and beverage manufacturing, and healthcare. CyberAv3ngers claimed responsibility for over a dozen cyberattacks launched since October 30, stating that they targeted Unitronics as it is Israeli-made and “Every equipment ‘made in Israel” is CyberAv3ngers legal target.’”
Energy & Defense
The Energy and Defense sectors were also recently impacted when IntelBroker, an initial access broker known for targeting US government agencies , launched a cyberattack against General Electric (GE), which has divisions in power, renewable energy, and aerospace industries. The threat actors exfiltrated sensitive Defense Advanced Research Projects Agency (DARPA) data comprised of classified information, including weapons programs and artificial intelligence (AI) research.
Intensifying Tensions
As geopolitical tensions intensify, a notable shift in cyber threat tactics occurs, and cyberattacks attributed to state-aligned APT groups have surged. APT 28, a Russian threat group with ties to the General Staff Main Intelligence Directorate (GRU), leveraged a Microsoft Outlook zero-day identified as CVE-2023-23397 to target critical infrastructure in NATO countries. Additionally, nearly two dozen critical infrastructure organizations across the United States were compromised by threat actors affiliated with the Chinese People’s Liberation Army (PLA) within the past 12 months. Notably, military and communications networks on Guam were targeted in a string of attacks attributed to Volt Typhoon, a Chinese State-sponsored APT group.
Looking Ahead
There is a high probability that New Jersey’s public and private institutions, critical infrastructure assets, and residents will continue to face an array of cyberattacks that have the potential to adversely impact public health, the welfare and safety of its residents, the economy and public interest of the State, and national security. Individuals and organizations can fortify their defenses by analyzing evolving trends and implementing proactive security measures. As we look toward 2024, staying informed, collaborating, and prioritizing cybersecurity will be paramount in navigating these challenges.