2023 Q1 Qbot Trend Analysis
Microsoft,Scams
January 11, 2023
Qbot (also known as Qakbot) is a banking trojan with self-propagating and backdoor capabilities to a remote server, allowing threat actors to access compromised systems, steal information and log keystrokes, move laterally, evade detection, and install additional malware or ransomware, such as Black Basta. The NJCCIC continues to observe multiple Qbot phishing campaigns attempting to be delivered to New Jersey State employees to potentially gain remote access, exfiltrate data, and deploy ransomware. Qbot remains a prevalent threat as tactics continue and evolve. Messages typically appear to reply to previous email conversation threads, also known as thread hijacking. In January 2023, Qbot adversaries began using Microsoft OneNote attachments in their campaigns. An example of a malicious Microsoft One Note attachment is shown below.
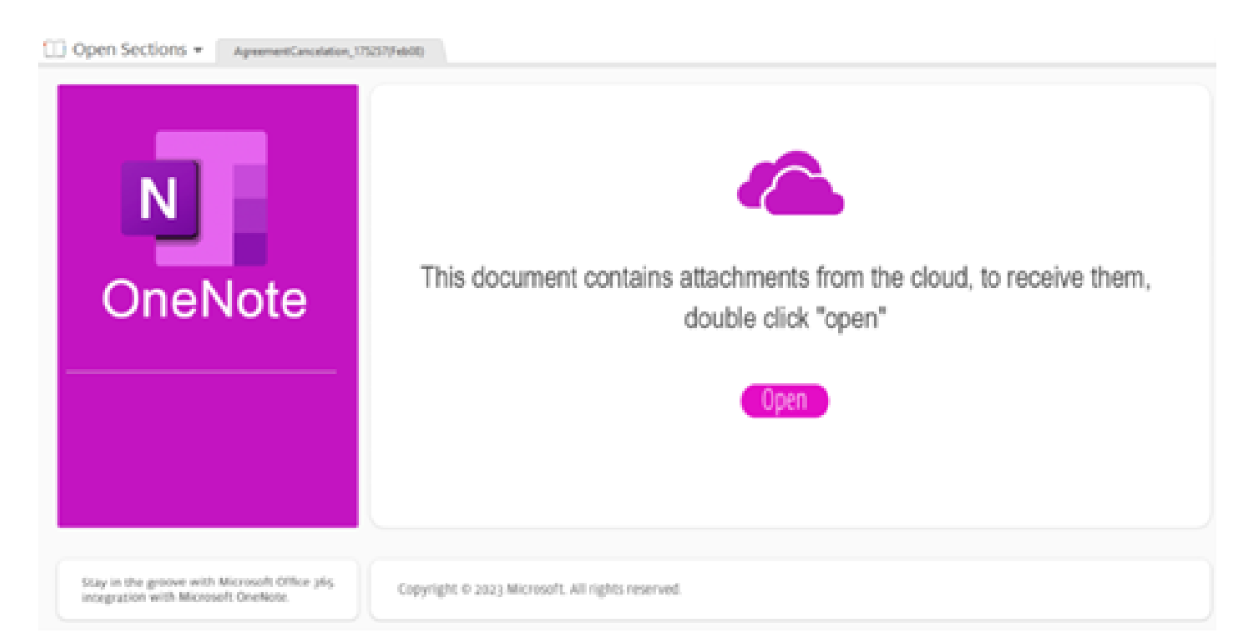
In January 2023, Qbot adversaries began using Microsoft OneNote attachments in their campaigns. The attachment’s naming convention contained keywords referencing an application, complaint, document, or fund. In February, they introduced zipped WSF attachments with naming conventions containing keywords referencing Adobe documents, certificates, and licenses. The zipped attachments consisted of a decoy PDF file, a benign TXT file, and a malicious WSF script that, if launched, downloaded Qbot from a URL link. By the end of February, they reintroduced PDF attachments with filenames that included keywords such as “note,” “list,” “document,” and “deal.” The PDF attachment contained a URL that led to a zipped ISO file containing LNK, CMD, and EXE files that launched the malicious script. By mid-March, they switched to zipped XLL attachments, which are Excel Add-In files, with “agreement” in the filename. They also used HTML attachments with “contract” in the filename containing a download button that, if clicked, initiated a JavaScript file and a PowerShell command to initiate Qbot. The JavaScript file used HTML smuggling, a technique used to smuggle encoded malicious scripts within a customized HTML attachment or webpage to evade security controls. An example of a malicious PDF attachment is shown below.
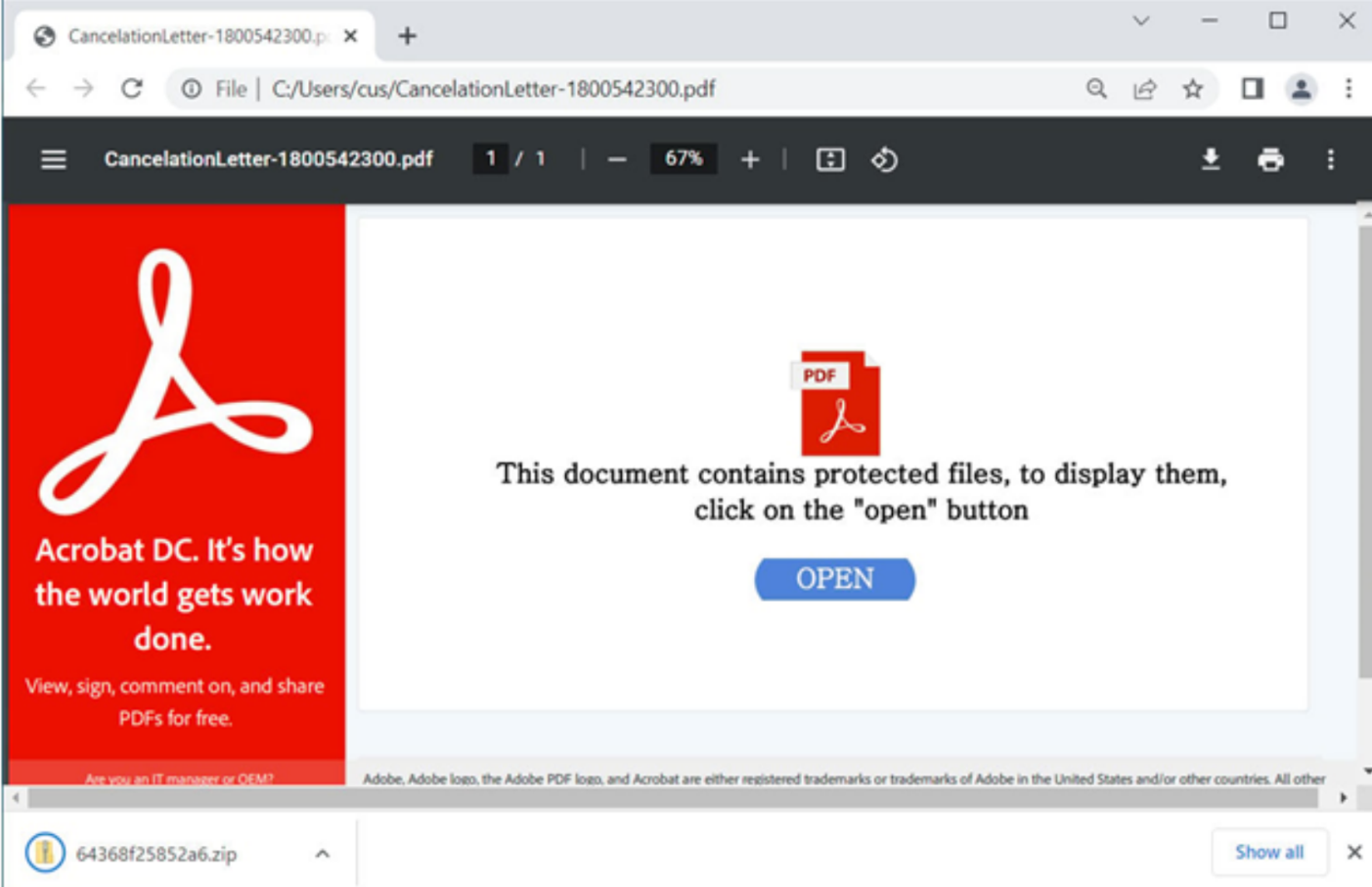
As cyber defenders identify and block these attempts, Qbot will continue to recycle old campaign techniques. The NJCCIC observed multiple Qbot campaigns this month, consistent with open-source reporting , in which Qbot adversaries reintroduced PDF attachments but with different keywords of complaint, claim, letter, and funds. The PDF attachments contain embedded URLs that, if clicked, download a WSF payload to use PowerShell and launch Qbot. Qbot was the most prevalent malware during the first quarter of 2023, with global organizations reporting impacts of 6 percent in January, 7 percent in February, and 10 percent in March. Based on our analysis and open-source reporting, the NJCCIC assesses with high confidence that Qbot will remain a persistent threat. For any further questions, contact us here at Cyber Command.