2024 Compromised Accounts: Infostealers
Scams
December 5, 2024
In 2023, SpyCloud reported that 61 percent of data breaches were associated with infostealer malware. Cyber threat actors use infostealers to exfiltrate sensitive data on the systems they infect, such as saved browser passwords and cookies, cryptocurrency wallets, credit card numbers, and details about the operating system, hardware components, and installed software. Threat actors often deliver infostealers via malicious email attachments, phishing links, fake online advertisements, compromised websites, and trojanized programs masquerading as legitimate software.
If a threat actor exfiltrates a user’s account credentials, they can be utilized in subsequent malicious cyber activity against the associated identity or organization, such as phishing campaigns and network access, or sold to other threat actors.
Based on information from a trusted third party, credentials utilized by public sector and critical infrastructure organizations in New Jersey were observed and sold on various dark web marketplaces such as Genesis Marketplace, Russian Market, and 2easy. Certain users’ credentials were identified several times, likely indicating the resale of information or failure to remove the malware from the host device.

Lumma, RedLine, and META were the most common infostealers implicated in stealing credentials of actively monitored domains. This finding aligns with security research trends reporting Lumma, RedLine, and META as the most prominent strains.
- Lumma was developed by “Shamel” and targets Windows 7-11 and multiple browsers including Chrome, Edge, and Firefox.
- Subscription-based infostealer targeting cryptocurrency wallets, browser data, and multi-factor authentication (MFA).
- Known for attacks via trojanized software and phishing emails.
- Uses “TeslaBrowser/5.5” user agent and “/c2sock” URI pattern, with multiple observed C2 servers across EMEA and US regions.
- First discovered in March 2020, it targets browser data (logins, cookies, credit cards) across Chromium and Firefox browsers, FTP clients, VPNs, and messaging applications.
- Popular Malware-as-a-Service (MaaS) that offers a subscription model, allowing buyers to manage attacks and sell stolen data on dark web forums.
- Collects extensive system info (IP address, hardware details, OS, anti-virus tools) and is heavily distributed through Telegram channels due to anonymity features.
- Can enable threat actors to bypass MFA via the theft of authentication cookies.
META:
- First observed in early 2022 and believed to have the same creator as RedLine.
- Similar functionality to RedLine, though an improved version with enhanced browser data extraction and cryptocurrency wallet targeting.
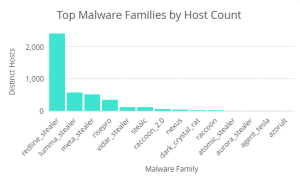
In October, international law enforcement actions led to the disruption of RedLine and META infostealers and charges against RedLine’s creator. This operation enabled the seizure of domains, servers, and Telegram accounts used by the infostealers’ administrators. Additionally, two domains used for command-and-control (C2) domains were seized. As a developer and administrator of RedLine, Maxim Rudometov was charged with access device fraud, conspiracy to commit computer intrusion, and money laundering.
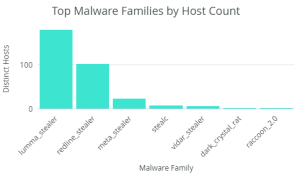
The takedown of RedLine and META infostealers will significantly reduce infections associated with those variants, as already indicated in Image 3. Compromises will likely be associated with variants unaffected by the takedown of RedLine and META domains and C2 servers, such as Lumma. Due to the lucrative nature of infostealers, MaaS models will persist, and new variants will be developed to fill the void left by RedLine and META. It is also possible that associates of RedLine and META could revive their infrastructure in the coming months.
SpyCloud reports an increase in the use of Xehook, Meduza, and Elusive infostealers; however, these variants have not yet impacted NJCCIC-monitored domains.
Recommendations
- Implement an endpoint detection and response solution that can identify the presence of infostealers on systems.
- Monitor and restrict access to sensitive directories, especially AppData and browser profile locations.
- If a user account is compromised, ensure authentication cookies and tokens are revoked.
- Implement network access controls and set shorter cookie expiration times.
- Create rules to alert of unusual login activity, such as logging in from two locations in a timeframe that would make it impossible to travel.
- Enable MFA across all user accounts.
- Require security awareness training focusing on phishing and social engineering tactics.





