2FA Campaigns Target Government
Scams
August 15, 2024
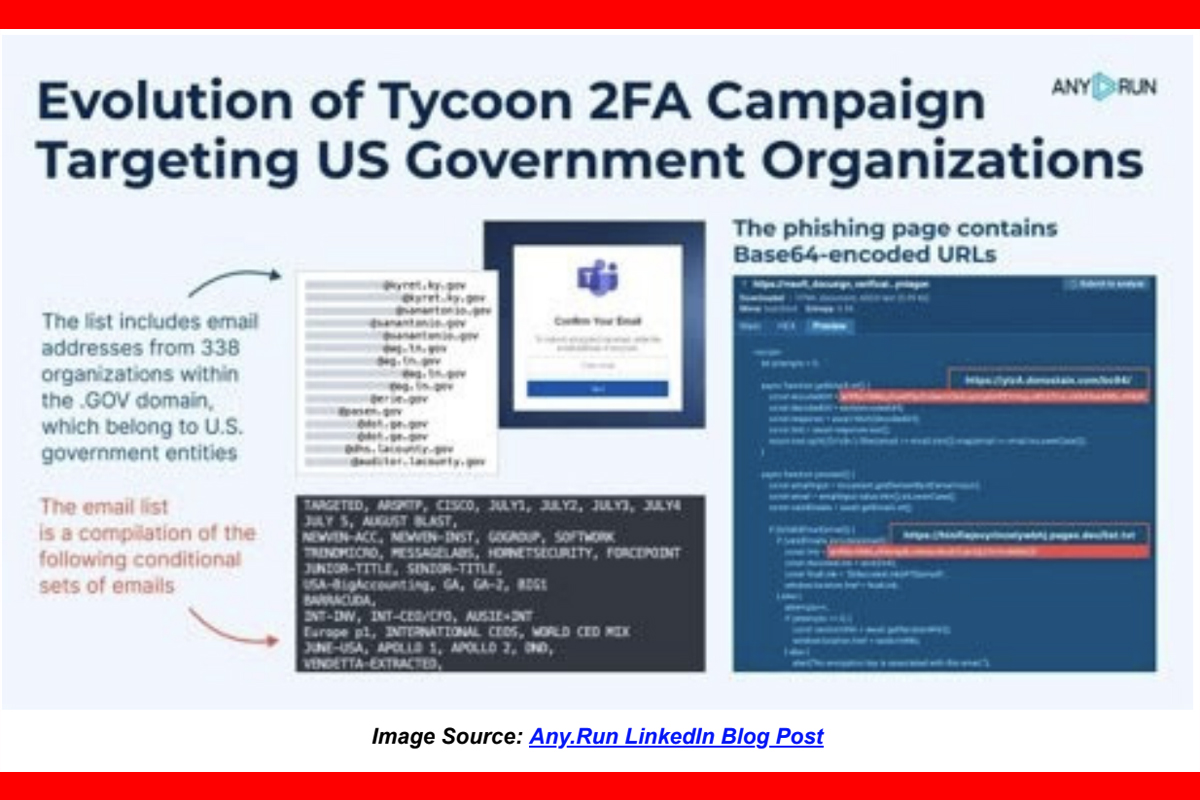
A sophisticated phishing campaign targeting Microsoft Teams was identified using the Tycoon 2FA Phish-kit phishing-as-a-service (PhaaS) platform to steal session cookies and bypass two-factor authentication (2FA) protection. After clicking on a phishing link, the victim is prompted to enter their email on the threat actor-controlled phishing page, MSOFT_DOCUSIGN_VERIFICATION_SECURED-DOC_OFFICE[.]zatrdg[.]com (Any.Run interactive analysis ). If the email used to authenticate is on the specified target list, the victim is redirected to an obfuscated phishing domain, such as donostain[.]com, requesting their Microsoft account password. This website redirects to a Tycoon 2FA phishing page or a legitimate domain. Another recent tactic is exploiting “Error 500” or “no Internet Connection” messages. After attempting to refresh the page, the victim is redirected to a fake Microsoft 365 Outlook phishing website to steal credentials if entered. Some of these phishing websites may also include a CAPTCHA solution.
An additional recently identified campaign uses Amazon Simple Email Service (SES) and high-profile redirects to steal user credentials. The attack chain is designed to avoid detection, involving multiple stages and using compromised domains and services. According to a phishing sample analysis, the attack begins with an email from an Amazon SES client. These emails often contain a valid signature, adding to their appearance of legitimacy. The email usually includes two empty PDF attachments and a message from Docusign stating, “You have received a document to review and sign.” Despite occasionally failing SPF and DKIM checks, these emails may still appear legitimate due to the compromised source. Based on a report by Any.Run, when the “Review Document” link is clicked, victims are rerouted through a complex series of URLs to obscure the final phishing domain.
Recommendations
- Avoid relying solely on SPF and DKIM checks to validate emails, as the source email may be compromised.
- Avoid responding to messages, clicking links, or opening attachments from unknown or unverified senders, and exercise caution with emails from known senders.
- Confirm the legitimacy of requests by contacting the sender via a separate means of communication, such as by phone, using contact information obtained from official sources before responding, divulging sensitive information, or providing funds.
- Navigate directly to legitimate websites and verify before submitting account credentials or providing personal or financial information.
- Use strong, unique passwords and enable multi-factor authentication (MFA) where available, choosing authentication apps or hardware tokens over SMS text-based codes.
- Reduce your digital footprint so that threat actors cannot easily target you.
- Report malicious cyber activity to the FBI’s IC3 and the NJCCIC.