404 Snake Keylogger Stealing Data
Malware
May 22, 2025
The NJCCIC’s email security solution has observed an uptick in campaigns distributing 404 Keylogger infostealing malware. 404 Keylogger, also known as Snake Keylogger, is a malware-as-a-service (MaaS) that works both as a downloader and an information-stealing malware. Once installed, this malware can steal credentials, log keystrokes, capture screenshots, harvest emails, and grab clipboard data. Stolen data is exfiltrated using Simple Mail Transfer Protocol ( SMTP), File Transfer Protocol (FTP), and Telegram bots.
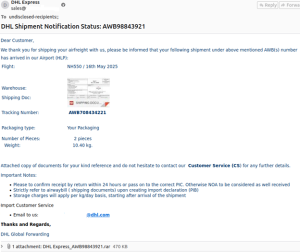
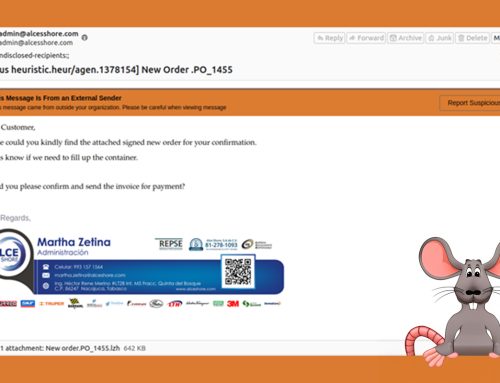
In one campaign, the threat actor sends an email impersonating a DHL shipment notice. The email includes what appears to be a PDF of a shipping document. However, upon further inspection, the file has a .rar extension, which is a compressed archive that may hide potentially malicious files waiting to be extracted. The email includes details about the shipment, including package weight and flight information, to make it seem legitimate. At the end of the email, the sender warns that failure to act will incur charges to prompt a potential victim to take action. Other 404 Keylogger campaigns were recently spotted posing as purchase order confirmations and requests for quotes.
Upon extracting the file, the compressed executables use the AutoIt scripting language to install and run the 404 Keylogger. A copy of itself is saved as ‘ageless.exe’ to the %Local_AppData%\supergroup folder, with its attribute set to hidden. A second file, named ageless.vbs, is saved to the %Startup% folder. This script enables the malware to run on system startup to establish persistence on the infected machine.
Recommendations
- Avoid clicking links and opening attachments in unsolicited emails.
- Confirm requests from senders via contact information obtained from verified and official sources.
- Type official website URLs into browsers manually.
- Facilitate user awareness training to include these types of phishing-based techniques.
- Maintain robust and up-to-date endpoint detection tools on every endpoint.
- Consider leveraging behavior-based detection tools rather than signature-based tools.
- Report this activity to the FBI’s IC3 and the NJCCIC.