A Five-Year Overview of Chinese APT Activity
Global Attacks
November 14, 2024
For over five years, Sophos analysts have monitored cyber threats from Chinese groups targeting its firewalls with advanced botnets and tailored malware. Collaborating cybersecurity organizations and law enforcement attributed clusters of activity to groups like Volt Typhoon, APT31, and APT41/Winnti. A series of reports titled “Pacific Rim” was released detailing analyses and mitigations associated with incidents attributed to these advanced persistent threat (APT) groups who increasingly target networking devices worldwide.
Analysts identified significant exploit research in Sichuan, China, assessing with high confidence that these exploits are shared among Chinese state-sponsored groups with varying objectives. Key trends in attacker behavior included advanced stealth techniques and persistence capabilities, such as using legitimate system tools, memory-only trojans, and a new firewall bootkit. Additionally, operational security was enhanced to disrupt firewall telemetry, complicating detection and open-source intelligence efforts.
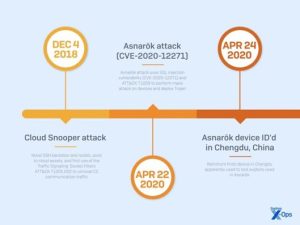
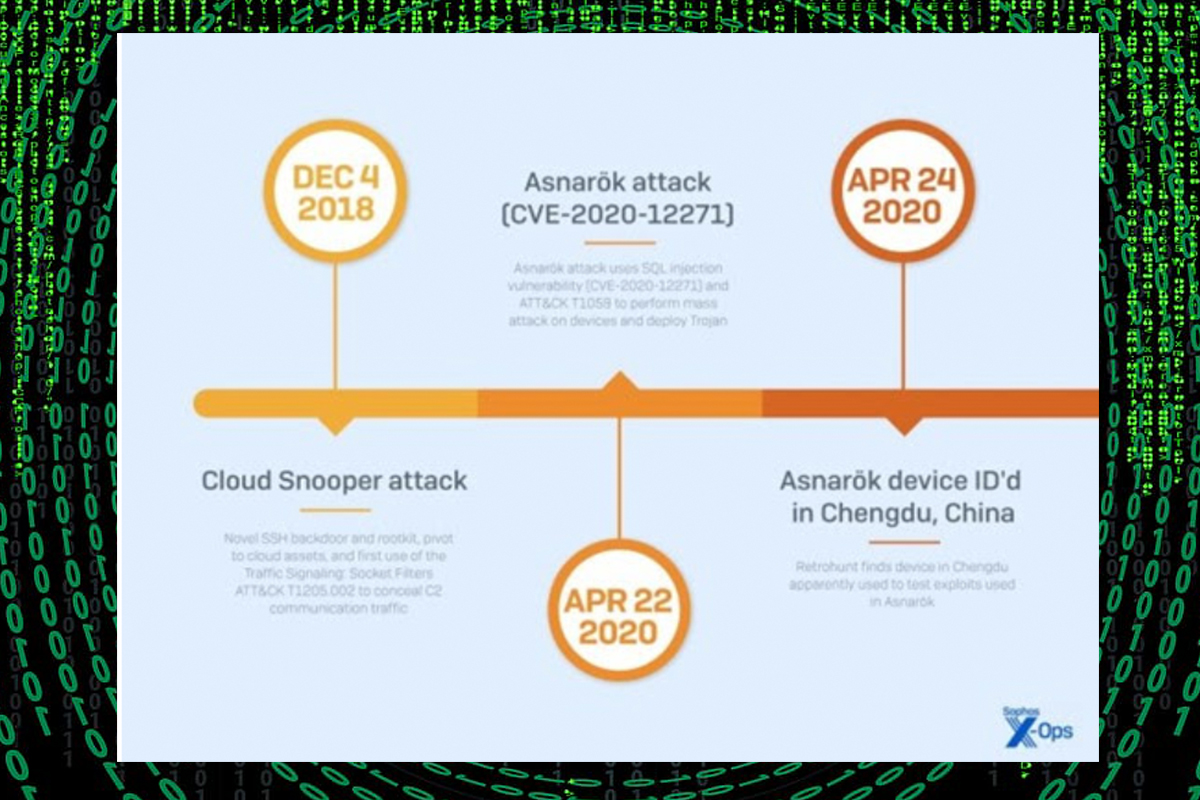
They quickly exploited previously unknown vulnerabilities in WAN-facing services, allowing them to retrieve stored information and deliver payloads within the device firmware and to devices on the internal LAN. These attacks targeted well-known manufacturers, including Fortinet, Barracuda,
In April 2020, a report detailing the first wave of attacks, named Asnarök, was released. Additionally, links between bug bounty researchers who disclosed vulnerabilities and the aforementioned adversary groups were identified in two campaigns. The analysts determined with moderate confidence that a research community in Chengdu’s educational institutions is collaborating on vulnerability research and sharing findings with Chinese government-affiliated contractors involved in offensive operations.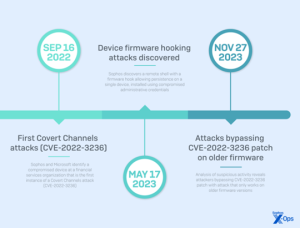
In mid-2022, threat actors shifted to highly targeted attacks against specific entities, including government agencies, critical infrastructure groups, healthcare providers, and military-adjacent businesses. They employed a manual “active adversary” approach and various tactics, including stealthy persistence techniques. The most common initial access vector for deploying these attacks was through the exploitation of known vulnerabilities; however, analysts also identified some incidents in which valid administrative credentials were used from the LAN side, indicating perimeter devices were exploited for persistence and remote access after gaining network access by other means.
Recommendations
- Keep systems up to date and apply patches after appropriate testing.
- Implement cybersecurity best practices to reduce risk and increase resiliency to cyber threats.
- Utilize monitoring and detection solutions to identify suspicious login attempts and user behavior.
- Conduct continuous monitoring and threat hunting. Ingest techniques and indicators of compromise found in the Pacific Rim reports into endpoint security solutions.
- Consider leveraging behavior-based detection tools rather than signature-based tools.
- Malicious cyber activity can be reported to the FBI’s IC3 and the NJCCIC.