A Loveable Problem Phishing Campaign
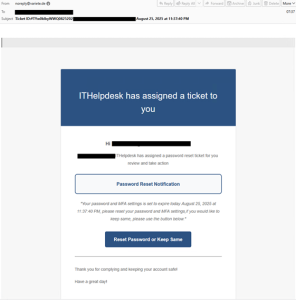
The NJCCIC observed a new adversary-in-the-middle (AiTM) phishing campaign aimed at harvesting credentials. This campaign starts with an email claiming to be from the help desk, with a link provided to reset or retain the current password.
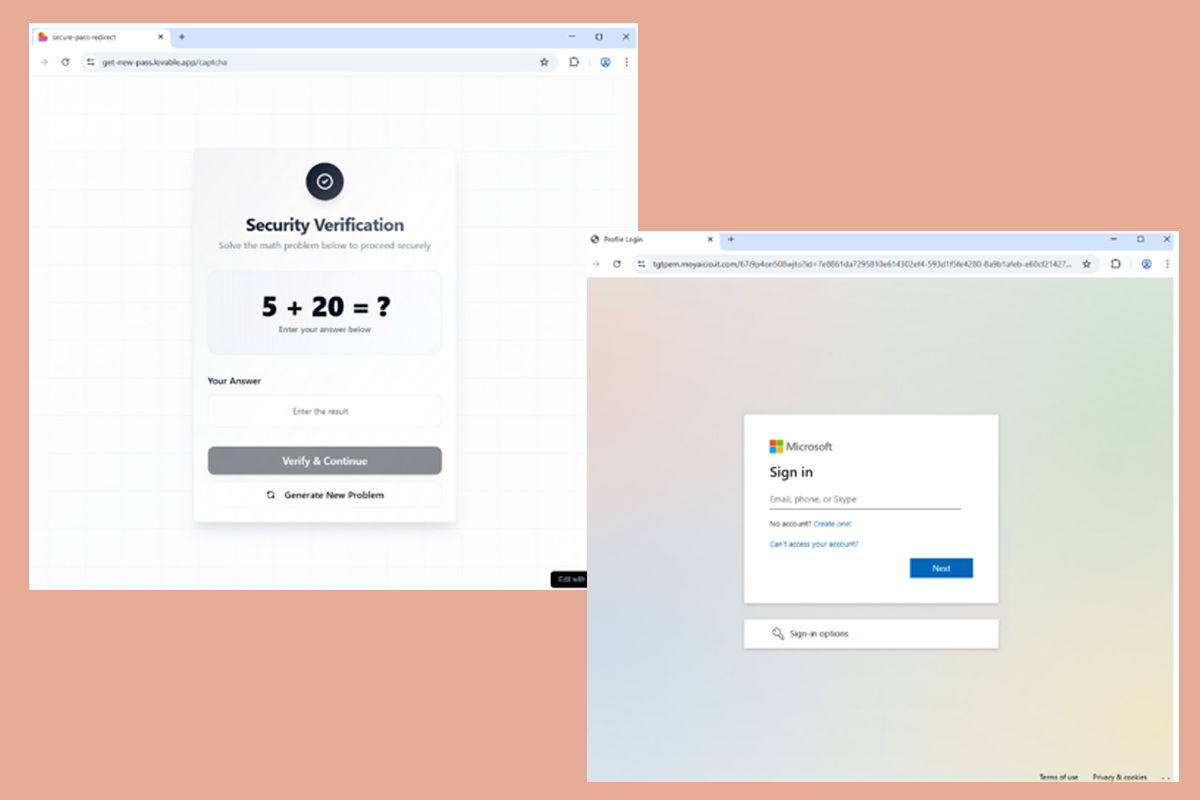
Upon clicking the provided link, users are directed to a Loveable.app math-based CAPTCHA, which helps threat actors bypass security measures. Completing the CAPTCHA redirects users to a fake Microsoft authentication page. Any credentials entered will be forwarded in real time using the synchronous relay capabilities from the Tycoon Phishing-as-a-Service (PhaaS) platform. Associated session cookies and two-factor authentication (2FA) tokens are also intercepted.
Recommendations
- Facilitate user awareness training to include these types of phishing-based techniques.
- Avoid clicking links and opening attachments in unsolicited emails.
- Confirm requests from senders via contact information obtained from verified and official sources.
- Review the Don’t Take the Bait! Phishing and Other Social Engineering Attacks NJCCIC product for more information on common phishing and social engineering attacks.
- Ensure multi-factor authentication (MFA) is enabled for all online accounts.
- Immediately change passwords and revoke active session tokens if entered into malicious websites.
- Report phishing and other malicious cyber activity to the NJCCIC and the FBI’s IC3.