Analysis of Marko Polo Cybercriminals
Scams
September 19, 2024
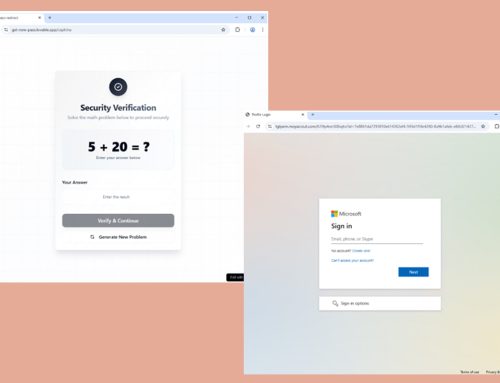
Analysts recently identified a cybercrime group known as Marko Polo, linked to at least 30 unique cryptocurrency and gaming-related scams that have likely compromised thousands of devices worldwide. The group is identified as a financially motivated “traffer team.ˮ Traffer teams are groups of organized individuals who redirect victims’ traffic to malicious content operated by other threat actors. They target online gaming personalities, cryptocurrency influencers, and technology professionals, posing as human resources or talent acquisition representatives on social media to lure victims with fake job opportunities and direct them to malicious websites. The group primarily consists of Russian, Ukrainian, and English speakers and is involved in various malicious activities, including the distribution of compromised Zoom meeting software builds and the impersonation of legitimate software and gaming platforms to deliver malware strains.
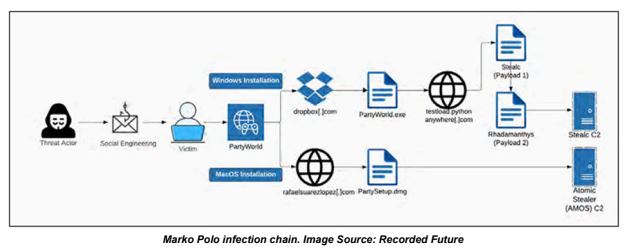
The group’s operations have stolen sensitive personal and corporate data, generating millions of dollars in illicit revenue. The widespread dissemination of Marko Polo’s scams and malware poses a significant risk to regular internet users and businesses. Impacted individuals may be vulnerable to identity theft and financial losses, while impacted businesses could be exposed to potential data breaches, reputational damage, and financial ramifications. The group’s adaptability and tendency to evolve its methods pose a persistent threat to cybersecurity defenses.
Recommendations
- The NJCCIC recommends users educate themselves and others on this and similar scams to prevent future victimization.
- There is no indication that these threats are credible; therefore, users are advised to refrain from sending funds and disregard these emails.
- Avoid clicking links, responding to, or otherwise acting on unsolicited text messages or emails.
- Use strong, unique passwords and enable MFA for all accounts where available, choosing authentication apps or hardware tokens over SMS text-based codes.
- Only download applications from reputable sources.
- Protect your digital assets by refraining from sending funds or installing wallets through unverified websites.
- Job seekers are advised to examine potential offers by contacting the human resources department directly via official contact information. Research potential employers and businesses online to determine if others have reported a scam before responding and providing sensitive information.
- Technical details and additional mitigations can be found in the Recorded Future report.
- These scams can be reported to the Federal Trade Commission (FTC), the FBI’s IC3 and the NJCCIC.