Android Banking Trojans Evolve
Google,Scams
May 23, 2024
Throughout 2023, researchers discovered 10 new trojans targeting Android devices and 19 banking malware families that had persisted since 2022. These malware families targeted 1,800 banking applications across 61 countries. Of the 1,800 targets, traditional banking applications remained the primary target at 61 percent, whereas cryptocurrency, social media, and messaging apps were targeted at the remaining 39 percent. Notable new trojan capabilities spotted throughout 2023 include:
- Automated Transfer System (ATS): Threat actors can harvest credentials and MFA tokens and initiate, modify, and execute transactions.
- Intercepting Notifications: Threat actors may utilize the ATS to delete transaction-related SMS or app alerts to evade user detection.
- Social Engineering Sophistication: Threat actors use social engineering tactics to masquerade as customer support agents to direct victims to download Trojan payloads voluntarily.
- Live Screen-Sharing Capability: Banking trojans may now feature live screen-sharing, allowing cybercriminals to gain real-time access to infected devices.
- Subscription-Based Malware: Threat actors offer these malicious tools for a monthly fee of $3,000 to $7,000.
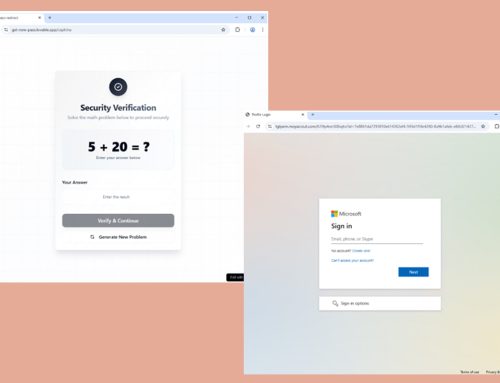
2024 has seen its share of new Android banking trojans and upgraded versions of old campaigns. These banking trojans are often packaged into legitimate-looking apps and impersonate well-known organizations. Masquerading as a fake Google Play updates application, Antidot comes with keylogging capabilities, remote control features, and a Websocket to give threat actors real-time control over infected devices.
The browser is one way to deliver these malicious applications to users. Brokewell has recently been found posing as an update page for Google Chrome. However, it was observed in previous campaigns targeting “buy now, pay later” financial services and spoofing an ID Austria application. Like other banking trojans, Brokewell has remote control and data-stealing capabilities. It also can bypass Android 13 restrictions introduced to prevent abuse of Accessibility Services by side-loaded apps (APKs).
A new Vultur campaign utilizes a telephone-oriented attack delivery (TOAD) attack to convince their target to install the malware. Victims receive a text message advising them to call a specified number if they did not authorize the transfer of a large amount of money. During the call, victims receive a second text message instructing them to install a trojanized version of the McAfee Security app. This new variant of Vultur also comes with many new features, including file management actions, blocking specific apps from executing, and disabling Keyguard to give unrestricted access to the device.
Recommendations
- Users are advised to only download applications from official sources.
- Users who downloaded the affected apps are urged to uninstall them promptly.
- Credentials used to log into malicious apps should immediately be changed.
- Review requested permissions and refrain from granting access to the “Accessibility Services.”
- Keep Google Play Protect enabled on all Android devices.