AZORult Malware HTML Smuggling
Malware
March 21, 2024
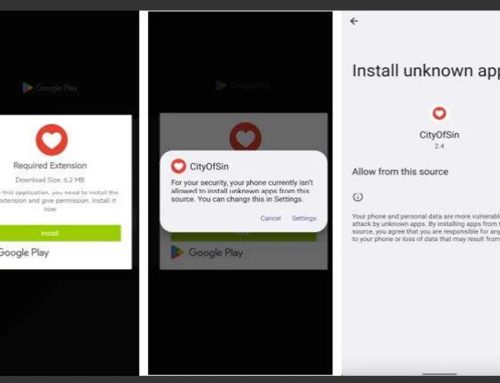
Threat actors are using HTML smuggling and fraudulent Google Sites pages to disseminate AZORult in a new malware campaign. AZORult, dubbed PuffStealer and Ruzalto, was first detected in 2016. It searches the desktop for sensitive documents using keywords for extensions and file names and collects browser data and cryptocurrency wallet information. AZORult’s payload has been distributed in phishing, malspam, and malvertising campaigns and is currently targeting the healthcare industry. This campaign is laden with obfuscation and evasion techniques to minimize the chance of detection by anti-malware software.
Researchers found that the HTML smuggling technique employed has AZORult’s malicious JavaScript embedded in a separate JSON file and hosted on an external website. Once the Google Site is visited, a CAPTCHA test is initiated to add a sense of legitimacy for users and protect the malware against URL scanners, such as VirusTotal. After passing the CAPTCHA test, the payload is reconstructed and downloaded to the victim’s machine. The downloaded file is disguised as a PDF file, often appearing as a bank statement to trick users into opening the file. Once launched, it will execute a series of PowerShell scripts. This payload includes ASMI bypass techniques and reflective code loading to bypass host and disk-based detection and minimize artifacts.
The NJCCIC recommends that users exercise caution and carefully examine emails before clicking links, ensuring the senders are known and legitimate. Additionally, refrain from downloading or opening suspicious software. If victimized, users are encouraged to report the activity to the FBI’s IC3 and the NJCCIC.