Banking Impersonation to Steal Credentials
Scams
April 3, 2025
Authentic bank notifications can help inform users of bank account activity, including balances and transactions. However, threat actors continue to impersonate banks and develop convincing messages that claim to involve bank account activity. These messages appear legitimate and official and may imply that the account security is at risk. The threat actors also create urgency and panic to persuade potential victims to take immediate action, such as divulging information or clicking on a link that spoofs a bank’s legitimate website.
The NJCCIC’s email security solution identified several credential phishing campaigns impersonating Chase Bank and Capital One Bank. The bank’s name is referenced in the sender’s display name and sometimes in the sender’s username but not in the sender’s domain name. Subject lines typically reference themes of account activation, account lock, card temporarily locked due to unusual activity, account activity review required, account temporarily restricted, high alert, and important message about your account. The threat actors use various top-level domain (TLDs), such as .com, .net, .de, .in, and .ru. and insert malicious links in the messages, including shortened URLs. These links direct potential victims to fraudulent bank portals that steal account credentials, MFA codes, and payment information.
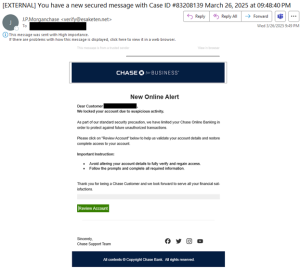
In one campaign, the message appears to be from Chase Bank and contains their branding, but the bank name is not referenced in the sender’s domain name. It also purports to be a new secured message with an established case ID to appear official. The case seems to indicate that the account was locked due to suspicious activity, and the target is requested to review the account to validate account details so that access to the account can be restored. The threat actors utilize various phishing landing pages and change them frequently to evade detection and continue their malicious activities. The phishing landing pages impersonate Chase Bank to validate the user’s information, including name, address, phone number, carrier PIN, Social Security number, email address and password, Chase Bank account credentials, MFA code, and ATM/debit card number and PIN.
The NJCCIC also received reports of threat actors impersonating a bank’s fraud department, such as Chase Bank and Wells Fargo Bank, claiming that fraudulent activity had been detected on the account or that an inside employee was stealing customer information. To mitigate, the threat actors advise the target to withdraw funds from the account and deposit them via ATM or Zelle into another account controlled by the threat actors.
Recommendations
- Refrain from responding to unsolicited communications, clicking links, or opening attachments from unknown senders.
- Exercise caution with communications from known senders.
- Confirm requests from senders via contact information obtained from verified and official sources.
- Type official website URLs into browsers manually and only submit account credentials and sensitive information on official websites.
- Use strong, unique passwords for all accounts and enable MFA where available, choosing authentication apps or hardware tokens over SMS text-based codes.
- If the account has been compromised, log out of all devices, revoke any access tokens, and reset passwords.
- Report suspicious or fraudulent communications to your bank.
- Report phishing emails and other malicious cyber activity to the Federal Trade Commission (FTC), FBI’s IC3, and the NJCCIC.





