Beware: Holiday Season Threats
Scams
November 27, 2024
The holiday season presents an attractive target for financially motivated cybercriminals who seek to exploit online retailers and shoppers. Despite the challenges posed by high inflation rates, the National Retail Federation (NRF) predicts a three to four percent increase in retail sales for the 2024 holiday season compared to 2023. The number of data breaches targeting the retail sector in 2024 has already reached unprecedented levels , with the cost of a data breach reaching $2.96 million, an 18 percent increase from 2023.
Online transactions are expected to rise as consumers seek deals and discounts, while broader economic factors, including general inflation, will continue influencing consumer spending. Retailers will likely offer coupon codes or discounts via email or SMS text messages to motivate consumers to shop online for higher-ticket items such as electronics and appliances.

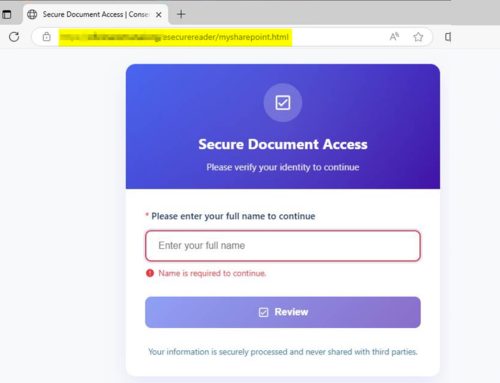
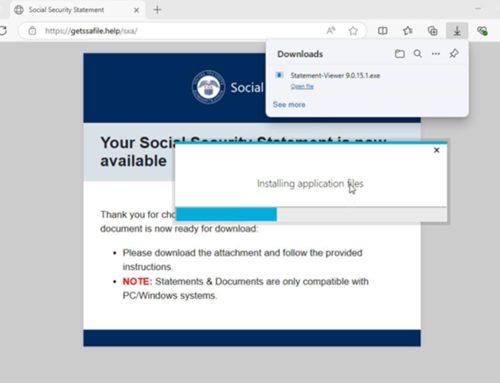
Analysis suggests threat actors will likely use tailored phishing emails during the holiday season. Threat actors continue to impersonate major brands and use social engineering to lure their targets through communications or malicious advertisements, introduce scare tactics, and attempt to steal personal data, financial information, account credentials, and funds. Additionally, employees working extended hours may be more susceptible to phishing emails due to divided attention and heightened performance demands. As teams are stretched thin with numerous responsibilities, they have less time to rigorously check security protocols, increasing the organization’s vulnerability to cyber threats during this critical period.

- Card tampering: Criminals alter packaging to steal information before the card is sold, draining funds once the card is loaded.
- Online attacks: Criminals hack online gift card accounts to use or sell stolen information.
- Victim-assisted fraud: Telemarketing groups trick individuals into buying gift cards and sharing codes, which are then sold to criminal organizations.
Warning signs of tampered gift cards include:
- visible tears around the packaging
- compromised pull tabs
- mismatched branding
- unusual PIN cover
If you suspect tampering, contact the customer support number on the back of the gift card.
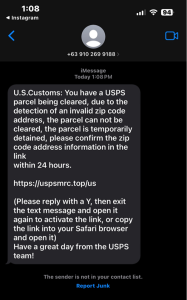
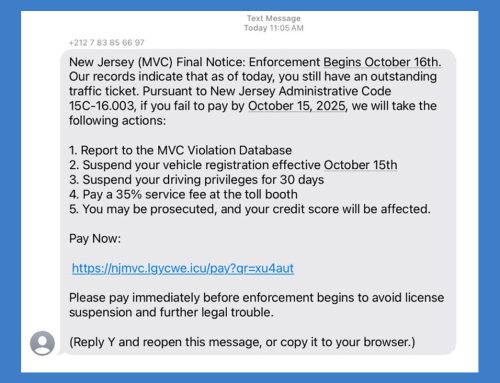
Lastly, SMS text message phishing is pervasive during the holiday shopping season. These messages may reference online purchases, deliveries, or accounts and prompt the recipient to click on a link or disclose sensitive information. As shoppers may be expecting messages relating to purchases or online accounts used to make these purchases, users could be more likely to respond to and take action on these messages under the assumption they are legitimate. Additionally, text messages impersonating toll services may become more prevalent as traveling increases during the holidays. FedEx, UPS, USPS, Amazon, and toll services are some of the most impersonated organizations in these text message phishing schemes during the holiday season.
Recommendations
- Avoid clicking on advertisements, social media links, promoted search results, or embedded URLs found in emails.
- Confirm requests from senders via contact information obtained from verified and official sources.
- Type official website URLs into browsers manually.
- Only submit account credentials and payment information on official websites.
- Follow the principle: “If it seems too good to be true, it likely is.”
- Do not feel obligated to make decisions under pressure. Scammers create a sense of urgency to pressure you into making hasty decisions without proper analysis.
- Use an advertisement and malicious content blocker that also protects against credit card skimming and other online threats.
- Monitor your financial statements and report suspicious activity.
- Use strong, unique passwords for all accounts and enable multi-factor authentication where available, choosing authentication apps or hardware tokens over SMS text-based codes.
- Reduce your digital footprint to reduce the likelihood of becoming a target for malicious actors.
- Review the NJCCIC product, Stay Cyber Safe During the Holidays, for additional attack techniques and recommendations.