Active Subdomain Hijacking Operation
Scams
February 29, 2024
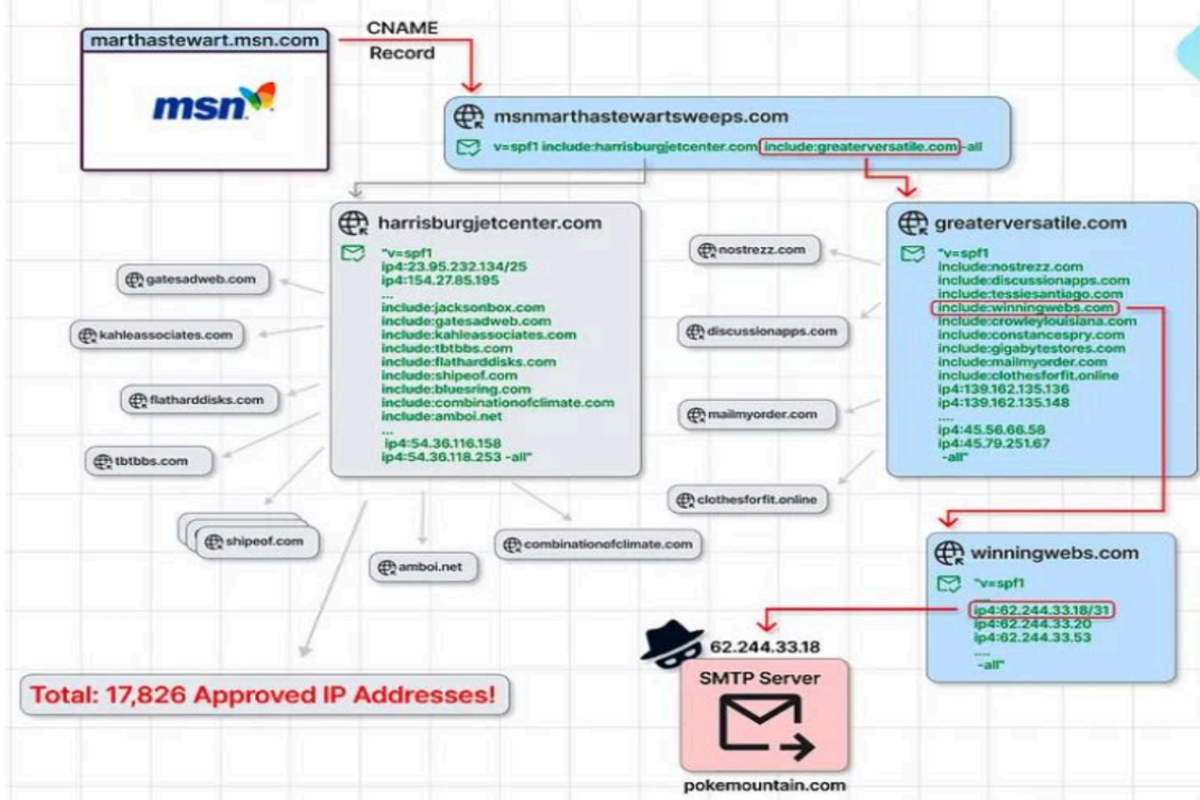
Subdomain hijacking occurs when threat actors gain control of a subdomain of a legitimate domain by taking over unused or abandoned subdomains or exploiting misconfigured DNS records. They systematically scan for forgotten subdomains with dangling CNAME records of abandoned domains via specific targeting or automated tools. The threat actors then register these subdomains under their ownership to host malicious content or initiate additional attacks, such as hosting phishing landing pages designed to harvest login credentials. Additionally, a DNS SPF record of a known domain may hold unused or abandoned subdomains associated with obsolete email or marketing-related services. Threat actors can take ownership of those subdomains, inject their IP address into the SPF record, and send emails on behalf of the primary domain name. Since 2022, researchers have tracked a sophisticated subdomain hijacking operation dubbed SubdoMailing . Over 8,000 domains and 13,000 subdomains for legitimate brands and organizations have been impacted, including VMware, McAfee, Symantec, Better Business Bureau, and more. While subdomain hijacking is not new, what is concerning about this operation is the magnitude of identified domains and subdomains already compromised and counting. The impacts of these successful attacks can lead to reputational damage, financial losses, operational disruption, data breaches, phishing and fraud, and malware distribution. The threat actor behind the SubdoMailing operation, ResurrecAds, leverages trusted domains and a sophisticated distribution architecture to bypass email authentication controls and send millions of spam and phishing emails daily. The emails are designed to appear legitimate and evade detection of standard text-based spam filters by including an image that, if clicked, triggers a series of click-redirects through different domains. The redirects check the device type and geographic location to custom tailor the content and maximize profit, such as malicious advertisements, affiliate links, quiz scams, phishing websites, and malware downloads.
Recommendation
We recommend that users and organizations educate themselves and others on these continuing threats and tactics to reduce victimization. Users are advised to refrain from responding to unsolicited communications, clicking links, or opening attachments from unknown senders, and exercise caution with communications from known senders. If unsure of the legitimacy, contact the sender via a separate means of communication, such as by phone, from trusted sources before taking action. If you suspect your PII has been compromised, please review the Identity Theft and Compromised PII NJCCIC Informational Report for additional recommendations and resources, including credit freezes and enabling MFA on accounts. Additionally, we advise reporting suspicious or fraudulent correspondence to the respective entity. Impersonation scams and other malicious cyber activity can be reported to the NJCCIC.
Reporting
The NJCCIC encourages recipients who discover signs of malicious cyber activity to contact the NJCCIC via the cyber incident report form at www.cyber.nj.gov/report.
Please do not hesitate to contact us here at Cyber Command with any questions.