Human Resources Phishing Emails
Scams
September 21, 2023
Threat actors continue their efforts to target vulnerable and distracted users via Human Resources (HR)-themed phishing emails.
What Happened?
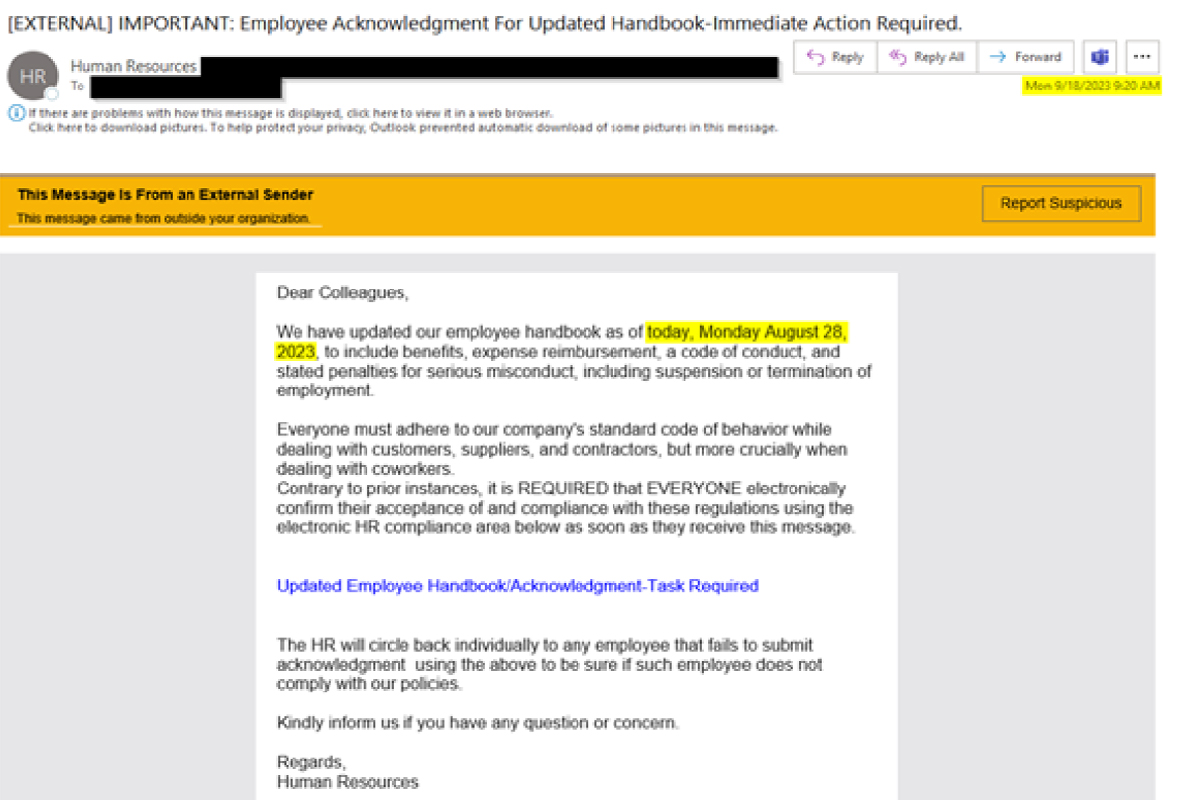
The NJCCIC observed multiple campaigns purporting to come from HR departments from US and non-US top-level domains (TLD), masquerading as acknowledgments of updated employee handbooks to harvest account credentials and steal information. Observed activity correlates with blocked emails sent to New Jersey State employees and similar reports targeting higher education organizations across the United States.
The sender’s display name in the above campaign impersonates HR to appear legitimate; however, upon closer inspection, the sender’s email address is from a non-US TLD. The message is flagged with an external banner alerting users that the email originates from outside the organization. The subject line instills a sense of urgency with keywords such as “important” and “immediate action required” to convince the target to click the acknowledgment link. If clicked, the target is directed to a credential phishing website, and any account credentials entered are sent to the threat actors in the background. The phishing email to the non-descript employee claims that HR will circle back individually if the employee fails to submit the acknowledgment.
Additionally, the delivery email date of September 18 in the above campaign does not match the date in the body of the email, August 28. This discrepancy raises concern and suggests that the threat actors failed to update their phishing email template. In other reported campaigns, however, the delivery date and date found in the message match. Furthermore, other campaigns contain sender display names of “HR Communication” and “Human Resource Management” from US TLDs and subject line keywords include “Urgent Task,” Handbook 2023,” “Attention!_Acknowledge_Handbook 2023,” or “Notification: Review and Sign the Revised Handbook for 2023-2024.”
What do you do?
For Organizations:
- Conduct regular phishing tests: Mimic real attacks at intervals to sharpen employee awareness.
- Interactive training: Use video/simulation measures to enhance skill retention.
For Users:
- Don’t respond to unsolicited emails: Avoid links/attachments from unknown senders.
- Exercise caution with known senders: Confirm authenticity before taking action.
- Verify HR requests directly: Contact HR rep, not via email.
- Type website URLs manually: Don’t click emailed links.
- Change passwords & enable MFA: If compromised, take immediate action.
- Report suspicious activity: Inform FBI IC3 and NJCCIC.
Additional Tips:
- Watch for sender name/email discrepancies (non-US TLDs are a red flag).
- Be wary of urgent subject lines (“Important”, “Immediate Action”).
- Check for inconsistencies like mismatched dates in the email.
- Remember, legitimate updates won’t use manipulative tactics.