Brand Impersonation Scams Continue
Scams
August 22, 2024
Businesses in the Information Technology sector act as critical service providers and part of a supply chain, store sensitive information, provide access to other accounts, and frequently engage with customers. These businesses deliver essential and frequently used services, such as email and other communications, cloud storage, online shopping, and more, increasing the likelihood that users will quickly respond to messages or inquiries from familiar and trustworthy brands. As of the second quarter of 2024, this sector ranks at the top of the list in brand impersonation and is an attractive and valuable target. Threat actors continue impersonating major technology companies, such as Google, Zoom, Facebook, Microsoft, and Apple, and their legitimate products and services. They use social engineering to lure their targets through communications or malicious ads, introduce scare tactics, and attempt to steal personal data, financial information, account credentials, and funds.
In the past month, PINEAPPLE and FLUXROOT hacker groups leveraged Google Cloud serverless projects to deliver and communicate with their malware, host and direct targets to phishing websites, and run malware and execute malicious scripts. In a separate campaign, threat actors abused Google Ads to post malicious ads that appeared official and verified by Google. If the user clicked on the malicious ad, they were redirected to a fake Google Authenticator site that inadvertently led to a signed payload hosted on GitHub. If installed, personal data would be at risk of being stolen via the attacker-controlled phishing website.
Additionally, threat actors targeted cryptocurrency investors and NFT holders, invited them to a Zoom meeting, and provided a malicious link that, if clicked, downloaded malware, added itself to the Windows Defender exclusion list, and stole funds. In a separate campaign, threat actors used Facebook to create fake pages, groups, ads, and content of popular generative artificial intelligence (AI) brands with malicious links that, if clicked, downloaded malware to steal passwords, cryptocurrency wallets, and information stored in the browser. Furthermore, threat actors spoofed the caller ID to display Microsoft’s name or number. They impersonated Microsoft employees or representatives to make fraudulent calls to trick potential victims into divulging personal or financial information.
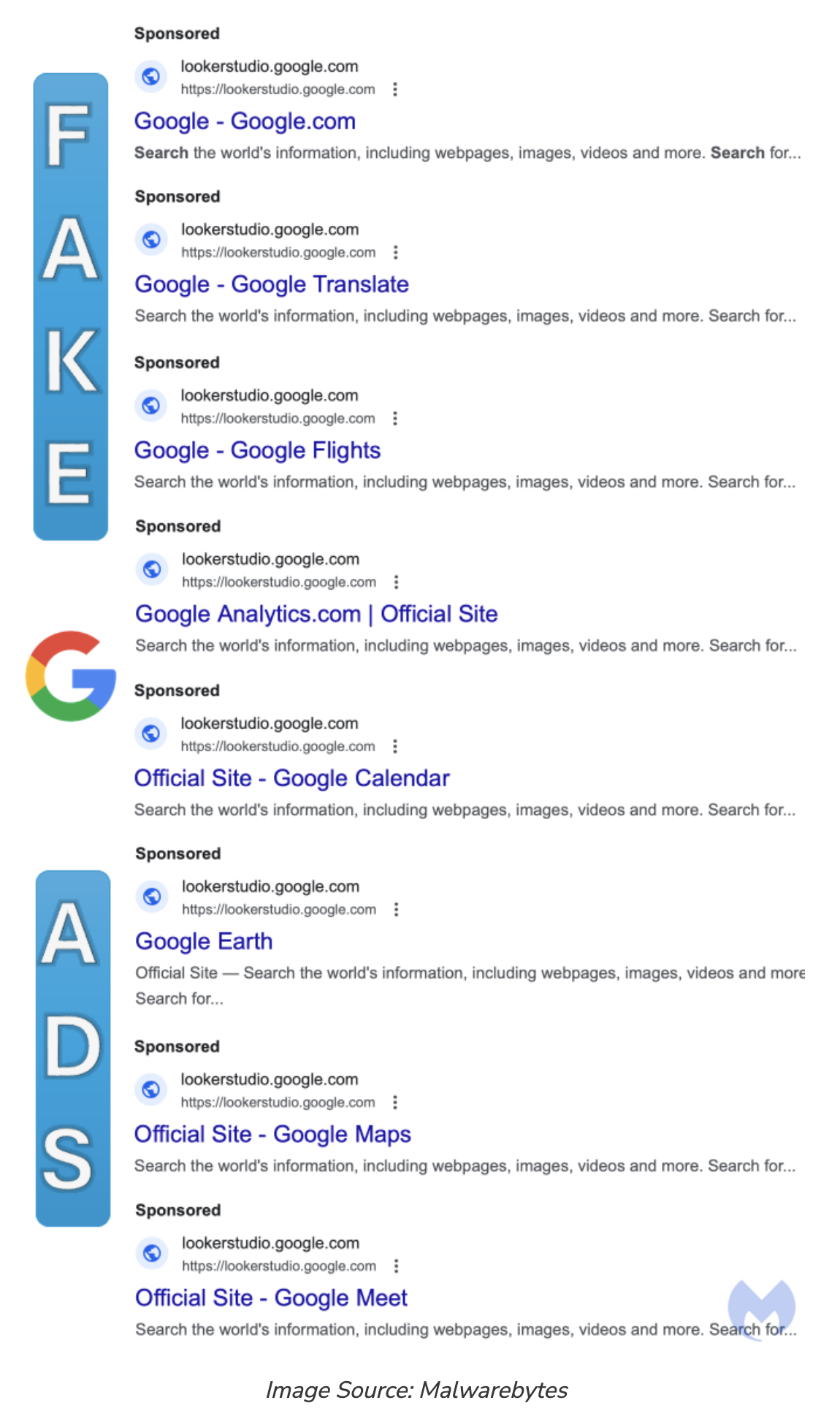
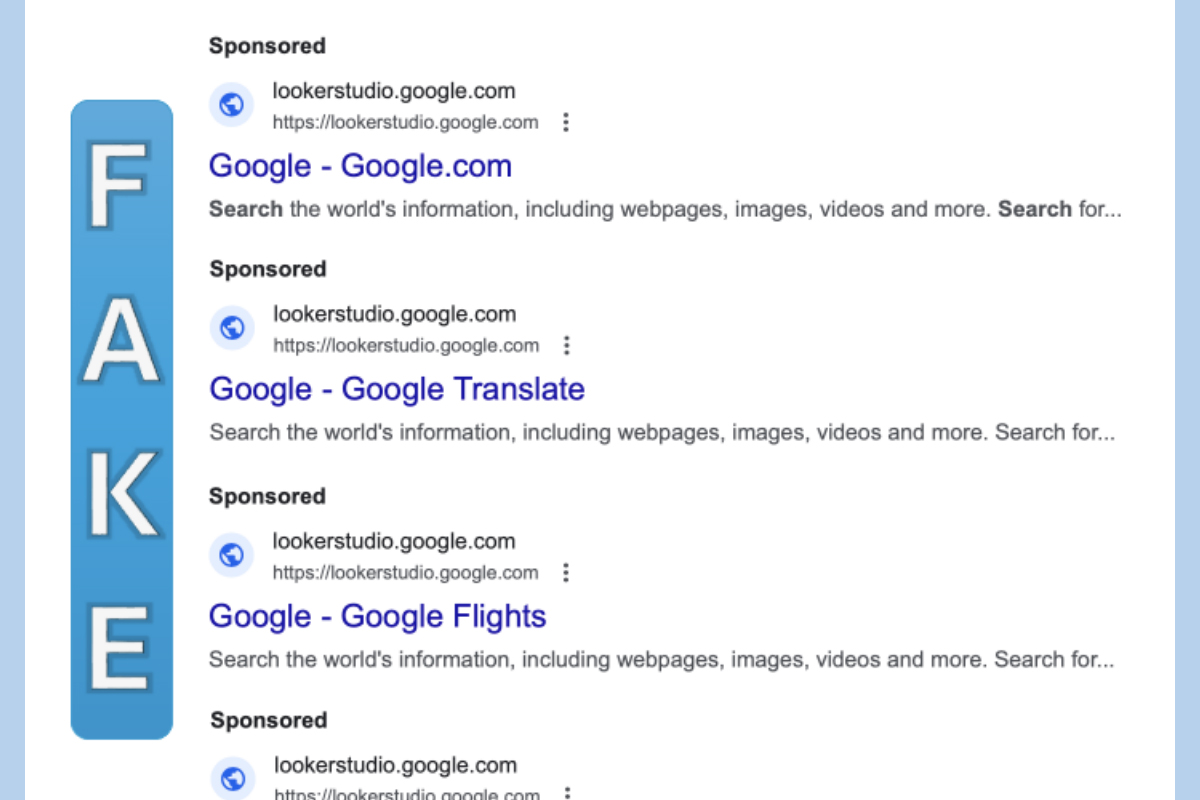
Threat actors are impersonating Google’s entire product line via malicious Google Search ads to direct potential victims to spoofed websites and Microsoft and Apple tech support scams. These malicious ads point to Google Search, Translate, Flights, Analytics, Calendar, Earth, Maps, Meet, and more. Upon closer inspection, the URLs of these ads are hosted on Looker Studio and contain an image of the Google Search home page that displays in full-screen mode. When the image is clicked, an embedded link launches a new tab to redirect the victim to a fake Microsoft or Apple alert page attempting to hijack the browser, play a recording, claim that the computer has been blocked, and advise the victim to contact support via the provided phone number. The threat actors behind the fake support number purport to be Microsoft or Apple representatives and persuade victims to purchase gift cards or log into their bank accounts to pay for the phony repair.
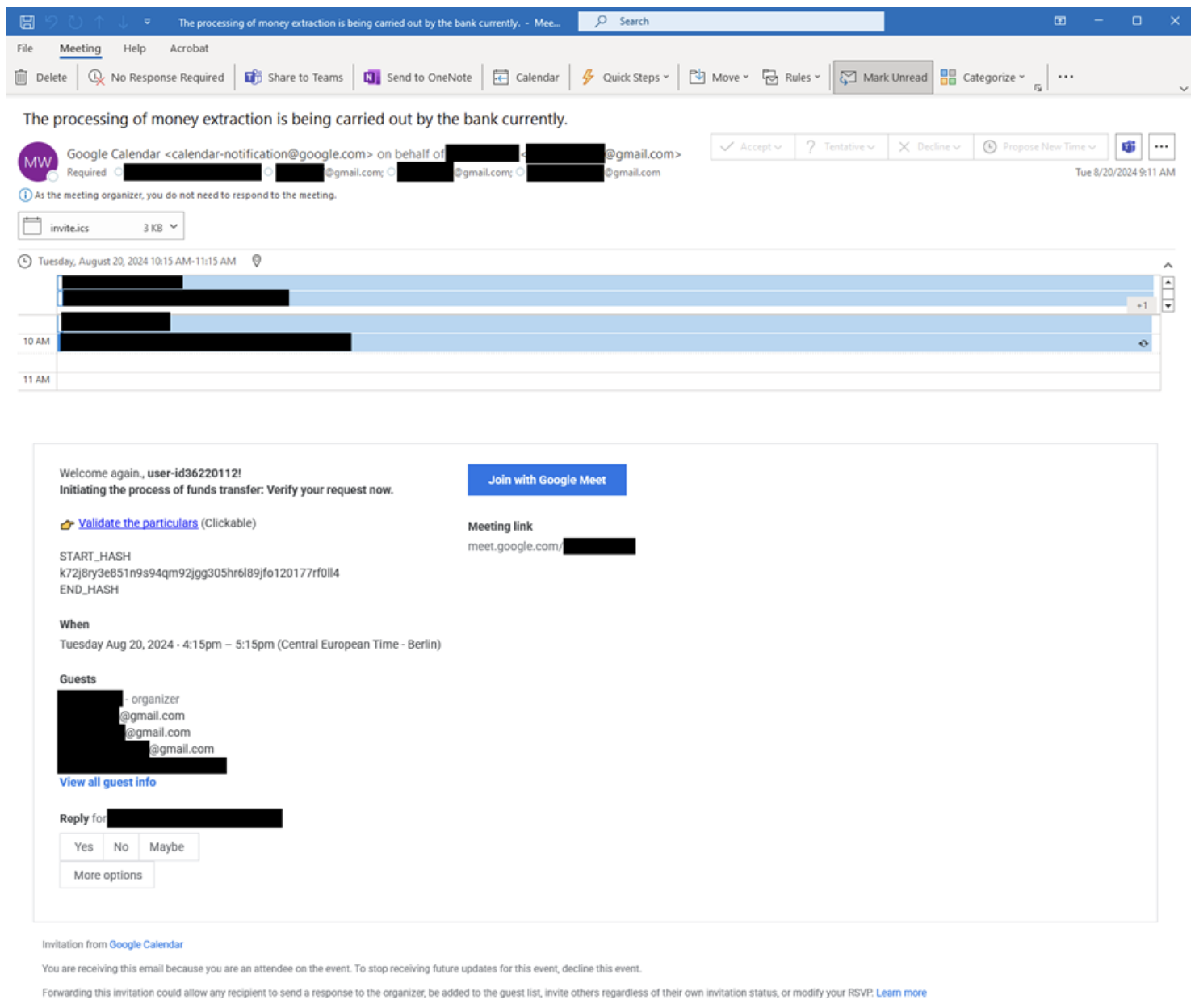
The NJCCIC’s email security solution detected multiple credential phishing campaigns targeting New Jersey State employees using legitimate products and services of major technology companies. In one campaign, threat actors utilize several products of the Google suite, including Gmail, Calendar, Forms, and Meet, to send phishing emails as calendar invitations to verify Bitcoin funds will be transferred. A Gmail user sends the calendar invitation to the target and other purported guests utilizing Gmail accounts, and it claims funds are currently being withdrawn to create a sense of urgency. One link in the calendar invitation directs the target to a Google Meet session, which initially displays that no camera was found and prompts the user for permission to access their microphone. Then, instead of waiting to be let into the session, the target can sign in with their Google account credentials. To supposedly validate the particulars, another link in the calendar invitation directs the target to a Google Forms page and, if submitted, displays a Bitcoin-themed landing page, utilizing the hxxps://globalminingbit[.]top domain, to receive Bitcoin bonus funds. After several redirects, clicking multiple buttons, and communicating with a chat representative, the target is prompted for their name, email address, financial information, and account information to receive the funds.
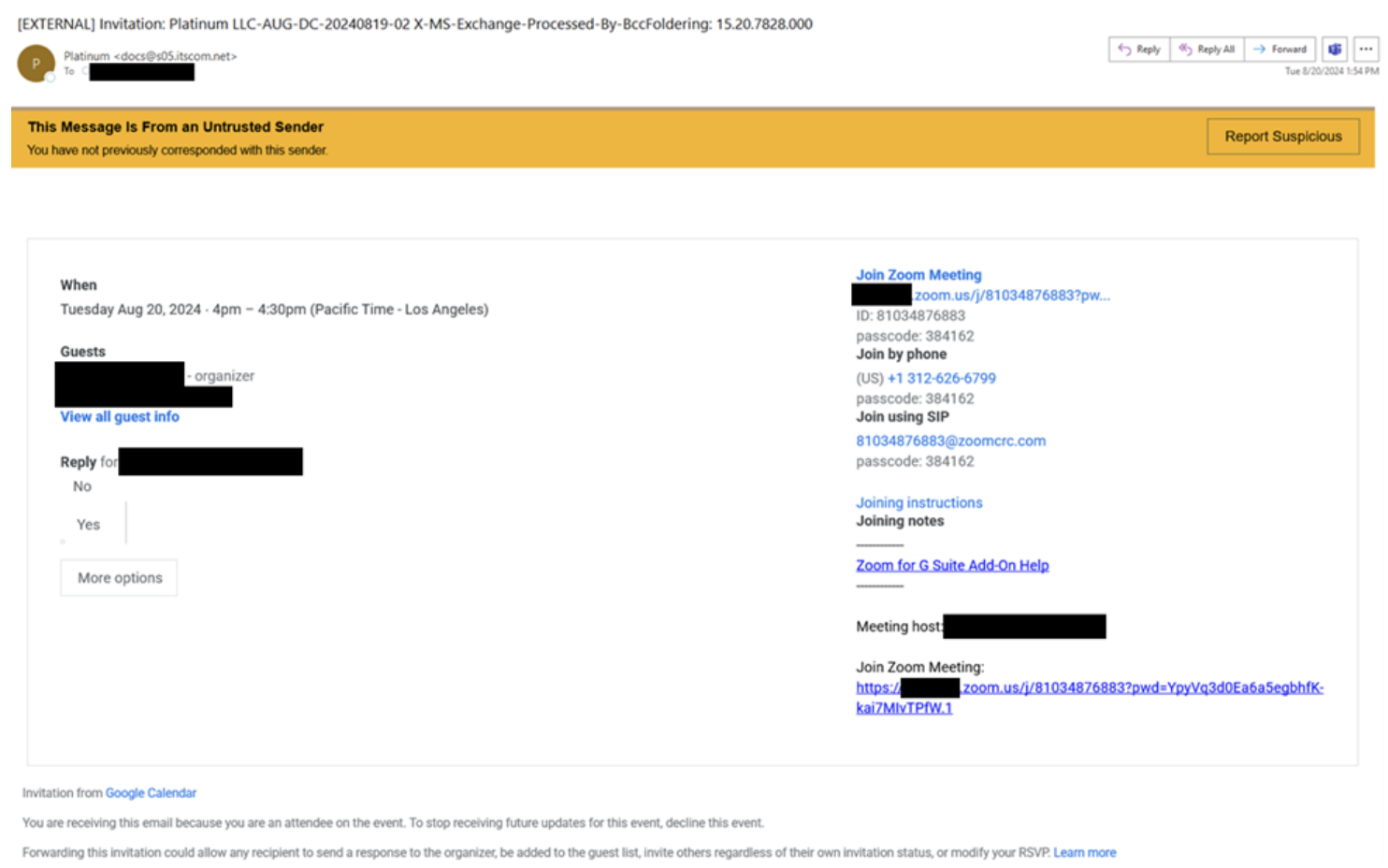
Threat actors are also sending fraudulent Zoom invitations in credential phishing campaigns. If the Zoom link is clicked, targets are directed to a fraudulent Microsoft SharePoint page with the organization’s branding, pointing to a newly registered hxxps://thepivoproject[.]com domain appended with the target’s email address and followed by a client identifier with random characters. If credentials are submitted on this phishing page, they are sent to the threat actors in the background.
Recommendations
- Refrain from answering unexpected calls from unknown contacts. When receiving unsolicited phone calls, do not respond to any requests for sensitive information or access.
- Avoid responding to messages, clicking links, or opening attachments from unknown or unverified senders, and exercise caution with emails from known senders.
- Confirm the legitimacy of requests by contacting the sender via a separate means of communication, such as by phone, using contact information obtained from official sources before responding, divulging sensitive information, or providing funds.
- Navigate directly to legitimate websites and verify before submitting account credentials or providing personal or financial information.
- Use strong, unique passwords and enable multi-factor authentication (MFA) where available, choosing authentication apps or hardware tokens over SMS text-based codes.
- Reduce your digital footprint so that threat actors cannot easily target you.
- Report malicious cyber activity to the FBI’s IC3 and the NJCCIC.