Bumblebee Resurrects After Losing its Stinger
Malware
October 24, 2024
A sophisticated malware loader known as Bumblebee has resurfaced after a law enforcement operation in May 2024 significantly disrupted its infrastructure. This operation, dubbed Operation Endgame, also targeted other malware families, including IcedID, Pikabot, Smokeloader, SystemBC, and Trickbot. The operation led to asset freezes, infrastructure shutdowns, and the public identification of eight suspects.
Bumblebee was discovered in March 2022 and was primarily used to deliver additional malware payloads. It vanished after the operation; however, analysts identified a new infection chain signaling a possible resurgence of Bumblebee.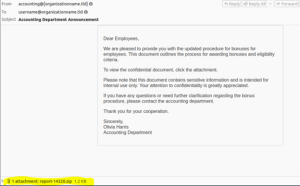
The new campaign distributes the malware through phishing emails that bait recipients into opening a ZIP archive containing an LNK file with names similar to “Report-#####.lnk.” When executed, this file initiates the download and execution of the Bumblebee payload in memory, bypassing the need to write the DLL to disk. The infection chain is automated, only requiring user interaction to run the LNK file. The MSI files that deliver the payload masquerade as Nvidia and Midjourney installers.
While previous attacks used legitimate binaries like rundll32.exe to load malicious DLLs, the current infection chain employs a more discreet technique via the SelfReg table. The DLL is contained in a CAB file named “disk1.” Once installation begins, it is loaded into the msiexec process address space, triggering the execution of the Bumblebee payload.
Recommendations
- Avoid clicking links, responding to, or otherwise acting on unsolicited emails.
- Use strong, unique passwords and enable multi-factor authentication (MFA) for all accounts where available, choosing authentication apps or hardware tokens over SMS text-based codes.
- Keep systems up to date and apply patches after appropriate testing.
- Implement cybersecurity best practices to reduce risk and increase resiliency to cyber threats.
- Utilize monitoring and detection solutions to identify suspicious login attempts and user behavior.
- Additional recommendations and indicators of compromise (IOCs) can be found in the NetSkope blog post and GitHub repository.