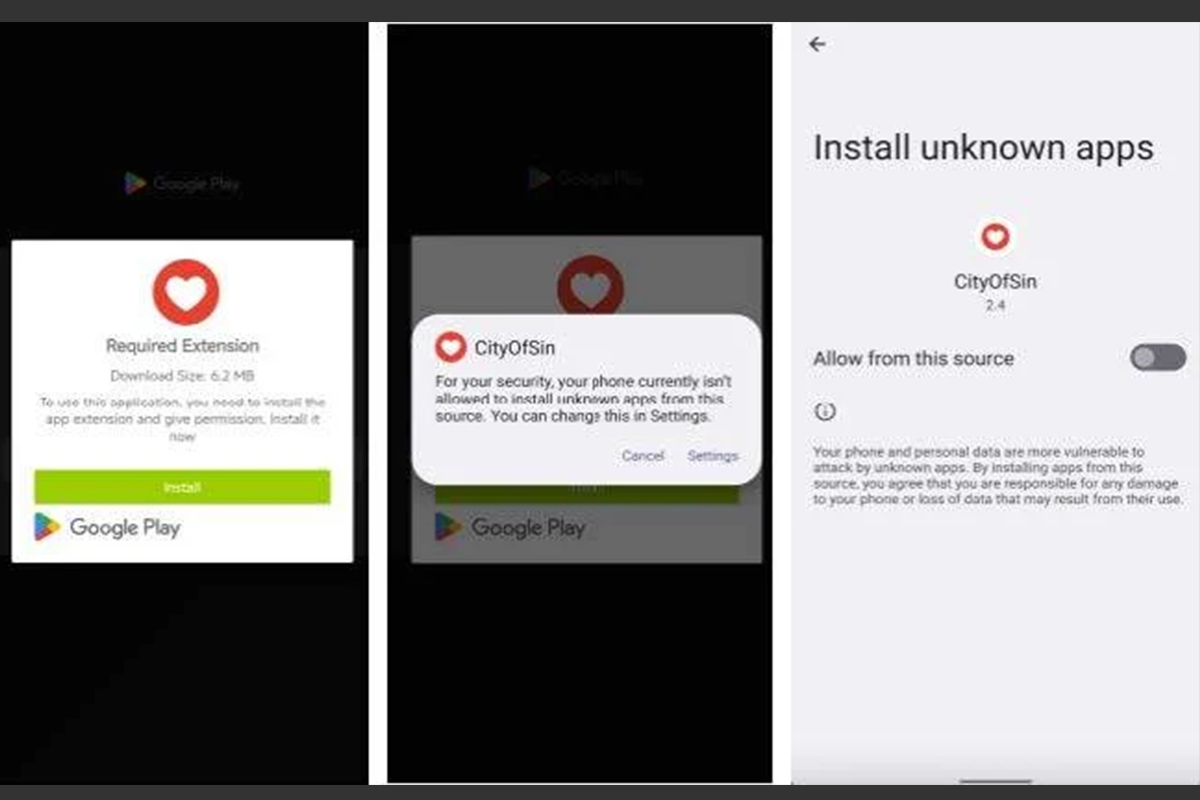
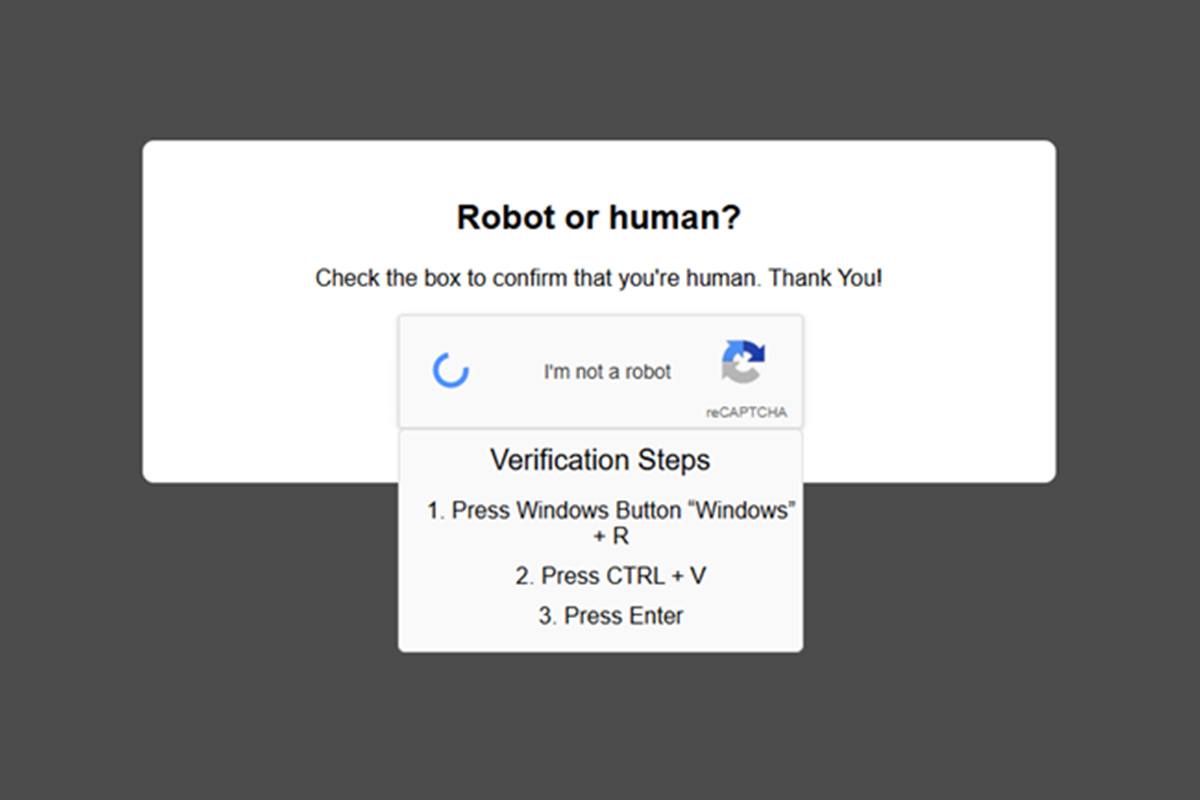
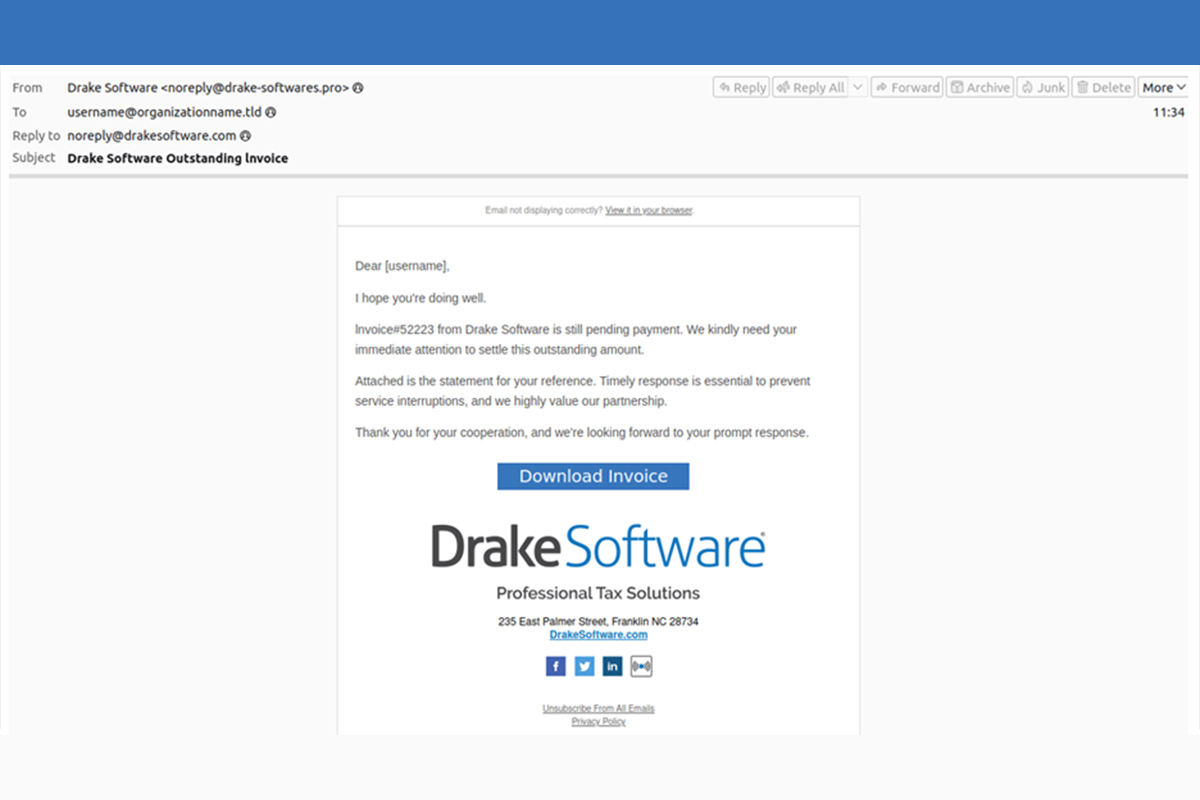
Discord Invites Used as a Path to Malware
Before 2015, few established Voice over Internet Protocol (VoIP) options existed. Skype and TeamSpeak were among the most common, but were limited in scale and became outdated. Around this time, Discord hit the market, becoming a cultural staple in online gaming communities.