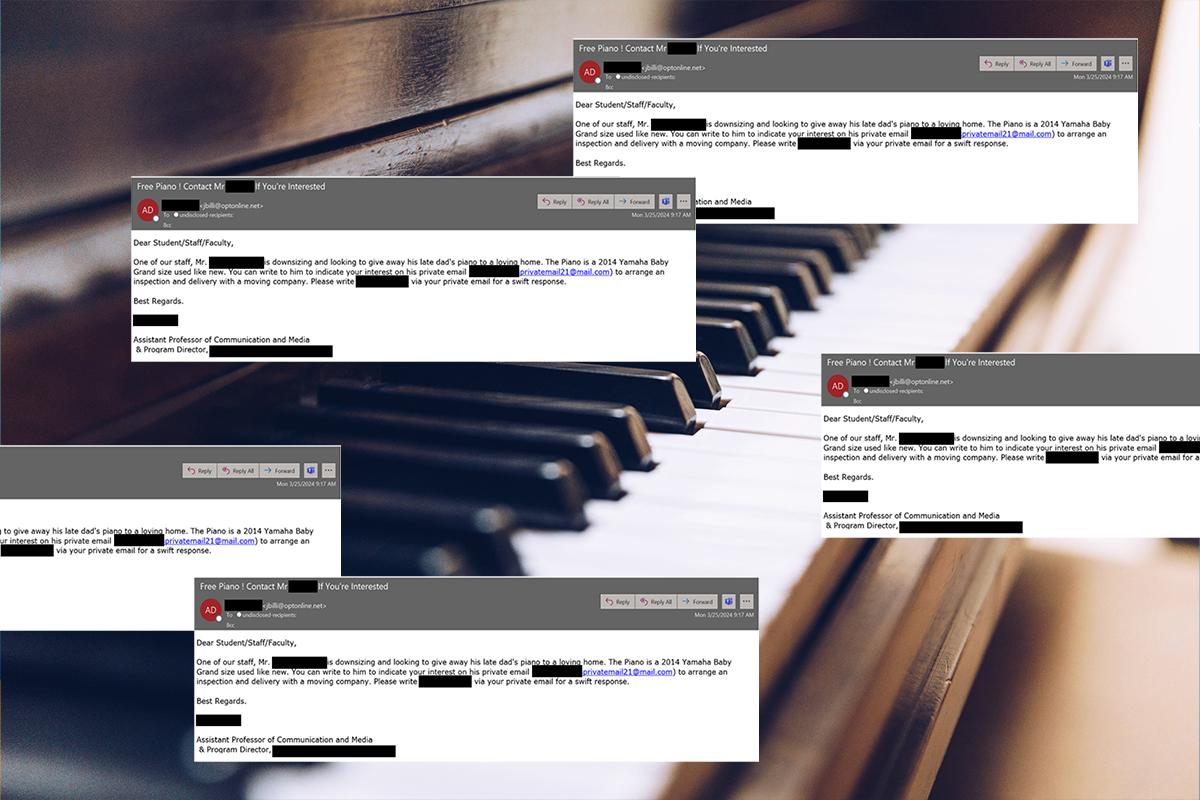
Uptick in Direct Deposit Scams
The NJCCIC recently received multiple incident reports from organizations targeted with direct deposit scams in an attempt to change bank account information for direct deposit payments for payroll to facilitate fraud. K-12 school districts are primarily targeted.