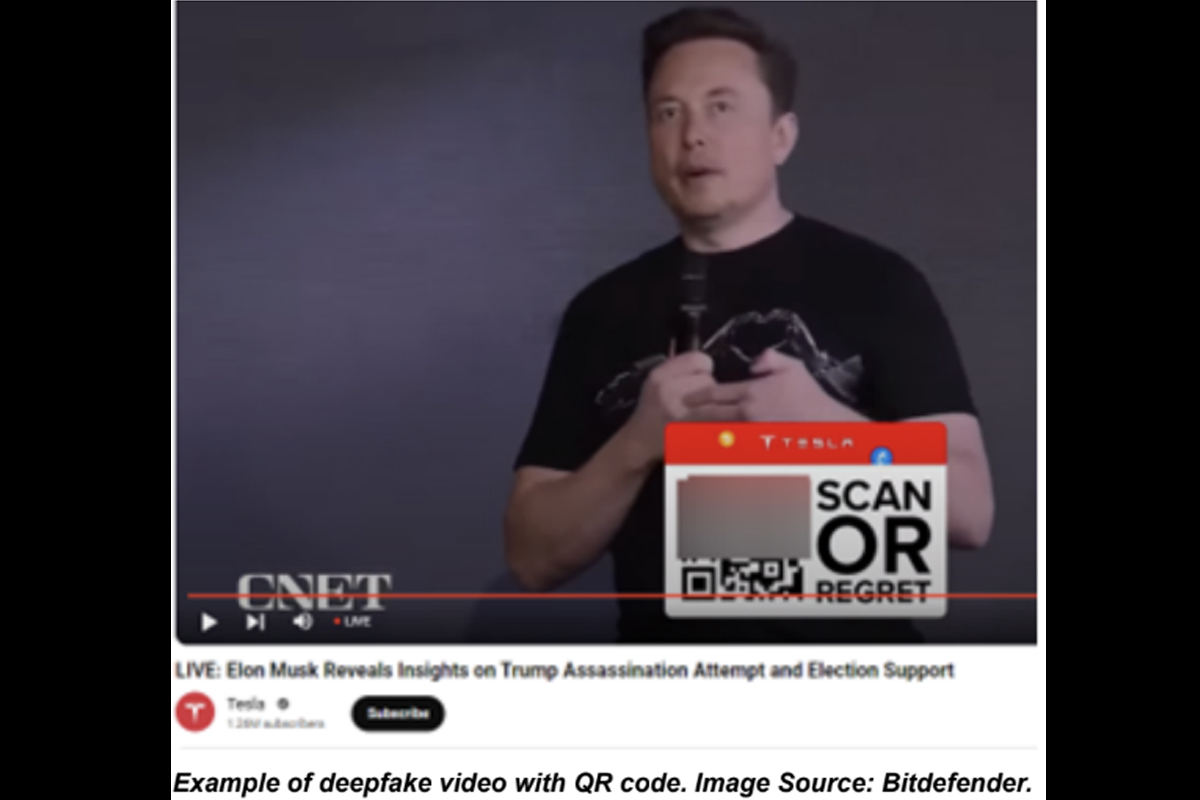
Cybercriminals Exploit Assassination Attempt
The NJCCIC recently received reports of cryptocurrency scams exploiting current events. Opportunistic cybercriminals are using the recent assassination attempt that targeted former President Donald Trump to lure unsuspecting victims into a new pig-butchering cryptocurrency scam.