Iranian Threat Group MuddyWater Rises
Global Attacks
July 18, 2024
While Chinese, North Korean, and Russian state-sponsored cyber threat activity has recently surged, MuddyWater, an Iranian threat group affiliated with the Ministry of Intelligence and Security (MOIS), has consistently targeted Israel and its allies with a barrage of cyberattacks since the onset of the Israeli-Hamas War. The threat group typically uses phishing campaigns, often sent from compromised business email accounts, to deploy legitimate Remote Management Tools (RMM) such as Screen Connect and Atera Agent. However, recent campaigns targeting Israel were observed delivering a new custom backdoor identified as BugSleep marking a notable change in TTPs. BugSleep appears to be in a perpetual development state, undergoing continuous improvement for functionality and bug fixes.
In addition, MuddyWater often uses Egnyte, a legitimate file-sharing service enabling organizations to conveniently share files via a web browser. They typically focus on specific sectors of interest, such as Israeli municipalities, airlines, travel agencies, and journalists; however, recent targets include the education, logistics, and healthcare sectors. Themes used in these campaigns include invitations to webinars and online courses allowing the threat actor to recycle the phishing template across different sectors and regions. The phishing emails are delivered to targets in the locally spoken language, though English is now used more frequently.
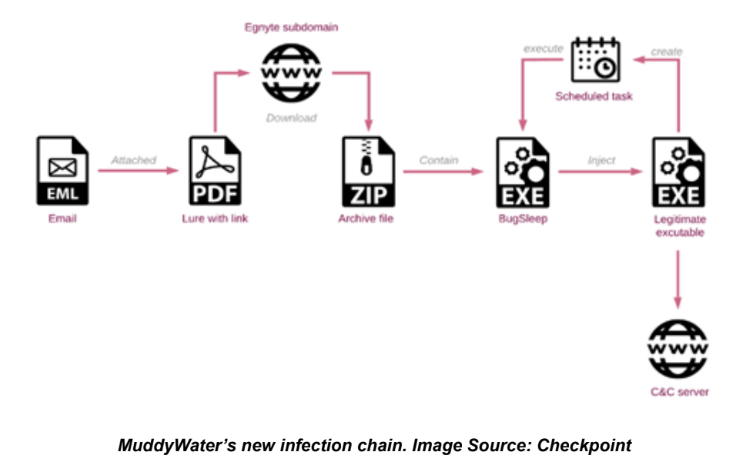
The malware can perform several commands to write, run, establish persistence, delete tasks, and other evasion techniques. One analyzed sample resulted in a custom loader that injects a shellcode to deliver BugSleep in-memory into specific processes. These processes include msedge.exe, opera.exe, chrome.exe, anydesk.exe, onedrive.exe, and powershell.exe, depending on whether they are already running. Cyberattacks using this new malware are targeting a wide range of global entities, with a particular focus on Israeli and Saudi Arabian targets. This Iranian threat group is highly active and has historically targeted various industry sectors worldwide, including telecommunications, government, IT services, and oil industry organizations. Over time, it has expanded its cyber-espionage operations to focus on governmental and defense institutions in Central and Southwest Asia, along with businesses in North America and Europe. Although MuddyWater is currently targeting Israel, the group often reuses newly developed and successfully tested malware to attack Western countries and Israeli allies.
Recommendations
- Avoid clicking links, responding to, or otherwise acting on unsolicited text messages or emails.
- Use strong, unique passwords for all accounts and enable multi-factor authentication (MFA) where available, choosing authentication apps or hardware tokens over SMS text-based codes.
- Keep systems up to date and apply patches after appropriate testing.
- Utilize monitoring and detection solutions to identify suspicious login attempts and user behavior.
- Implement email filtering solutions, such as spam filters, to help block messages.
- Employ a comprehensive data backup plan and ensure operational technology (OT) environments are segmented from the information technology (IT) environments.
- Cyber incidents can be reported to the FBI IC3 and the NJCCIC.