Chinese APT Salt Typhoon Targets ISPs
Global Attacks
October 3, 2024
A suspected Chinese (PRC) state-sponsored cyber threat group known as Salt Typhoon was recently identified accessing multiple United States internet service providers (ISPs) to conduct cyber espionage. This cyberattack is just the latest in a series of campaigns sponsored by the Chinese government. Salt Typhoon’s actions are part of a larger Chinese strategy to conduct cyber operations to gain access to other countries’ infrastructure for espionage and potential disruption. These attacks on ISPs are particularly concerning as they can be used to compromise sensitive communications, establish a foothold for future cyberattacks, and impact national security.
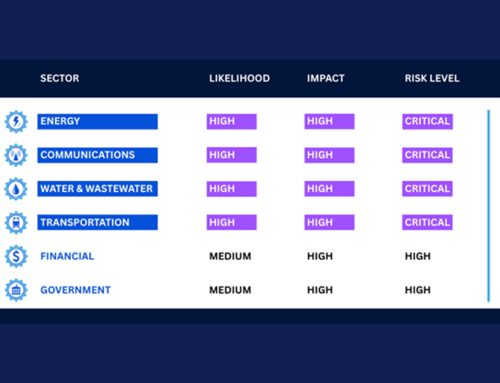
Previously, PRC state-sponsored cyber threat group Volt Typhoon was observed exploiting a zero-day vulnerability in Versa Director, a software platform used by ISPs and managed service providers (MSPs) to manage SD-WAN infrastructure. The Federal Bureau of Investigation (FBI) issued a joint cybersecurity advisory listing the group’s tactics, techniques, and procedures (TTPs). The advisory confirmed that Volt Typhoon compromised the IT environments of multiple critical infrastructure organizations, including those in the Communications, Energy, Transportation Systems, and Water and Wastewater Systems Sectors.
The FBI recently disrupted a portion of botnet infrastructure used by another PRC state-sponsored cyber threat group, Flax Typhoon. The botnet infrastructure contained hundreds of US-based small-office or home-office (SOHO) routers. The group commonly exploits vulnerabilities in networking appliances from companies such as Fortinet, Ivanti Connect Secure (formerly Pulse Secure), NETGEAR, Citrix, and Cisco to gain initial access. Salt Typhoon and Flax Typhoon likely use similar techniques for initial infections. One source indicated that Salt Typhoon may also be recognized as GhostEmperor and FamousSparrow, which historically targets government entities and telecommunications in Southeast Asia using a rootkit named Demodex.
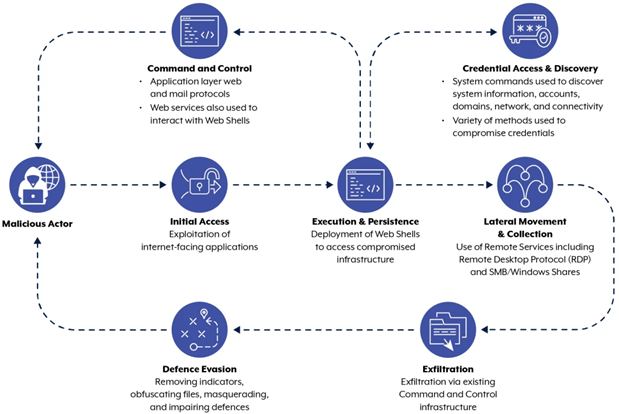
Current and former US intelligence officials have expressed serious concern regarding the bold nature and persistent use of cyber operations to infiltrate critical infrastructure networks. FBI Director Christopher Wray stated that the cyber threat posed by the Chinese government is immense. Analysts assess that there are strong indicators that recent Salt Typhoon activity may be linked to China’s Ministry of State Security, particularly APT40 (also known as Gingham Typhoon), a group known for its expertise in intelligence collection. Based on recent federal agency alerts regarding PRC state-sponsored cyber campaigns, China has escalated from surveillance-only goals toward installing offensive capabilities to disrupt critical US civilian and military infrastructure.
Recommendations
- Critical infrastructure administrators are encouraged to review analyses of recent state-sponsored cyber threat activity and apply recommendations to prevent victimization.
- Keep systems up to date and apply patches after appropriate testing.
- Utilize monitoring and detection solutions to identify suspicious login attempts and user behavior.
- Enforce the principle of least privilege, disable unused ports and services, and use web application firewalls (WAFs).
- Use strong, unique passwords for all accounts and enable MFA where available, choosing authentication apps or hardware tokens over SMS text-based codes.
- Employ a comprehensive data backup plan and ensure operational technology (OT) environments are segmented from information technology (IT) environments.
- Report cyber incidents to the FBI’s IC3 and the NJCCIC.