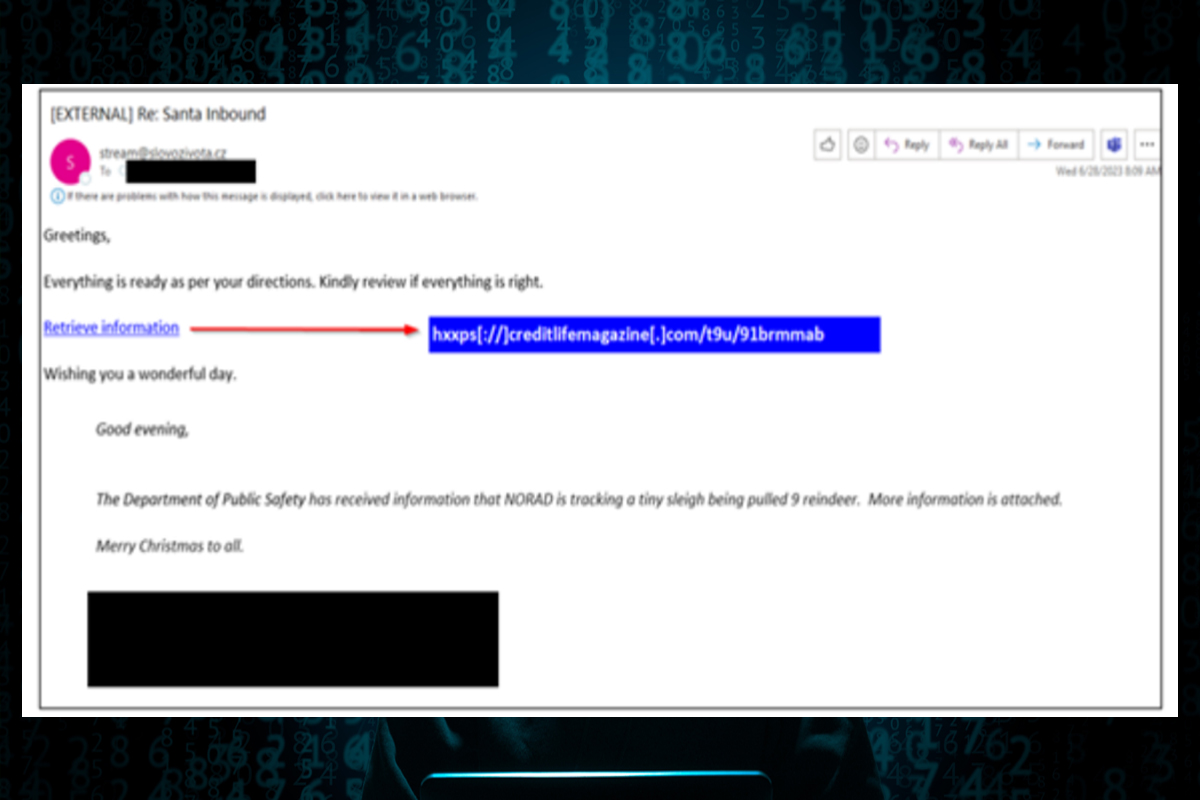
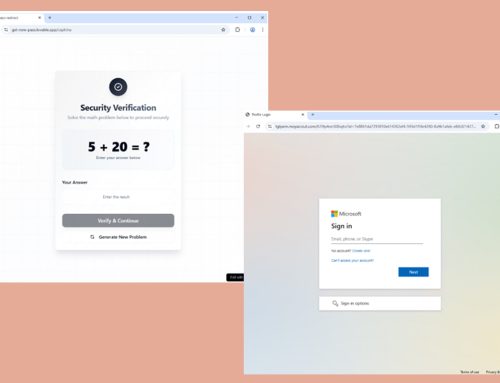
“Christmas in July” Phishing Campaign
Scams
July 6, 2023
Phishing emails remain a top social engineering tactic for cybercriminals. These emails may request recipients open an attachment, click a link, provide account credentials, transfer funds, or disclose sensitive information.
Phishing campaigns often impersonate known organizations, businesses, and individuals to convey a sense of legitimacy and convince targets to take a desired action (trick). In some cases, these email schemes claim recipients will receive rewards or assistance with their devices, or that they are helping to gift others (treat). Often, the emails that successfully pass through an email security gateway do not contain inherently malicious indicators, such as a link or attachment, and instead simply ask recipients to take an action. Examples of recent messages that attempted delivery to user inboxes can be found below.
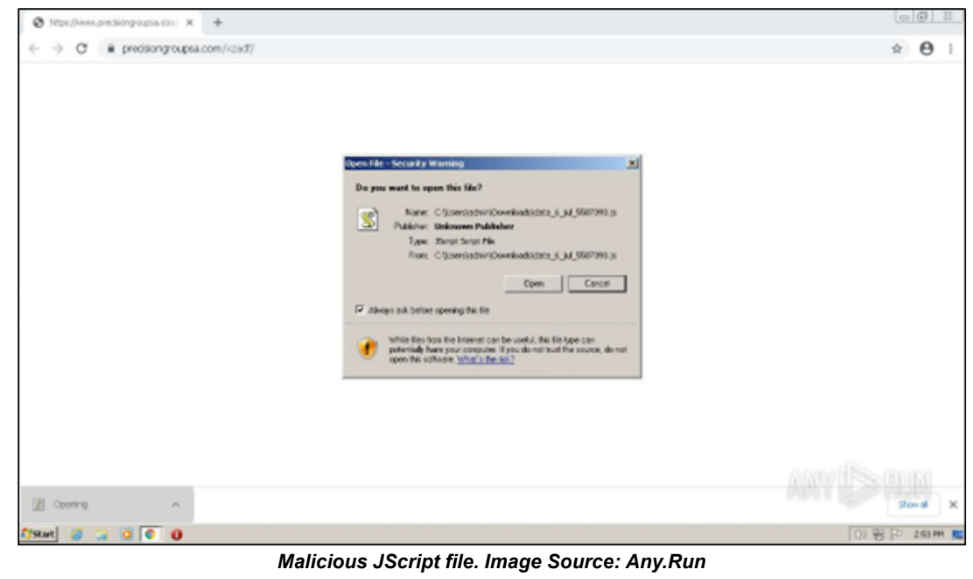
What Should I Do?
The NJCCIC advises users to ignore and delete these phishing emails, report the activity to their IT department if applicable, and avoid releasing these types of
correspondence to their inbox from a quarantined environment. Users are advised to refrain from responding to unsolicited communications, clicking links or opening attachments from unknown senders, and exercise caution with communications from known senders. If unsure of the legitimacy, contact the sender via a separate means of communication, such as by phone, before taking action. Phishing emails and other malicious cyber activity can be reported to the FBI’s Internet Crime Complaint Center ( IC3) and the NJCCIC.
Additionally, organizations are advised to implement filters at the email gateway to identify and block emails using known phishing tactics and those from suspicious IP addresses, create an email gateway rule to flag communications in which the “reply” email address is different from the “from” email address, and identify emails that originate outside their network by marking them with an “external email” tag in the subject and body since these emails should be given additional scrutiny. Furthermore, create a policy and procedure to identify and report business email compromise (BEC) scams, including periodic employee awareness training; establish policies and procedures that require any requests for highly sensitive information or large financial transactions be authorized and approved by multiple individuals via a secondary means of communication beyond email; and implement Domain-Based Message Authentication, Reporting, and Conformance (DMARC) to reduce the risk of email spoofing. For further information contact us here at Cyber Command.