ClickFix Imitates Problem and “Solution”
Individual Attacks
October 24, 2024
In June, the NJCCIC reported on a previous ClickFix campaign that used PowerShell scripts to drop malicious payloads. Recently, ClickFix was identified in two separate phishing campaigns. In one of these campaigns , the threat actors behind ClickFix hacked into over 6,000 WordPress sites to implant malicious plugins that display fake browser update prompts to users. Similar to the previous campaign, a malicious JavaScript file attempts to load the forged update prompt when the compromised website is loaded. This malicious file is stored using Binance Smart Chain (BSC) contract. If the end user follows the instructions from the prompt, info-stealing malware will be loaded and installed onto their device.
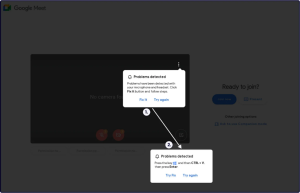
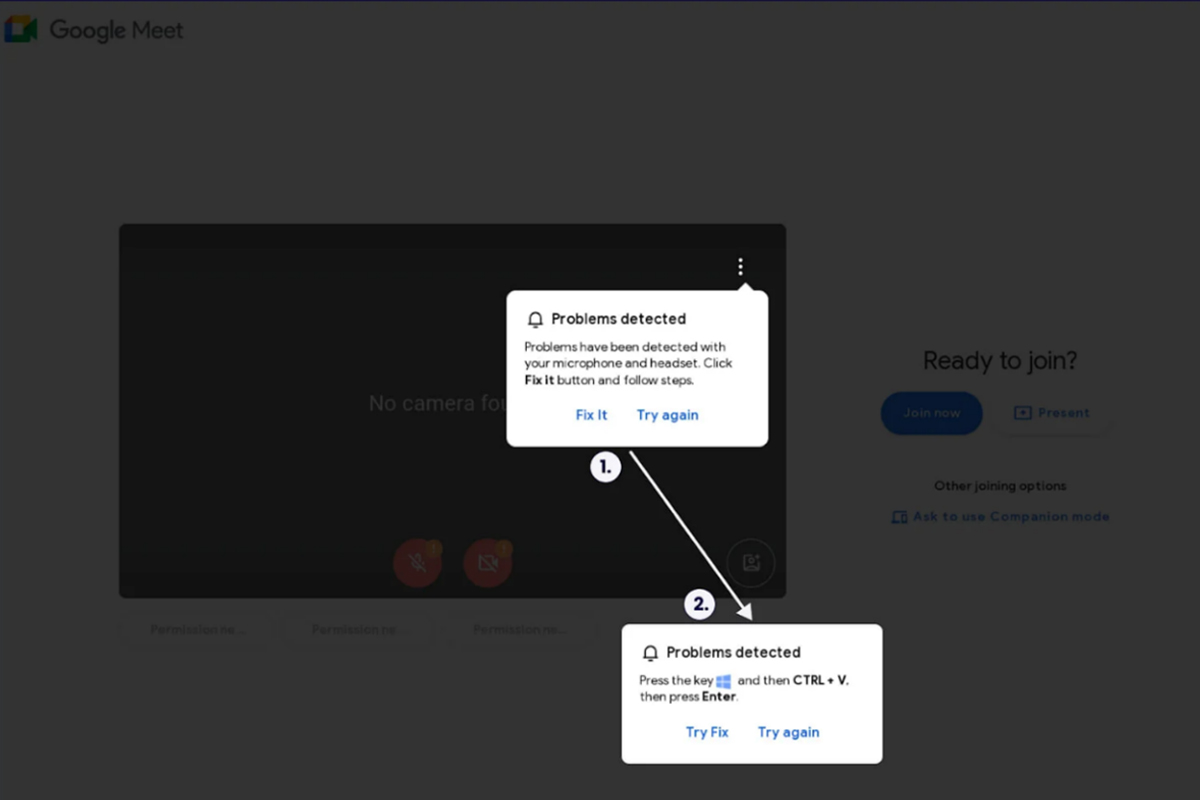
In the other campaign, Clickfix was observed posing as a Google Meet conference page. This fake page displays an error message claiming there is a technical issue and offers a fix. If a user clicks the “Fix It” button, they are led to a second pop-up with the option to “Try Fix” or “Try Again.” If a user selects “Try Fix,” a command will be copied to the user’s clipboard, which the user is instructed to paste into the Windows command line. If the script is executed, the following actions occur:
- The parent process (mshta.exe) is terminated.
- The executables for Stealc and Rhadamanthys malware are downloaded. After a two-second delay, the command and control (C2) server is notified if the executables have successfully run.
- The victim’s public IP address is retrieved and sent to the C2 server along with the execution status.
Recommendations
- Avoid clicking links and opening attachments in unsolicited emails.
- Confirm requests from senders via contact information obtained from verified and official sources.
- Type official website URLs into browsers manually.
- Facilitate user awareness training to include these types of phishing-based techniques.
- Maintain robust and up-to-date endpoint detection tools on every endpoint.
- Consider leveraging behavior-based detection tools rather than signature-based tools.
- Phishing and other malicious cyber activity can be reported to the FBI’s IC3 and the NJCCIC.