ClickFix Leading to MonsterV2 Infostealer
Scams
July 17, 2025
The NJCCIC observed a new iteration of ClickFix leading to the download of a recently discovered infostealer, MonsterV2. This infostealer can grab cryptocurrency wallets, account credentials, personally identifiable information such as Social Security numbers, and browser information.
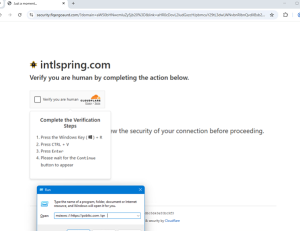
The ClickFix phishing campaign sends users an email claiming they must confirm their identity to maintain access to their email account. After clicking the link, the threat actors attempt to trick the user into running a malicious script on a compromised legitimate website. On website load, the malicious injection causes a script to run that forces an overlay to appear on the infected website. The overlay shows a fake CAPTCHA that states the user needs to complete the required verification steps in order to proceed:

Following these instructions begins the download and installation of Monsterv2. Similar to previous campaigns, this can also lead to secondary payloads, including StealC and Rhadamanthys.
Recommendations
- Exercise caution while online, verifying any unusual requests or instructions.
- Facilitate user awareness training to include these types of social engineering-based techniques.
- Maintain robust and up-to-date endpoint detection tools on every endpoint.
- Confirm requests from senders via contact information obtained from verified and official sources.
- Social engineering and other malicious cyber activity can be reported to the NJCCIC and the FBI’s IC3.





