Credential Stealing by Locking Browsers
Google,Scams
September 19, 2024
Security researchers have discovered a new campaign to steal a user’s login account credentials. In this campaign, a target’s browser is forced to load in kiosk mode, a full-screen mode that prevents users from navigating away from the selected webpage. While this campaign affects many browsers, it targets Google login account credentials.
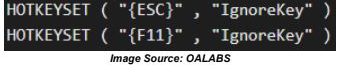
The attack chain in this campaign begins when a device becomes infected by Amadey malware. Once the system is infected, Amadey loads Stealc and deploys an AutoIt script to run a credential flusher that launches the system’s preferred browser in kiosk mode and loads a specific website. This script also blocks the ESC and F11 keyboard shortcuts, forcing users to submit their credentials to navigate out of kiosk mode. If users enter their credentials on the provided login page, Stealc will capture them from the browser’s credential store and deliver the stolen information to the threat actors.
There are several recommended options to escape kiosk mode. Users can try other keyboard shortcuts, such as Alt + F4, Ctrl + Shift + Esc, and Alt +Tab. Users can also terminate the browser by opening the Task Manager using Ctrl + Alt +Delete and selecting the End Task option. If these options are unsuccessful, researchers suggest pressing the Win + R keys to open the Run command, typing “cmd” to open the command prompt, and entering “taskkill /IM chrome.exe /F” to terminate the open instance of the Chrome browser. If the above options are unsuccessful, rebooting is suggested as a fail-safe. To mitigate continued infection, users can press the F8 key during boot, select Safe Mode, and run a full anti-virus scan once the system has finished loading to remove the malware.
Recommendations
- Implement cybersecurity best practices to reduce risk and increase resiliency to cyber threats.
- Facilitate user awareness training to include these types of phishing-based techniques.
- Maintain robust and up-to-date endpoint detection tools on every endpoint.
- Consider leveraging behavior-based detection tools rather than signature-based tools.
- Report malicious activity to the FBI’s IC3 and the NJCCIC.





