Credential-Stealing Phishing with Dropbox
Scams
March 16, 2023
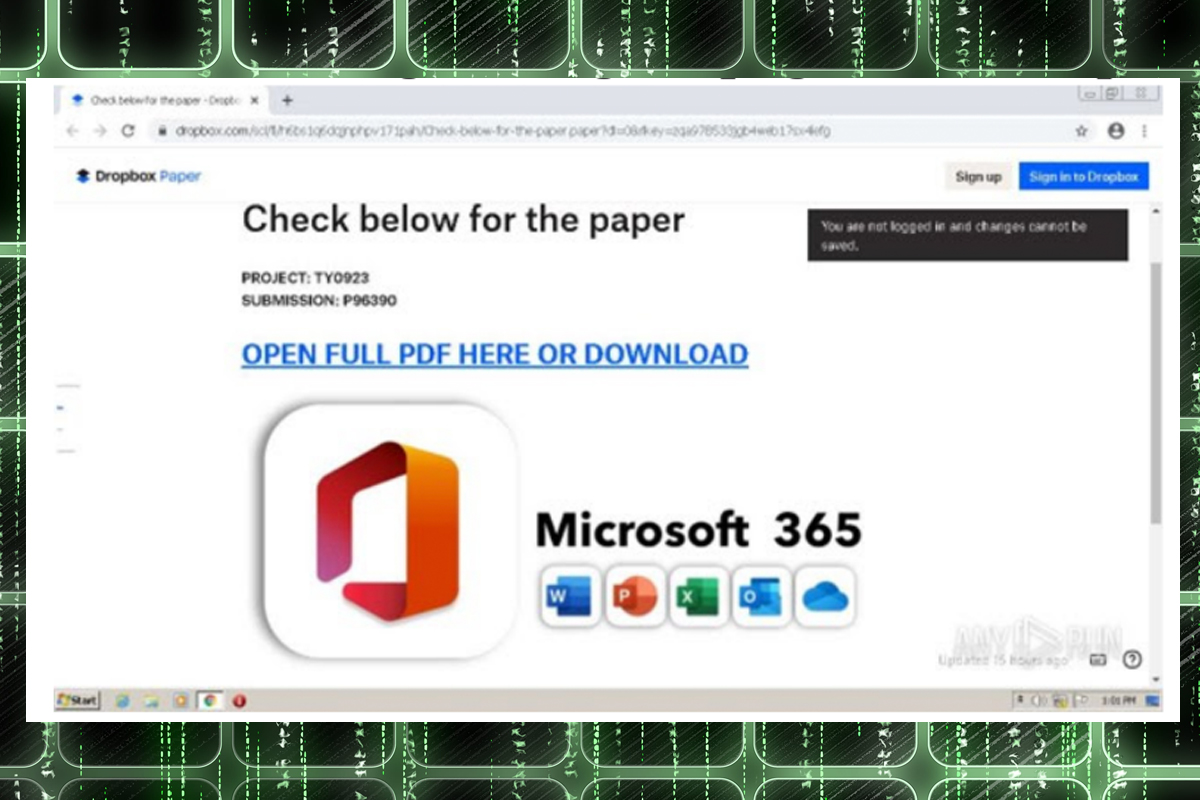
On March 14, the NJCCIC observed a phishing campaign utilizing a legitimate file-sharing platform and URL redirects to steal user credentials. In this scheme, the email includes a Dropbox link to view a document; however, this link redirects users to a known phishing page, hxxps://trabosky002-secondary[.]z13[.]web[.]core[.]windows[.]net, which impersonates OneDrive and prompts the user to provide their email address and password to view the file.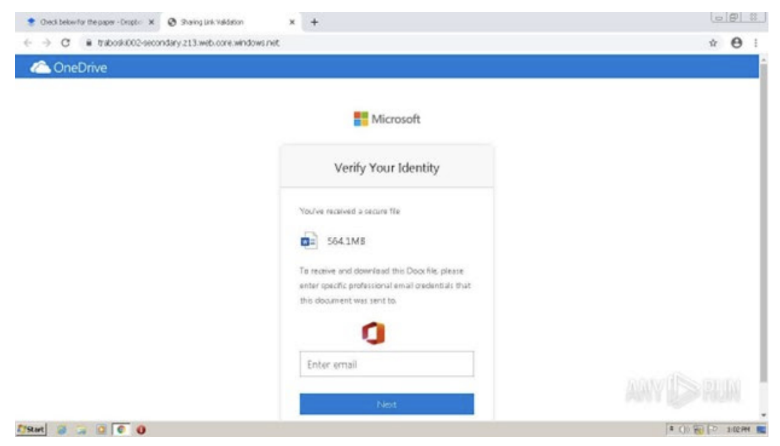
The cyber threat actors behind the campaign collect user account credentials submitted on the fraudulent webpage to facilitate subsequent cyber threat activity. This campaign was distributed using a compromised account belonging to a New Jersey healthcare organization. Attempts to steal account credentials may be more successful, as the recipients believed the communication came from a known and trusted sender. Additionally, the use of a legitimate service such as Dropbox lends a sense of credibility to the scheme.
The NJCCIC advises against clicking on links in unexpected emails from unverified senders. Users are encouraged to verify that a website is legitimate before entering account information and remain cautious even if an email is sent from a known or trusted account. Threat actors can use legitimate services like Dropbox to present a false sense of legitimacy and forward victims to phishing websites or other malicious payloads. If a suspicious email appears to originate from a legitimate sender, confirm its authenticity with the sender via another form of communication, such as by phone. If account credentials are submitted on a fraudulent website, users are advised to change their password and enable multi-factor authentication (MFA). Additionally, phishing emails and other malicious cyber activity can be reported to the FBI Internet Crime Complaint Center (IC3) and the NJCCIC.