Cryptocurrency Theft on the Rise
Scams
September 12, 2024
The NJCCIC received incident reports consistent with open-source reporting that indicate an overall increase in various types of cryptocurrency scams. Cryptocurrency’s decentralized nature and its global transferability make it appealing to cybercriminals, leading to its prevalent use in fraudulent investment scams. In 2023, the Federal Bureau of Investigation’s Internet Crime Complaint Center (IC3) received over 69,000 complaints regarding financial fraud and cryptocurrency, with reported losses totaling more than $5.6 billion. This marked a 45 percent increase in cryptocurrency-related scams since 2022. Investment scams accounted for almost 71 percent of all cryptocurrency-related losses. Additionally, deceptive practices in investment fraud schemes led to a 53 percent increase in reported losses from $2.57 billion in 2022 to $3.96 billion in 2023.
State-Sponsored Cyber Threats
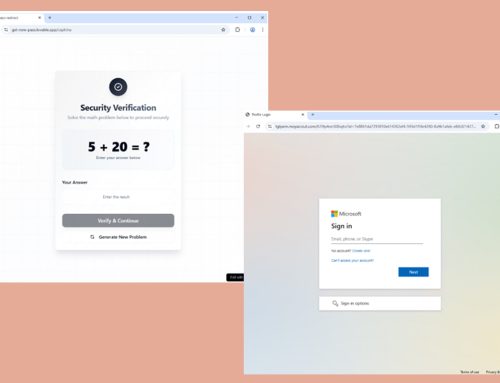
The IC3 also released a public service announcement (PSA) regarding North Korean (DPRK) cybercriminals conducting highly tailored, difficult-to-detect social engineering campaigns. These campaigns target employees of decentralized finance (DeFi), cryptocurrency, and similar businesses to gain unauthorized access to the businesses’ networks, deploy malware, and steal company cryptocurrency. Before reaching out, the cybercriminals examine potential targets by monitoring their activity on social media, especially on professional networking or employment-related platforms. They use personal information about a target’s background, skills, employment, or business interests to create tailored fictional scenarios to attract the targeted individual. These schemes often involve offers of new job opportunities or corporate investments and may mention personal details, such as interests, personal relationships, and professional connections, to engage the potential victims in extended conversations to build trust and deploy malware.
These cybercriminals often communicate with victims in fluent or near-fluent English and possess a strong understanding of the technical aspects of the cryptocurrency industry. They frequently impersonate various individuals, including contacts, general recruiters, or influential figures associated with specific technologies. To boost the authenticity of their impersonations, the cybercriminals use realistic images, including photographs taken from public social media profiles of the impersonated individual. Additionally, they may use fake imagery of time-sensitive events to prompt immediate responses from their intended victims. The cybercriminals also impersonate recruitment agencies or tech companies by creating professional websites to make the fictitious entities appear legitimate.
Other Notable Scams
Fraudulent activities targeting Bitcoin ATMs, also known as BTMs, have increased, resulting in substantial financial losses. Data from the Federal Trade Commission (FTC) Consumer Sentinel Network revealed over $65 million in fraud losses at BTMs in the first half of 2024, nearly ten times higher than from 2020 to 2023. Notably, these figures likely represent only a fraction of the actual losses, as many fraud incidents are not reported.
The widespread accessibility of BTMs has facilitated the use of cryptocurrency in various scam activities, with government impersonation, business impersonation, and tech support scams being the most prevalent reported schemes associated with BTMs. Notably, individuals aged 60 and above have been disproportionately affected by fraudulent activities using BTMs, reporting losses at a rate more than three times that of younger adults.
Scams involving BTMs often commence with communications related to alleged unauthorized account activities or deceptive security warnings, compelling individuals to take immediate action. Subsequently, these scams evolve into coercing victims to deposit funds into BTMs to safeguard their assets or rectify fabricated issues. The process typically involves instructing individuals to withdraw cash from their bank accounts and deposit it into specific BTM locations using provided QR codes, ultimately transferring funds into the scammers’ possession.
Recommendations
- The NJCCIC recommends users educate themselves and others on this and similar scams to prevent future victimization.
- Avoid clicking links, responding to, or otherwise acting on unsolicited text messages or emails.
- Users can search for and report the bitcoin addresses included in the scam email to the Chainabuse Database.
- Protect your digital assets by refraining from sending funds or installing wallets through unverified websites.
- Refrain from providing sensitive information—including your seed phrase or passphrase—to any entity requesting it, including websites, apps, giveaways, and browser extensions.
- Avoid storing the seed phrase online, entering it into any online applications without due diligence, or losing the recovery seed.
- Use strong, unique passwords and enable MFA for all accounts where available, choosing authentication apps or hardware tokens over SMS text-based codes.
- Only download applications from reputable sources.
- These scams can be reported to the Federal Trade Commission (FTC), the FBI’s IC3 and the NJCCIC.
The FBI recommends the following best practices to lower the risk from DPRK’s social engineering attempts:
- During the hiring process, consider developing unique methods to verify a contact’s identity using separate, unconnected communication platforms.
- Do not store any information regarding cryptocurrency wallets, such as logins, passwords, wallet IDs, seed phrases, and private keys, on Internet-connected devices.
- Avoid taking pre-employment tests or executing code on company owned laptops or devices. If a pre-employment test requires code execution, insist on using a virtual machine on a non-company connected device, or on a device provided by the tester.
- Require multiple factors of authentication and approvals from several different unconnected networks prior to any movement of your company’s financial assets. Regularly rotate and perform security checks on devices and networks involved in this authentication and approval process.
- Limit access to sensitive network documentation, business or product development pipelines, and company code repositories.
- Funnel business communications to closed platforms and require authentication — ideally in person — before adding anyone to the internal platform. Regularly reauthenticate employees not seen in person.
- For companies with access to large quantities of cryptocurrency, the FBI recommends blocking devices connected to the company’s network from downloading or executing files except specific whitelisted programs and disabling email attachments by default.
If you suspect you or your company have been impacted by a social engineering campaign similar to those discussed in this announcement, or by any potential DPRK-related incident, the FBI recommends the following actions:
- Disconnect the impacted device or devices from the Internet immediately. Leave impacted devices powered on to avoid the possibility of losing access to recoverable malware artifacts.
- File a detailed complaint through the FBI Internet Crime Complaint Center (IC3) at www.ic3.gov.
- Provide law enforcement as many details as you can regarding the incident, including screenshots of communications with the malicious cyber actors. If possible, take screenshots of (or otherwise save) identifiers, usernames, online accounts, and any other details about the actors involved.
- Discuss options for incident response and forensic examination of impacted devices with law enforcement. In some situations, law enforcement may recommend taking advantage of private incident response companies.
The FTC provides the following recommendations to avoid BTM scams:
- Share your experience with colleagues, if appropriate, to raise awareness and broaden the public’s understanding of the significant malicious cyber threat emanating from North Korea.
- Never click on links or respond directly to unexpected calls, messages, or computer pop-ups. If you think it could be legit, contact the company or agency, but look up their number or website yourself. Don’t use the one the caller or message gave you.
- Slow down. Scammers want to rush you, so stop and check it out. Before you do anything else, talk with someone you trust.
- Never withdraw cash in response to an unexpected call or message. Only scammers will tell you to do that.
- Don’t believe anyone who says you need to use a Bitcoin ATM, buy gift cards, or move money to protect it or fix a problem. Real businesses and government agencies will never do that – and anyone who asks is a scammer.
- Additional recommendations to avoid scams can be found at ftc.gov/scams. Report scams to the FTC at ReportFraud.ftc.gov.