Discord Invites Used as a Path to Malware
Before 2015, few established Voice over Internet Protocol (VoIP) options existed. Skype and TeamSpeak were among the most common, but were limited in scale and became outdated. Around this time, Discord hit the market, becoming a cultural staple in online gaming communities for its large-scale server-based model that hosts hundreds of users simultaneously. When the COVID-19 pandemic struck and Discord’s popularity increased by millions , sitting amongst Zoom, Teams, and Meet, its target demographic widened from gaming to a broad range of diverse communities and businesses. With over 200 million monthly active users and nearly 30 million servers, Discord’s wealth of stakeholders became targets of malicious cyber threat actors.
Invite Links
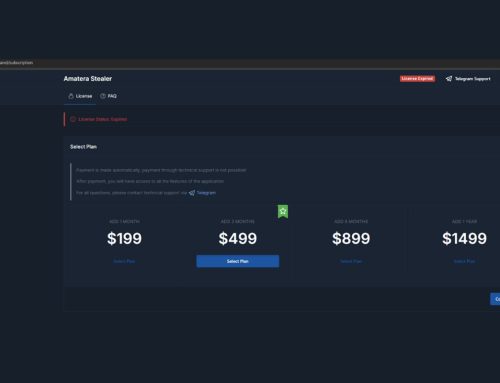
Check Point Research discovered an active malware campaign exploiting Discord’s server invitation links. Typically, when joining a Discord server, the system randomly generates a link with a string of letters and numbers at the end denoting the server-specific invite code. These links can be set to expire in a custom amount of time set upon creation, ranging from thirty minutes up to never expiring until manually deleted. Invite links that inevitably expire or have been removed by server admins can then be utilized by threat actors to phish credentials and deliver malware.
Discord utilizes a “Boost” system in servers to generate additional income and increase user engagement by allowing users to upgrade a server up to Level 3 through payments. Each tier unlocks new options for the server, one of which is custom vanity invite links. With this, administrators can create a custom invite link code specialized to their server instead of generating a random code.
Threat actors can use expired or deleted links previously directed to legitimate servers for communities and businesses to now point to malicious servers. Threat actors would still need their server to be at a Level 3 Boost to set the custom invite code, which is the targeted server’s expired code. For example, if a server’s invite link is hc59xz09 and then expired after its chosen time, a threat actor would create a new server, set it up to look convincingly like the server it was formerly used in, then use that old code in a new way. For organizations that left server invites scattered around their websites and social media, those expired links may now forward unsuspecting users to a threat actor’s server.
The first variation of this attack relates to invite links with lowercase letters. Attackers cannot register these codes as vanity codes to trick users. Instead, proactive threat actors who find an expired or deleted link can then create their own for use. Anyone who interacts with the old code will be redirected.
If an authentic invite code includes uppercase letters, attackers using their Level 3 Boost custom vanity invite can create the same code in a lowercase version. When the original code expires, users will be redirected to the lowercase version. If the original is deleted before the expiration time set, it will continue to be active until then.
If either of these is successful, an unsuspecting user is redirected to the malicious actor’s server and the next stages of malware attack begins.
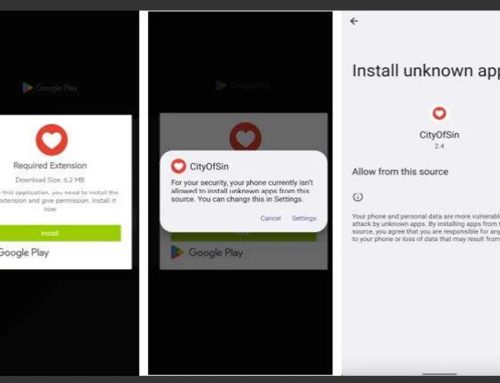
Discord servers often have custom scripted bots for auto-moderation, user verification, and scheduling events. If a user were to click on a link from a trusted source but was led to a fake channel, Check Point has identified that a Safeguard bot would prompt users to verify their account to gain access to the server. If the user proceeds, their Discord information is accessed and they are brought to a phishing website disguised as a mimic of Discord’s user interface that includes next steps. Discord has taken action to disable the bot used in this campaign; however, malicious actors could utilize the same techniques and create new delivery methods or bots.
Recommendations
- Exercise caution when clicking invitation links from known and unknown senders.
- Confirm the source is legitimate before clicking on any URLs.
- If the server is public, search for it manually through Discord’s server finder.
- Avoid clicking server links from old social media posts.
- Keep Discord, systems, and browsers updated.
- When prompted, thoroughly check the requested permissions from Discord bots.
- Verify the legitimacy of all Discord bots and avoid accepting permissions.
- Report malicious cyber activity to the NJCCIC and the FBI’s IC3.