Emotet Activity Returns
Malware,Scams
March 16, 2023
Emotet has resurfaced worldwide after three months of inactivity. Cofense researchers discovered malicious email campaigns using finance and invoice lures to collect information for future campaigns, gain remote access, deploy ransomware, and exfiltrate data. Additionally, the threat actors – known as initial access brokers – are targeting high-value corporate networks to infiltrate and sell access to ransomware groups. The NJCCIC observed phishing campaigns attempting to deliver Emotet sent from non-US top-level domains (TLD). The emails appear to be new messages or replies to conversation threads and contain a zipped Microsoft Word document that is not password-protected. The document requests the user to enable macros, a technique many threat actors no longer use due to Microsoft disabling macros by default in July 2022. If the file is unzipped and macros are enabled, the document downloads a compressed Emotet DLL file from compromised sites, primarily made up of hacked WordPress blogs. The initial attack file and the final payload are artific
ially inflated to more than 500 MB in size to avoid detection. This technique may cause serious performance issues or result in failed detections for some security vendor products when scanning these large files for malicious activity.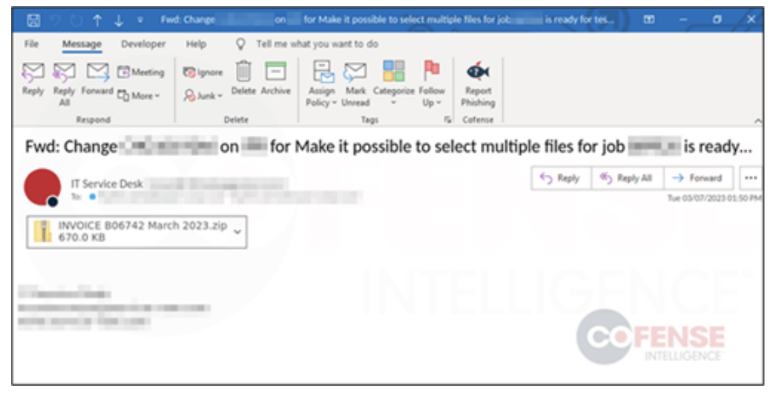
The NJCCIC recommends users and organizations educate themselves and others on these continuing threats and tactics to reduce victimization. Users are advised to refrain from responding to unsolicited communications, clicking links or opening attachments from unknown senders, and exercise caution with communications from known senders. If unsure of the legitimacy, contact the sender via a separate means of communication, such as by phone, before taking action.