Fake Updates Distribute Malware
Google,Malware
November 9, 2023
A good cybersecurity best practice is to stay informed of publicly disclosed vulnerabilities and to update all device hardware, operating systems, applications, software, and anti-virus or anti-malware programs. These patches address performance flaws and security vulnerabilities within a program or product that threat actors could exploit to gain unauthorized access to devices and data. Software vendors may offer users the option to either automatically check for updates and install or configure the software files, or manually download and install them. Capitalizing on this, threat actors use social engineering to convince their target to take action to download and install fake updates that ultimately distribute malware.
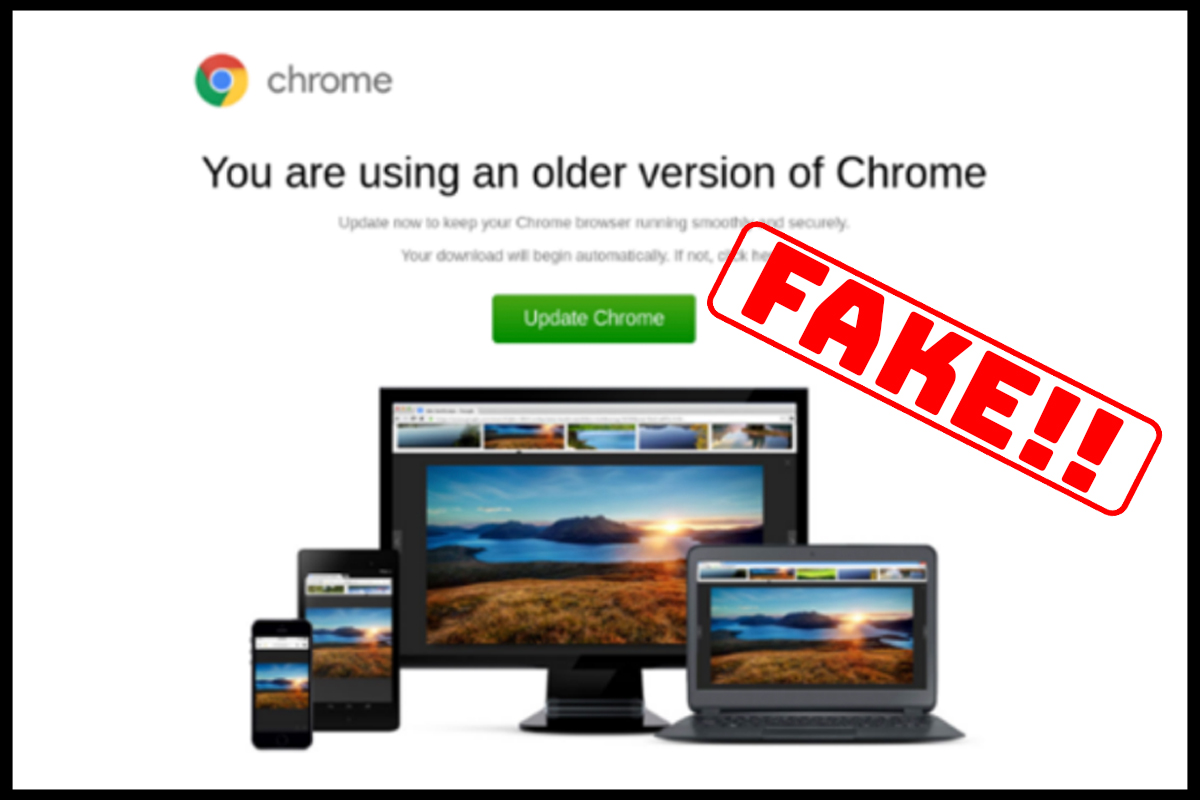
Over the past month, the NJCCIC has continued to observe multiple malware campaigns containing URLs leading to websites compromised with malicious HTML injections and presenting fake update notices. The emails, URLs, and domains appear legitimate; however, they are routing traffic maliciously. For example, SocGholish is a malware loader that exploits vulnerable website infrastructure and executes a series of logic checks to determine if the target is eligible for the payload based on the geolocation, operating system, IP address, browser, and other tracking variables. If eligible, it will redirect users to a landing page (see above image) displaying a fake browser update notice of “You are using an older version of Chrome.” If the update button is clicked, it will attempt to download a JavaScript file containing SocGholish malware. SocGholish can perform reconnaissance and deploy malicious payloads, such as remote access trojans (RATs), information stealers, and ransomware.
Similar to SocGholish, ClearFake is another malware campaign observed with fake update lures. The messages contain URLs leading to compromised websites that filter and redirect targets to a landing page displaying a fraudulent browser update notice: “You need to update your browser to view the content!” The lure is displayed in the language consistent with the browser’s display language settings. If the update button is clicked, it will download an executable file that, if launched, will install Lumma Stealer in the background. Lumma Stealer is an information stealer capable of stealing passwords, MFA data, configuration data, cryptocurrency wallet data from browsers, and more.
ZPHP is another malware campaign with messages containing URLs directing users to compromised websites and displaying “You are using an old version of Chrome” fake browser update notices. The injected code filters and redirects traffic to threat actor- controlled domains to deliver the malicious payload. This ZPHP campaign has been observed delivering NetSupport, which is a legitimate remote access tool often exploited by
threat actors using custom configurations. RogueRaticate is a similar malware campaign displaying “There’s no place like Chrome” fake browser update notices. If the update button is clicked, it will download and execute a Windows installer or JavaScript file that installs DarkGate malware. DarkGate is used to steal information, download additional payloads, and more.
The NJCCIC recommends organizations and users educate themselves and others on these continuing threats and tactics to reduce victimization. Users and administrators are advised to enable automatic updates whenever possible to ensure they are installed as quickly as possible or download updates from verified and trusted sources and install them after appropriate testing. Additionally, visit websites directly by manually typing the legitimate URL into a browser and refrain from navigating to online platforms or providing sensitive information via emailed links. Lastly, refrain from responding to unsolicited communications, clicking links, or opening attachments from unknown senders, and exercise caution with known senders. If unsure of a message’s legitimacy, contact the sender via a separate means of communication, such as by phone, before taking action.