FlowerStorm Phishing Platform
Scams
December 26, 2024
After the quick rise and fall of the Rockstar2FA Phishing-as-a-Service (PhaaS) platform, a new phishing platform, dubbed FlowerStorm, was observed filling in the gap left behind in Rockstar’s absence. Rockstar2FA platform had a simple interface that utilized adversary-in-the-middle (AiTM) techniques to allow threat actors to attempt to bypass the two-factor authentication (2FA) of Microsoft 365 accounts by stealing session cookies during a user’s login session. These stolen session cookies allowed threat actors to access user accounts without needing the user’s credentials or codes.
While the two platforms have not definitively been connected, researchers have found enough similarities between the two that suggest a common ancestry. First seen in June 2024, FlowerStorm shares many similar traits as Rockstar2FA, including:
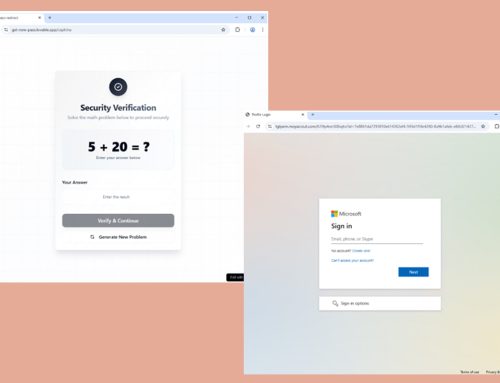
- Platforms utilize phishing portals that mimic legitimate login pages.
- The HTML structure of their phishing pages is highly similar. While the theming had notable differences (automotive vs. botanical), the underlying design structure remained consistent.
- Credential harvesting methods align closely and support email validation and MFA authentication through their backend.
- Platforms utilize similar domain registration and hosting habits, mainly using .ru and .com top-level domains and Cloudflare services.
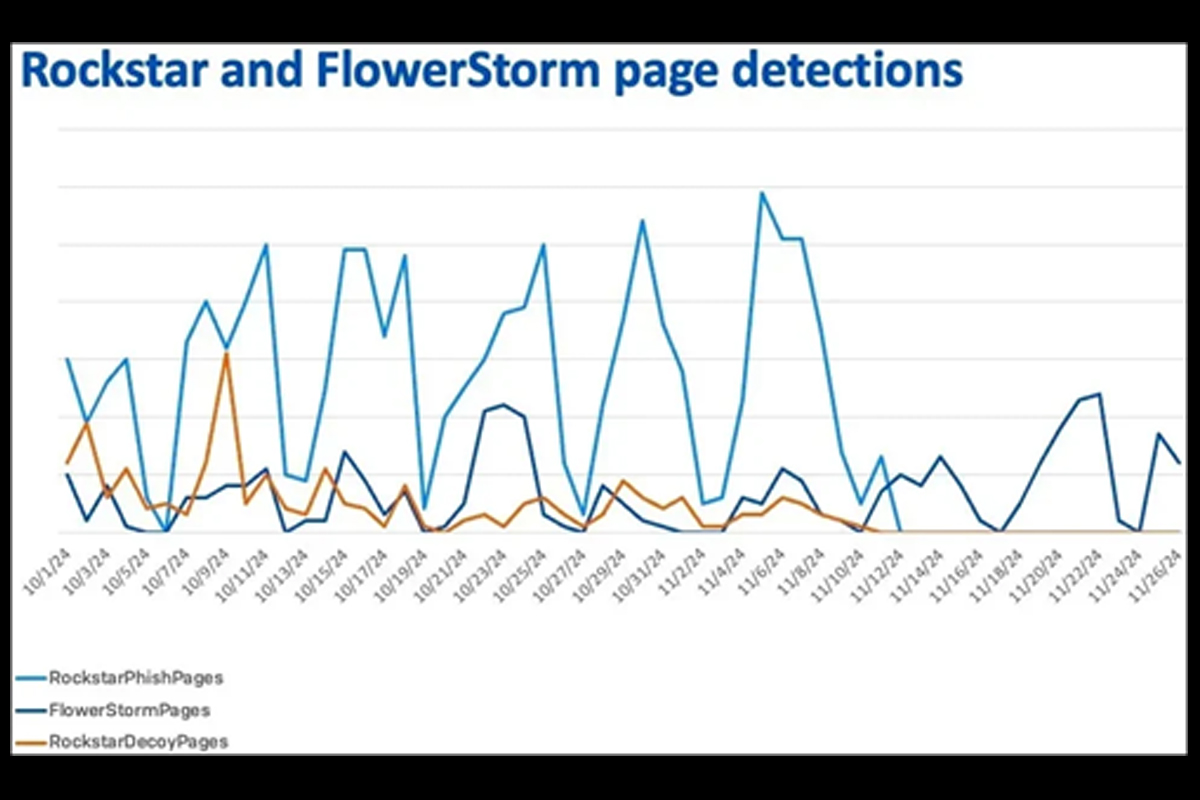
- At its peak, Rockstar2FA managed over 2,000 domains. After Rockstar2FA’s collapse, FlowerStorm saw rapid growth, which suggests a shared framework
Recommendations
- Avoid clicking links and opening attachments in unsolicited emails.
- Confirm requests from senders via contact information obtained from verified and official sources.
- Type official website URLs into browsers manually.
- Facilitate user awareness training to include these types of phishing-based techniques.
- Maintain robust and up-to-date endpoint detection tools on every endpoint.
- Consider leveraging behavior-based detection tools rather than signature-based tools.
- Report malicious activity to the FBI’s IC3 and NJCCIC.