Global IT Outage, Social Engineering
Microsoft,Scams
July 25, 2024
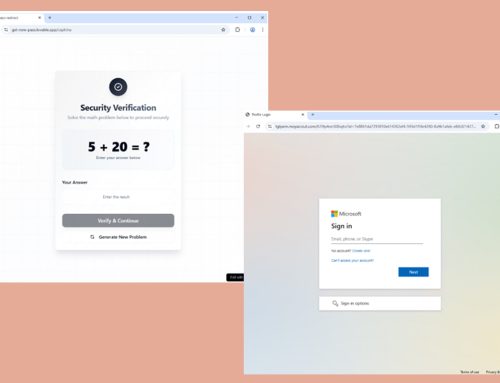
In the early morning of Friday, July 19, a Windows update pushed by CrowdStrike to its customers contained a defect that caused widespread global IT outages. Cyber threat actors
attempt to capitalize on this event in social engineering campaigns. These cyber threat actors registered typosquatting domains referencing the CrowdStrike incident. Threat actors will likely contact potential victims via phishing emails or text messages, luring them to click links, open attachments, or provide sensitive information or access.
Additionally, CrowdStrike Intelligence observed threat actors distributing a malicious ZIP archive named crowdstrike-hotfix.zip. The ZIP archive contains a HijackLoader payload that, when executed, loads the Remcos Rat. The campaign is likely targeting Latin America-based
(LATAM) CrowdStrike customers at this time due to the use of Spanish filenames and instructions within the ZIP archive.
Recommendations
- Avoid clicking links or opening attachments in communications from unknown senders, and exercise caution with emails that appear to come from known individuals and organizations.
- Report phishing emails to your organization’s IT department, where available.
- Only click links in articles and social media posts if you have verified that the links lead to official websites.
- Exercise caution with communications that emit a sense of urgency.
- Refrain from providing unverified individuals remote access to your device.
- Report social engineering attempts to the NJCCIC.