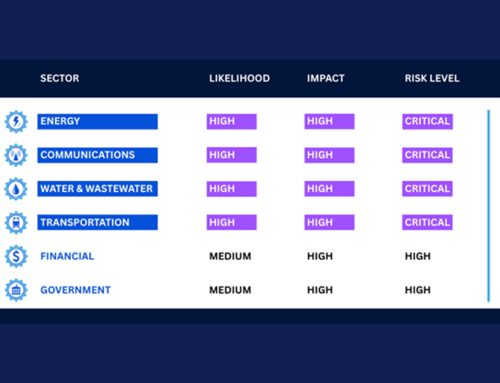
GorillaBot Unleashes DDOS Attacks
Global Attacks
October 10, 2024
The newest threat to emerge from Mirai’s leaked source code has made itself known in a big way. The botnet, dubbed GorillaBot , issued over 300,000 attack commands across 113 countries from September 4 to September 27, with China (20 percent), the United States (19 percent), and Canada (16 percent) as the most targeted countries. These attacks involved over 20,000 organizations worldwide, including almost 4,000 organizations in the United States. At its peak, over 20,000 commands were issued over 24 hours, demonstrating a consistent and substantial flow of commands.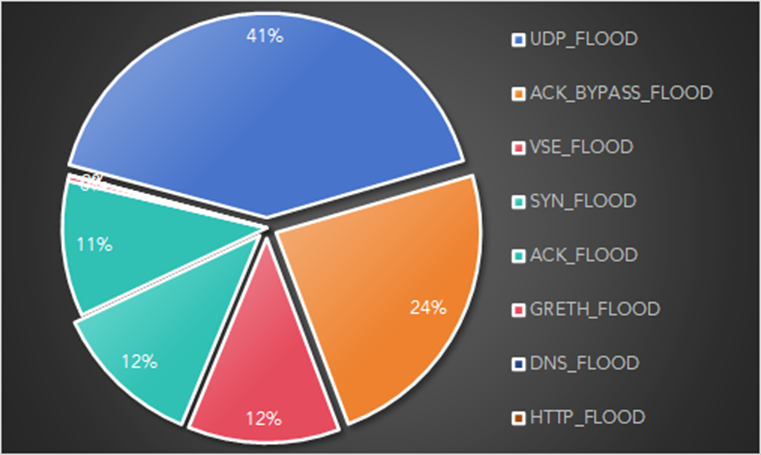
Image Source: NSFOCUS
GorillaBot utilizes several different attack methods but favors UDP Flood attacks, followed by ACK Bypass Flood attacks and Valve Source Engine (VSE) Flood attacks. Using the same process as the original Mirai , GorillaBot randomly selects one of five C2 servers to establish a connection and receive commands. GorillaBot employs 19 different distributed denial-of-service (DDOS) attack vectors and encryption algorithms, which the Keksec threat group often utilizes to encrypt key strings. An exploit named “yarn_init” is written into the code that uses a vulnerability in Hadoop Yarn RPC that allows for remote code execution without authentication. To maintain persistence, GorillaBot writes the “custom.service” file into the /etc/systemd/system directory and sets it to run automatically upon system boot. There is also a check to determine if the /proc file system exists on the infected device and if the system is a honeypot.
Recommendations
- Monitor network traffic, checking for any abnormal increases that could indicate the beginning of a DDOS attack.
- Regularly check for and remediate exploitable security flaws and vulnerabilities.
- Distribute servers and critical data in multiple data centers to ensure they are on different networks with diverse paths.
- Keep all devices patched with the latest security updates.
- Review the DDOS Attack Types and Mitigation Strategies NJCCIC Product for more information on DDOS attacks.
- Read more about IoT Devices and best practices in the IoT Device Security and Privacy NJCCIC product.