GRU Cyberattacks on Critical Infrastructure
Global Attacks
September 12, 2024
The Federal Bureau of Investigation (FBI), Cybersecurity and Infrastructure Security Agency (CISA), National Security Agency (NSA), and several partner-nation organizations attributed various cyber operations to Unit 29155, also known as EMBER BEAR , a group affiliated with the Russian General Staff Main Intelligence Directorate (GRU) 161st Specialist Training Center. These operations include espionage, sabotage, reputational harm, attempted coups, influence operations, and assassination attempts in Europe. Since 2020, the group has expanded its campaigns to include offensive cyber operations.
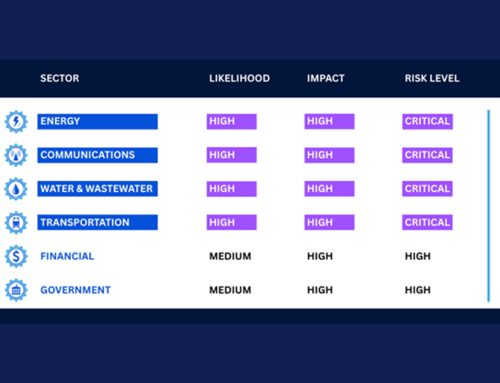
Prior to the Russian invasion of Ukraine on February 24, 2022, the Russian group conducted cyberattacks as early as January 13, 2022, using the WhisperGate malware as a preemptive strike to prepare the field for the upcoming military operations. Unit 29155 uses common red teaming techniques and publicly available tools, which can lead to misattribution. They use VPNs to anonymize their activity and typically exploit weaknesses in internet-facing systems. Additionally, they target critical infrastructure and key resource sectors, including government services, financial services, transportation systems, energy, and healthcare sectors of various NATO countries, as well as Europe, North America, Latin America, and Central Asia. Analysts assess that Unit 29155 cyber actors include junior active-duty GRU officers under the direction of experienced leadership. These individuals are enhancing their technical skills by performing cyber operations and intrusions. Furthermore, Unit 29155 cyber actors rely on non-GRU actors, including known cyber-criminals and enablers, to conduct their operations. Their recent focus appears to target and disrupt aid efforts to Ukraine.
Recommendations
- Users are encouraged to educate themselves and others on state-sponsored cyber threats to prevent victimization.
- Implement cybersecurity best practices to reduce risk and increase resiliency to cyber threats.
- Avoid clicking links, responding to, or otherwise acting on unsolicited text messages or emails.
- Use strong, unique passwords and enable multi-factor authentication (MFA) for all accounts where available, choosing authentication apps or hardware tokens over SMS text-based codes.
- Keep systems up to date and apply patches after appropriate testing.
- Utilize monitoring and detection solutions to identify suspicious login attempts and user behavior.
- Enforce the principle of least privilege, disable unused ports and services, and use web application firewalls (WAFs).
- Employ a comprehensive data backup plan and ensure operational technology (OT) environments are segmented from information technology (IT) environments.
- Regularly perform scheduled backups, keeping an updated copy offline in a separate and secure location, and testing it regularly.
- Cyber incidents can be reported to the FBI’s IC3 and the NJCCIC.