Increase in Cryptocurrency Scams
Scams
January 4, 2024
The NJCCIC has observed increased reports of cryptocurrency scams over the past few weeks, consistent with open-source reporting . The scams begin with a sophisticated phishing attack, often initiated via social media direct messages or posts, and use a crypto wallet-draining technique to target a wide range of blockchain networks. These cryptocurrency stealers are malicious programs or scripts designed to transfer cryptocurrency from victims’ wallets without their consent. Attribution is frequently obfuscated as many of these campaigns are perpetuated by phishing groups that offer wallet-draining scripts in scam-as-a-service operations.
The cybercriminal begins the scam by creating fake AirDrop or phishing campaigns, often promoted on social media or via email, offering free tokens to lure users. The target is directed to a fraudulent website to claim these tokens, which mimics a genuine token distribution platform that requests to connect to their crypto wallet. The target is then enticed to engage with a malicious smart contract , inadvertently granting the cybercriminal access to their funds, which enables token theft without further user interaction. Cybercriminals may use methods like mixers or multiple transfers to obscure their tracks and liquidate the stolen assets. Social engineering tactics in recent campaigns include fake job interviews via LinkedIn, romance scams, and other quick cryptocurrency return promotions offered through various social media platforms.
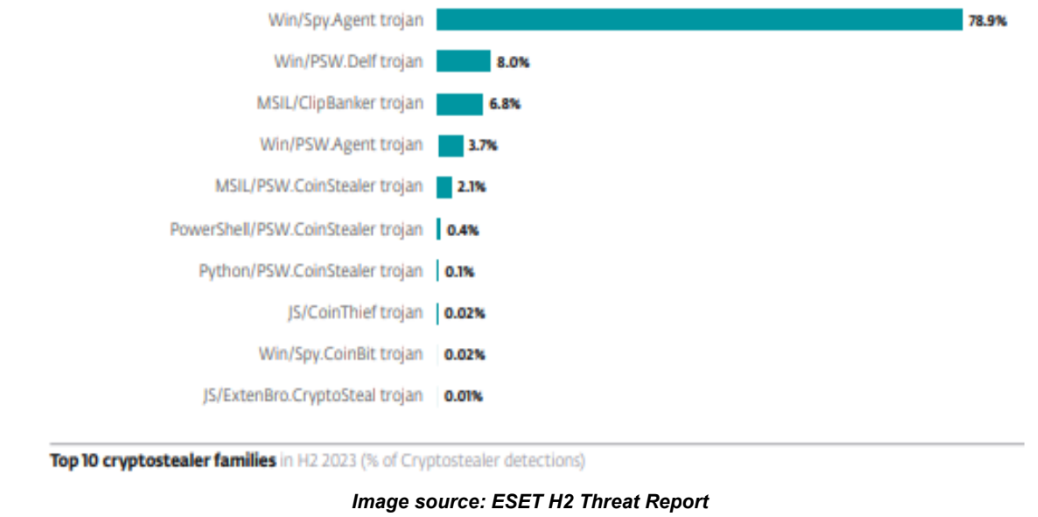
According to ESET’s H2 Threat Report (image above), the number of observed cryptocurrency threats decreased by 21 percent in the latter half of 2023; however, a sudden increase in cryptostealer activity was primarily caused by the rise of Lumma Stealer (78.9 percent), a malware-as-a-service (MaaS) infostealer capable of stealing passwords, multi-factor authentication (MFA) data, configuration data, browser cookies, cryptocurrency wallet data, and more. This infostealer was observed spreading via the Discord chat platform and through a recent fake browser update campaign. In this campaign, a compromised website displays a fake notice that a browser update is necessary to access the site. If the update button is clicked, the malicious payload is downloaded, delivering malware such as RedLine, Amadey, or Lumma Stealer to the victim’s machine. For any further questions contact us here at Cyber Command.





