Infostealers: Browser Extensions, Downloads
Malware
March 13, 2025
Cybercriminals use information-stealing malware, also known as infostealers, to gather data about users, their devices, and their networks. This information can include personal information, account information like online passwords, and other sensitive data. Infostealers are installed on victim devices in several ways, such as malicious browser extensions and downloads.
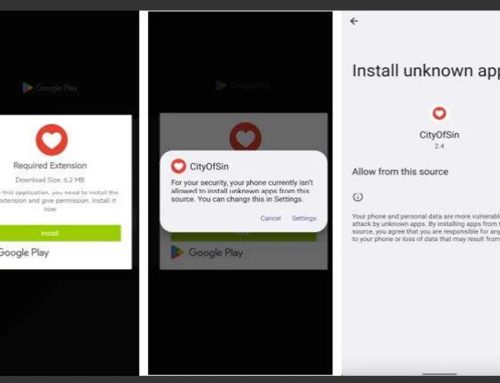
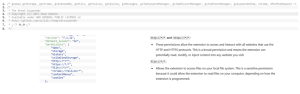
Users download browser extensions for a variety of reasons. After an extension is downloaded from official web stores, threat actors surreptitiously purchase or hijack popular extensions for malicious purposes and capitalize on the trust the extension has gained. Users often continue to use the extension even after it has been taken over by the new vendor, as they are likely unaware of the change. Oftentimes, the new vendor will also update permissions related to the extension, allowing them to access, read, and modify files on the users’ system and more, as noted in image 1. Some threat actors use the extension to inject code into the system’s browser to facilitate malvertising and search engine optimization fraud, which leads into the second stage of their operation.
If threat actors can manipulate search results and the online advertising viewed by users, they can push them to initiate malicious downloads. For example, the NJCCIC’s security operations center (SOC) team noted that malicious software known as pdfconverters[.]exe is often obtained by users searching for free worksheets, calendars, and more. While this program can convert documents, its real purpose is acting as a RedLine infostealer. A screenshot of the site and associated URLs advertising this download is noted in images 2 and 3.

Users who navigate to the sites advertising malicious downloads are often redirected there by other sites. Image 4 shows how a user is referred to these sites by malvertisements (column 3).

Once pdfconverters[.]exe is downloaded, the threat actors exfiltrate information to command and control (C2) domains through WebView2, which occurs in a window that is hidden from the user. A screenshot of the WebView2 history in image 5 shows those domains being contacted; however, this was not visible in the user’s regular browsing history.

Once the infostealer has been installed on the user’s device, it can gather sensitive information including the data, files, and images on the device; browsing history; account passwords, and more. Image 6 shows an example of the browser information that would be viewable by the threat actors, who could easily decrypt the passwords associated with the noted websites.

Technical Analysis and IOCs
While the sites and associated executable files and names may vary in these campaigns, below is the technical analysis of events previously observed by our SOC team, which include indicators of compromise (IOCs).
The source of the infostealer was attributed to SEO Poisoning and Adware redirects. As it is seen in our environment, most users were referred to the malicious hxxps://pdfconvertercompare[.]com by Google Ads. In one instance, the user was referred to the site containing the payload through the potentially compromised site: hxxps://homemade-gifts-made-easy[.]com. In all documented cases, the user is either browsing the web or visiting a site in search of a free service when they click on the ad and are redirected.
Following the visit to the PDF Converter site, PDFConverters.exe is downloaded onto the machine. The application is dropped into the Temp directory. The names of the created directories are %TEMP%\.Net\PdfConverters and %TEMP%\PdfConverters.WebView2. The second directory will act as the user directory location for the WebView2 application, which is used to obtain and launch the executables.
Once the executable is on the machine, the application is then loaded through msedgewebview2 process. From here, hxxp://www[.]pdfconvertercompare[.]com/main is contacted, which contains main.js, an additional payload. It seemed that the only way to discover the presence of this URL is by extracting the MS Edge WebView2 History file located in C:\Users\%USER%\AppData\Local\Temp\PdfConverters.WebView2\EBWebview\Default\History. Based on the analysis of our environment and other security researchers’ experiences, it appears that there are multiple versions of this threat and depending on the version, the following steps may differ.
1. PDFunk.exe is downloaded from hxxp://www[.]pdfconvertercompare[.]com/main. Following this, the application runs and then POST requests with Base64 encoded data are observed connecting to multiple C2 domains.
or
2. PDFunk-Setup.exe is downloaded from hxxp://www[.]pdfconvertercompare[.]com and begins loading additional dll files.
Among the dll files downloaded from hxxp://www[.]pdfconvertercompare[.]com is App.dll. App.dll has been identified as the main code in this campaign by security researchers. The script is written in C# and performs many actions on the machine, including checking for forensic and analysis tools, executing processes, initiating keystrokes, conducting clipboard manipulation, and modifying Chrome and Edge preferences. If forensics or analysis tools are detected, the process will not continue to run on the machine.
Recommendations
- Organizations are advised to implement controls to prevent the installation of unapproved browser extensions and software.
- Users should only download browser extensions and software from reputable sources.
- Periodically review current browser extensions to ensure they have not been removed from official web stores.
- Run an updated anti-malware program on all devices.
- Only grant permissions to browser extensions, applications, and software that are necessary to perform their intended tasks. Refrain from permitting the viewing or changing of device data.
- Remove extensions, applications, and software that are no longer in use.
This Multi-State Information Sharing and Analysis Center (MS-ISAC) Advisory is being provided to assist agencies, organizations, and individuals in guarding against the persistent malicious actions of cybercriminals.
|
|
|
|
|
|
|
|
|