Iranian APT New Malware
Global Attacks
December 12, 2024
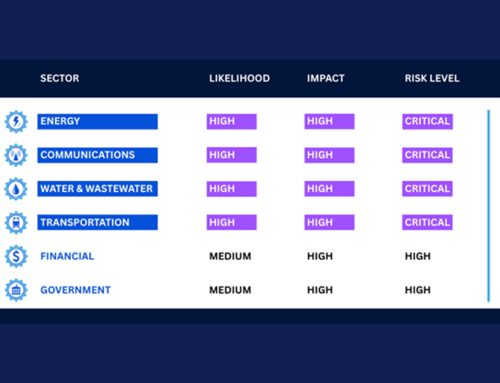
Iranian threat actors have deployed a new malware, IOCONTROL, to target Internet of Things (IoT) devices and Operational Technology (OT)/SCADA systems in critical infrastructure across Israel and the United States. Analysts have categorized IOCONTROL as a nation-state cyberweapon capable of causing significant disruptions. This malware can impact various devices, including routers, programmable logic controllers (PLCs), human-machine interfaces (HMIs), IP cameras, firewalls, and fuel management systems from multiple manufacturers, such as D-Link, Hikvision, and Gasboy.
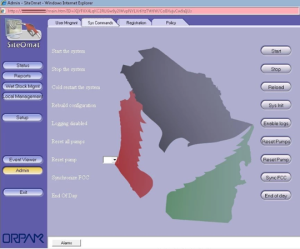
A malware sample was extracted and analyzed from a fuel management system allegedly compromised by the CyberAv3ngers, an Iranian Government’s Islamic Revolutionary Guard Corps (IRGC)-affiliated advanced persistent threat (APT) group. The group has historically targeted and attacked industrial control systems used in critical infrastructure and was linked to the Unitronics PLC attack in November 2023. While the initial attack vector is unknown, evidence indicates that IOCONTROL was used to compromise approximately 200 gas stations in late 2023, coinciding with cyberattacks on water treatment facilities. Reports suggest the APT group uses tools like ChatGPT to aid in exploits and plan attack strategies.
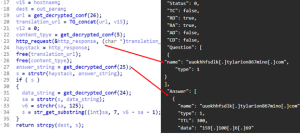
In September, a malware sample was analyzed using a VirusTotal sandbox, which initially revealed zero detections; however, the number of detections increased to 21 as of December 10. IOCONTROL supports the following commands: “send ‘hello”; “check exec”; “execute command”; “self-delete”; and “port scan.” These commands execute using system calls from the ‘libc’ library, and outputs are saved in temporary files for reporting.
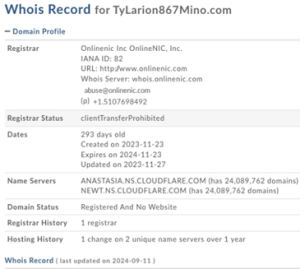
Additionally, the malware sample revealed specific configurations and a stored DNS name, uuokhhfsdlk[.]tylarion867mino[
Recommendations
- Implement cybersecurity best practices to reduce risk and increase resiliency to cyber threats.
- Avoid clicking links, responding to, or acting on unsolicited text messages or emails.
- Keep systems up to date and apply patches after appropriate testing.
- Use strong, unique passwords and enable multi-factor authentication (MFA) for all accounts where available, choosing authentication apps or hardware tokens over SMS text-based codes.
- Enforce the principle of least privilege, disable unused ports and services, and use web application firewalls (WAFs).
- Employ a comprehensive data backup plan and ensure operational technology (OT) environments are segmented from information technology (IT) environments.
- Perform scheduled backups regularly, keeping an updated copy offline in a separate and secure location and testing it regularly.
- Ingest indicators of compromise (IOCs) and tactics, techniques, and procedures (TTPs) outlined in the Claroty report into endpoint security solutions. Consider leveraging behavior-based detection tools rather than signature-based tools.
- Report cyber incidents to the FBI’s IC3 and the NJCCIC.