Latrodectus: the New IceID
Malware
April 11, 2024
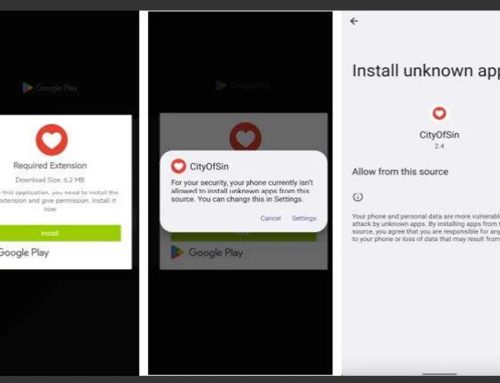
In November 2023, researchers discovered a new loader, dubbed Latrodectus, due to a string identified in the malware’s code. As of February, Latrodectus has been identified and delivered in nearly a dozen phishing campaigns. The malware functions as a downloader, with the end goal of downloading payloads and executing commands. Upon download, Latrodectus also performs various sandbox evasion checks to avoid detection and analysis by researchers.
While initial research suggested that Latrodectus was a newly released variant of IcedID, analysis later confirmed that it was a separate malware. Based on the malware’s functionality and similar characteristics in the disassembled sample, researchers found that Latrodectus was likely written by the same threat actors that wrote IcedID.
Analysts have identified two initial access brokers (IABs) as the threat actors impersonating organizations and distributing this malware. Threat actor TA578 ’s tactic involves messages threatening legal action against alleged copyright infringement to scare users into clicking links. In this campaign, the threat actors send the initial message through their target’s online contact forms. To add legitimacy to the copyright claim, the body of the malicious email includes a unique URL with both the name of the impersonated organization and the target.
The NJCCIC recommends that users and organizations educate themselves and others on these continuing threats and tactics to reduce victimization. Users are advised to refrain from responding to unsolicited communications, clicking links or opening attachments from unknown senders, and exercise caution with
communications from known senders. If unsure of the legitimacy, contact the sender via a separate means of communication, such as by phone, before taking action. Additionally, visit websites directly by manually typing the legitimate URL into a browser and refrain from navigating to online accounts via emailed links. Phishing emails and other malicious cyber activity can be reported to the FBI’s IC3, and the NJCCIC.