Lessons Learned from the 23andMe Hack
Mitigation
December 25, 2023
In October, 23andMe notified 6.9 million people that their information was compromised by hackers. However, as it turns out… 23andMe was not actually hacked. At least, not directly.
So what actually happened?
Hackers used stolen login information from data leak forums and tried to log into 23andMe using those same stolen email and password combinations. This tactic is called “credential stuffing”.
I don’t get it.
To remove any confusion, here it is spelled out.
Hackers downloaded stolen email and password combinations from different data leaks sites on the dark web. For example, let’s say at some point someone’s Facebook account was hacked. And let’s say that person used their email johndoe@gmail.com and favorite password that they never forget “Password123” to log into their Facebook account. The hackers then took a gamble and tried to log into 23anMe using the same username and password combinations to log in. And the hackers got lucky 14,000 times.
On 23andMe, users have the option to share ancestry and genetic information with relatives with whom they’re related. So even though the hackers got into 14,000 accounts, by doing so they actually gained access to records belonging to 6.9 million people.
Yikes. So what can we learn from this?
Well, before we get into that, let’s see what mistakes were made by these hacked users that allowed the hack to happen in the first place.
- For starters, the hacked users used the same email and password combination on more than one platform. This is a huge “no no”, which you likely learned already through Cyber Command’s Cybersecurity Training portal.
- The hacked users also did not have two factor authentication (2FA) enabled on 23andMe. How do we know this? Because if they had enabled 2FA, then the hackers would have had to enter a 2FA code, either from the actual user’s phone, or from an authenticator app. Without 2FA codes, the hackers would not have been able to get into the 23andMe accounts.
So, now what can we learn from this?
- Always use complex passwords.
- Always use unique passwords.
- Always enable 2FA on every platform to which you have access.
What do you mean by complex passwords?
We define a complex password as one that uses uppercase and lowercase letters, numbers and symbols, and is at least 14 characters long.
What do you mean by unique passwords?
Unique passwords means that they are not the same or similar to another password used. This means that you should not simply add an exclamation point or an @ sign to the end of your favorite password used on a different site, because this does not constitute unique. Passwords should be truly unique, and not similar to any other. Knowing your password to one account should not in any way give a hacker the clues needed to break into a different account of yours.
How important is it to use complex passwords?
Exceedingly important. Let’s say you have a favorite password that you use. The password is easy to remember, you use it all the time, and is a combination of “stuff” that only you know. Let’s use 37Av@tArs as our example for the password.
That password has uppercase and lowercase letters, numbers and symbols. So, what’s the problem with that password?
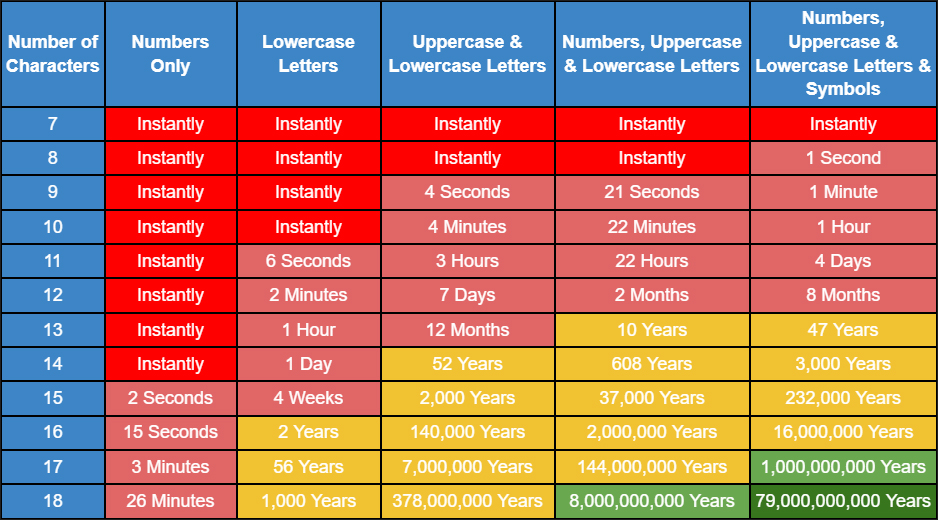
The problem is that as complex as the password is, the password only has 9 characters, and took only one minute to hack using brute force password attacking software that anyone can download for free from the Internet. Here is a chart that illustrates different password types and how long it would take for a hacker to crack.
Ok. So remind me, what again is a secure password?
The short answer is, your passwords should have the following characteristics to be considered secure.
- Uppercase letters.
- Lowercase letters.
- Numbers.
- Symbols.
- Be at least 14 characters long, but preferably be 18 characters long.
Whoa. According to the chart, even a 13 character password will take forty seven (47) years to crack. Why do we need to go crazy overboard?!
That is a great question. As you likely already know, technology is getting better and faster each year, and shows no signs of slowing down. Because the machines used by hackers (the same ones we buy in stores) are getting faster, so too it takes less time to crack a password using a newer computer than it does using an older computer. For example…
- In 2020, it would have taken a whopping 34,000 years to crack a 12-character password with uppercase and lowercase letters, numbers and symbols. In 2023 however, it only takes eight months to crack.
- In 2020, it would have taken 5 years to crack a 10-character password with uppercase and lowercase letters, numbers and symbols. In 2023 however, it only takes 4 days to crack.
So, again, as computer processing power increases, the time it takes to crack passwords substantially decreases. So, instead of changing your passwords every year, let’s add some additional complexity now.
Let’s bottom line this.
Follow these rules.
- Always use secure passwords. (Complex + Unique = Secure.
- Always enable 2FA on any and every platform.
How can I possibly be expected to remember a bajillion secure passwords to all the different websites I log into?
You’re not expected to remember them. Instead, you should always use a password manager to store your passwords.
I need help implementing a password manager. What should I do?
Contact us here at Cyber Command to discuss password manager implementation. It’s fairly straightforward, and only takes a few minutes to set up.
Lessons Learned
A wise man once said that wise people learn from their own mistakes, but geniuses learn from the mistakes of others. Let’s be geniuses and make sure to always use secure passwords and 2FA!