LokiBot Malware Returns
Malware
June 27, 2024
LokiBot, an infostealing malware that targets Android and Windows devices, was first spotted in 2015. LokiBot is a trojan primarily distributed through innocuous-appearing files. Once installed, LokiBot uses a keylogger to monitor desktop activity and steal user credentials, cryptocurrency wallets, and other sensitive information. Recent activity spotted by the NJCCIC’s email security solution reveals a continuing trend.
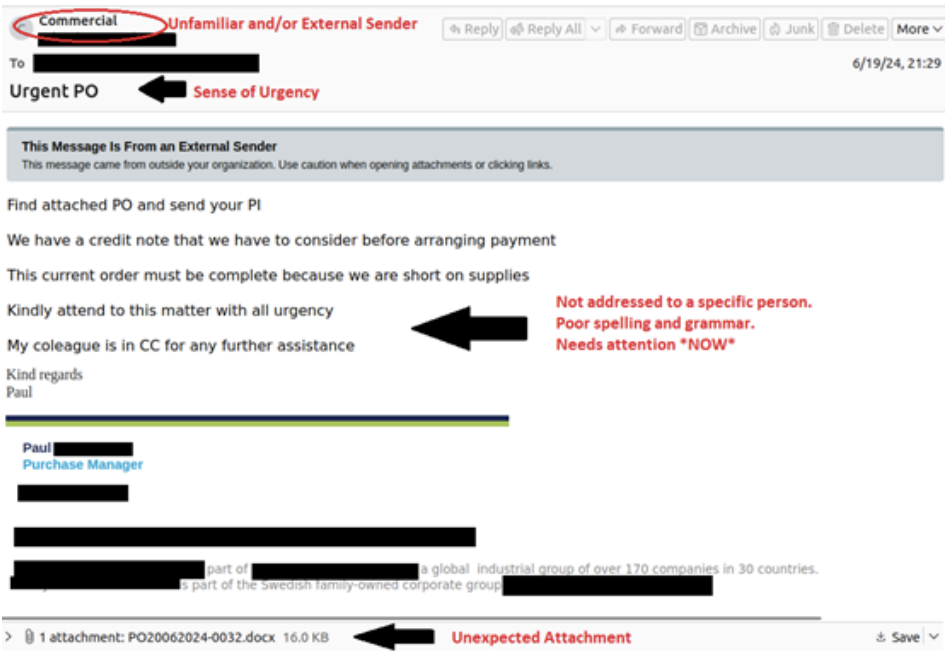
A recurring campaign by TA2536 involves phishing emails with attached Microsoft Office attachments with embedded Packager Shell Objects (OLE). Once opened, these embedded OLE compressed executables use LCG Kit to exploit vulnerabilities in Microsoft’s Equation Editor and download various malware, including STRRAT, XLoader, RedLine, LokiBot, Remcos RAT, or AgentTesla.
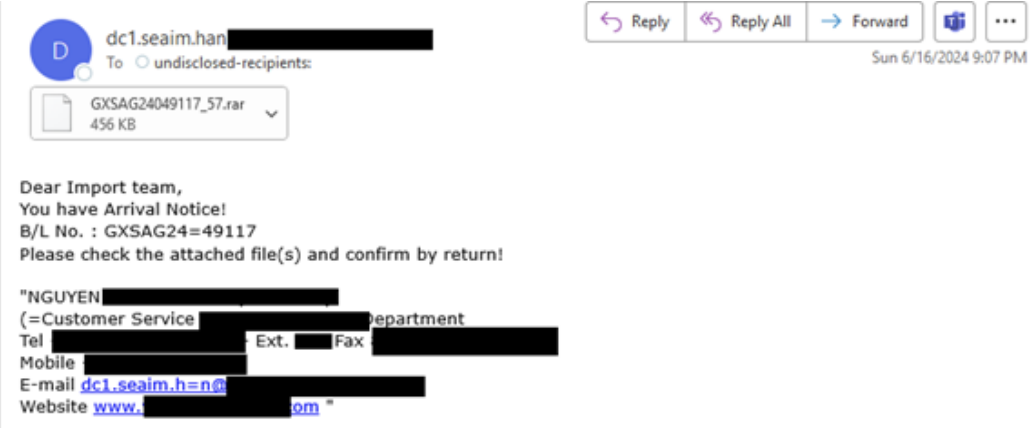
Earlier this month, a second campaign was observed spreading LokiBot. In this instance, the phishing email included a compressed RAR file, which installs LokiBot upon execution. In both campaigns, there were easy-to-spot signs that the emails were likely malicious, including uncommon senders, unexpected attachments, generic greetings, and awkward language that would be unexpected in a professional email.
Recommendations
- Avoid clicking links and opening attachments in unsolicited emails.
- Confirm requests from senders via contact information obtained from verified and official sources.
- Review the Don’t Take the Bait! Phishing and Other Social Engineering Attacks NJCCIC product for more information on common phishing and social engineering attacks.
- Facilitate user awareness training to include these types of phishing-based techniques.
- Maintain robust and up-to-date endpoint detection tools on every endpoint.
- Consider leveraging behavior-based detection tools rather than signature-based tools.
- Phishing and other malicious cyber activity can be reported to the FBI’s IC3 and the NJCCIC.