Magniber Attacks Targeting Home Users
Ransomware
August 8, 2024
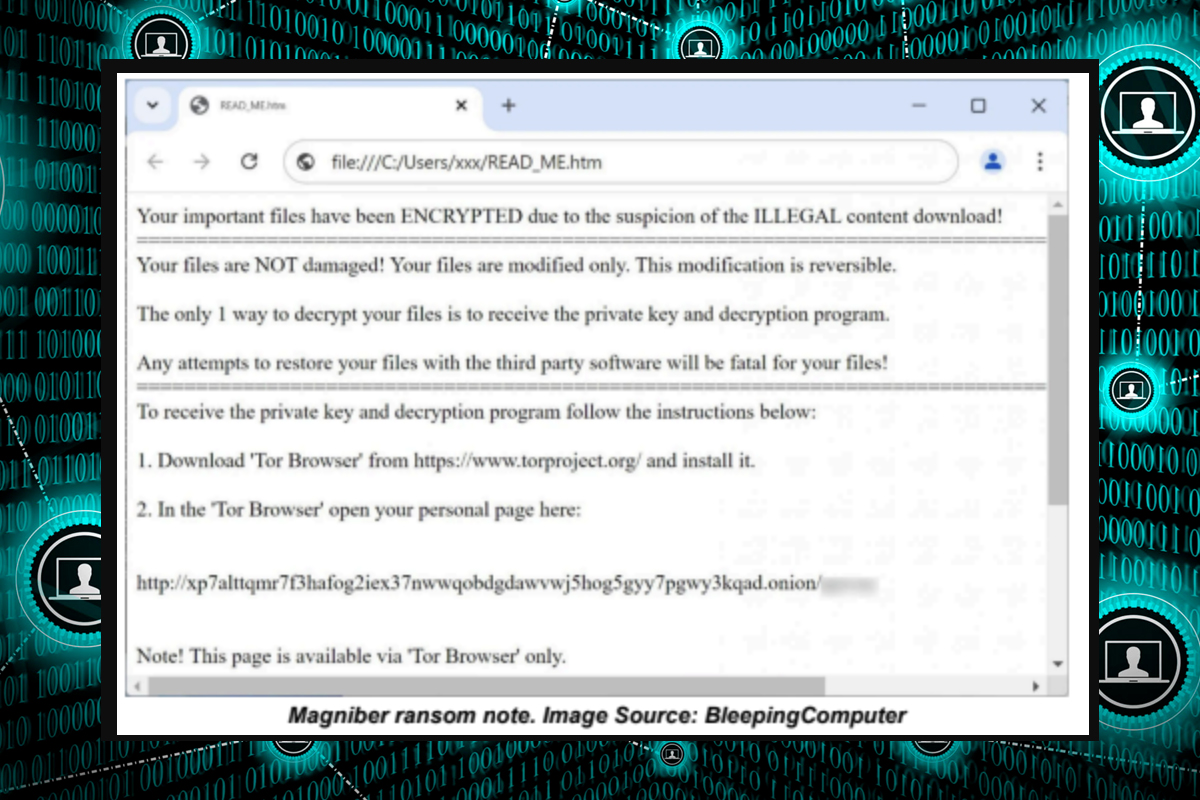
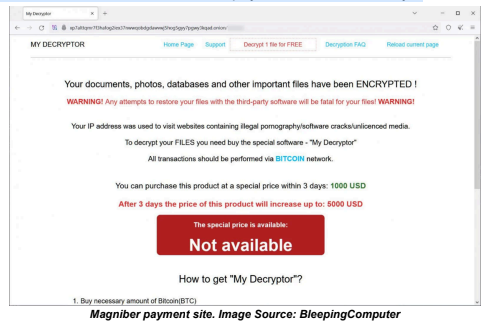
Researchers reported a global spike in Magniber ransomware attacks targeting home users. Since July 20, one website received almost 720 submissions from infected users. Magniber was first discovered in 2017 and is believed to be a successor to Cerber ransomware. Users infected with this variant will have a random five to nine-character extension appended to encrypted files. Victims will find a ransom note named READ_ME.htm instructing them to download the Tor Browser to reach the Magniber ransom site. As this campaign targets home users, the ransom payment initially has been set at $1,000 but will increase to $5,000 if the threat actors do not receive the Bitcoin payment within three days.
While there is no transparent attack vector for this campaign, users are advised to be wary of downloads from unknown or untrusted sources and to avoid cracked software and key generators. Currently, there is no free option available to decrypt files encrypted by this version of Magniber.
Recommendations
- Obtain software from legitimate developers or companies after analyzing customer reviews.
- Establish a comprehensive data backup plan that includes regularly performing scheduled backups, keeping an updated copy offline in a separate and secure location, and testing it regularly.
- Keep systems up to date and apply patches after appropriate testing.
- Use strong, unique passwords for all accounts and enable MFA where available, choosing authentication apps or hardware tokens over SMS text-based codes.
- Maintain robust and up-to-date endpoint detection tools on every endpoint.
- Consider leveraging behavior-based detection tools rather than signature-based tools.
- Report ransomware and other malicious cyber activity to the FBI’s IC3 and the NJCCIC.