MFA: Why Do I Need This?
Mitigation
December 4, 2023
Authentication control is a process used to validate a user’s identity, and is accomplished by presenting a challenge to the user attempting to log into their account. The challenge is “prove to me that you are who you say you are”. An example of this control is MFA, which helps protect online accounts from unauthorized access.
What is MFA?
MFA literally means what it stands for; “Multi Factor Authentication”, which means using multiple ways to authenticate your identity (or in other words, to prove that you are who you say you are). MFA is an effective measure to protect users from account compromise via credential theft or exposure as part of a data breach. Even if a threat actor (hacker) gains access to an account password, they will be unable to access the associated account without the user’s second (and/or third) authentication factor.
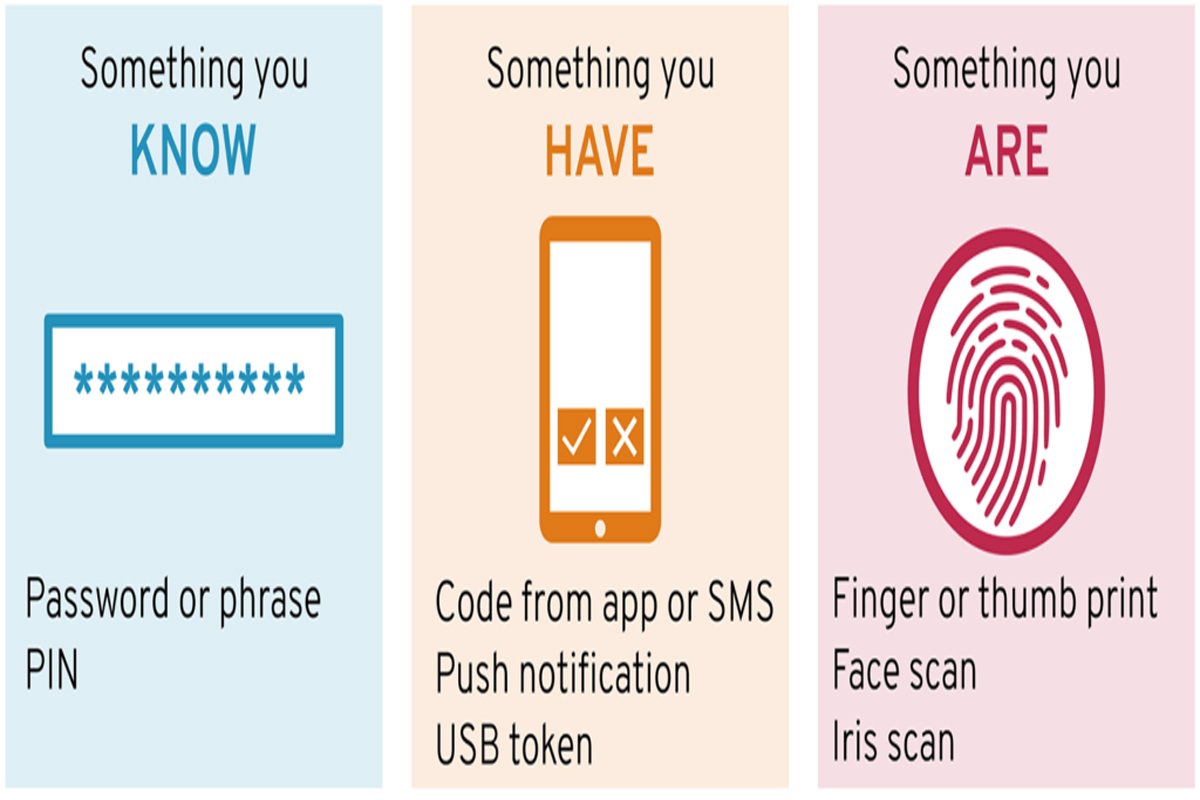
MFA requires two or more different factors and consists of a variety of authentication methods:
- Something you have: obtained by physical objects, such as codes provided via authentication apps or text messages on smartphones, smart cards, USB devices, and security hardware tokens.
- Something you know: anything that can be remembered and then typed, verbalized, performed, or recalled, such as passcodes, PINs, combinations, code words, and answers to security questions.
- Something you are: any part of the human body that can be used as verification, such as fingerprints, facial recognition, palm scans, retina scans, iris scans, and voice verification.
MFA is strongly recommended for all accounts where available, especially those associated with work, school, email, banking, social media, and online stores. Authentication apps, hardware tokens, or biometrics are preferred as a second factor instead of text-based authentication.
How does this affect me?
Once 2FA has been set up, anytime you log into an account of yours, depending on your location, the date and time, your Internet connection and some other variables, you may be challenged to validate your identity either by additionally receiving a text message with a code, or by using the Google Authenticator app.
An Even Stronger Security Posture
In 2024, lets strive to kick it up a notch not only to stay compliant, but also to ensure that we are all doing the best we can to avoid a serious cybersecurity threat.
- Google Authenticator Only for 2FA: For starters, we recommend switching from receiving text messages as your 2FA method, and instead to only use a trusted authenticator app, such as Google Authenticator. This will require you to download the Authenticator app to your personal or work smartphone, from either the Google Play store or from the Apple Store.
- YubiKeys: Second, we recommend using physical security keys such as YubiKeys to implement an even stronger MFA method. As shown in the picture below, those little holes are to connect them to a keychain so that you do not lose them.