More PFS in Phishing Emails
Scams
September 12, 2023
The NJCCIC observed a high volume of phishing emails targeting New Jersey State employees, attempting to harvest credentials or deliver malware by abusing the Interplanetary File System (IPFS) and other Web3 technologies. IPFS is a giant peer-to-peer distributed file storage protocol that enables users to exchange files worldwide. Unlike centralized systems which use file paths, IPFS files use a decentralized naming system and are given unique content identifiers (CID) derived from a file’s hashed content. IPFS is often used for legitimate purposes; for example, blockchain and NFT projects commonly implement decentralized storage such as IPFS. Throughout 2022, analysts observed threat actors actively leveraging IPFS in phishing attacks and its popularity has steadily increased largely due to low-cost storage and resiliency against content moderation. Additionally, the use of common IPFS gateways makes it more difficult for organizations to block access.
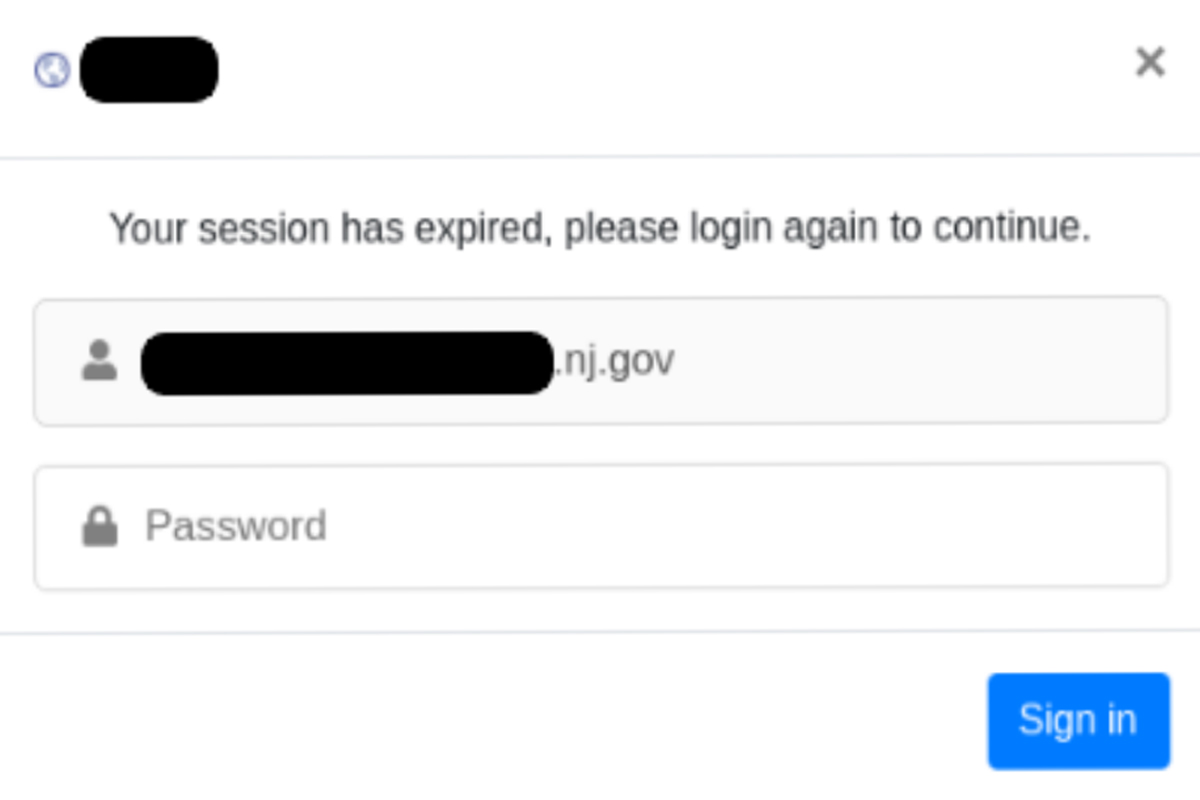
The phishing emails contain various subject lines including document-signing services, invoices, receipts, or claims that unusual sign-in activity was detected. The message often contains typical phishing red flags and an IPFS file link link (1, 2 ) that redirects recipients to various web pages with the intent to harvest credentials, steal funds, or deliver malware. In the above example, the included link was appended with the recipient’s email address and redirected the user to a prefilled authentication page. While IPFS gateway providers attempt to regularly delete links to fraudulent and malicious files, the detection and deletion process
of links at the gateway level is slow. The NJCCIC analysts assess that this activity will continue to increase due to its resiliency against content moderation, ease of use, obscured attribution, and reduced cost to the threat actor.
Recommendations
- The NJCCIC recommends users and organizations educate themselves and others on these continuing threats and tactics to reduce victimization. Users are advised to refrain from responding to unsolicited communications, clicking links or opening attachments from unknown senders, and exercise caution with communications from known senders.
- If unsure of the legitimacy, contact the sender via a separate means of communication, such as by phone, before taking action. Additionally, visit websites directly by manually typing the legitimate URL into a browser and refrain from navigating to online accounts via links delivered in emails.
- Phishing emails and other malicious cyber activity can be reported to the FBI Internet Crime Complaint Center (IC3) and the NJCCIC.