National Insider Threat Awareness Month
Mitigation
September 10, 2023
September 2023 marks the fifth annual National Insider Threat Awareness Month (NITAM), an initiative highlighting the importance of safeguarding our nation by detecting, deterring, and mitigating insider threats. NITAM assists public and private organizations in educating their workforce, enhancing their employees’ capacity to identify potential risks, and increasing prevention awareness.
How does this effect me?
Insider threats are individuals with authorized access who, wittingly or unwittingly, use that access to harm their organization and its resources. Insiders can include employees, vendors, partners, suppliers, and others. Insider threats impact both public and private institutions, causing damage to national security, loss of life, the loss or compromise of classified or sensitive information, and billions of dollars annually in lost revenue related to trade secret theft, fraud, sabotage, damage to an organization’s reputation, acts of workplace violence, and more. Most insider threats exhibit known or identifiable concerning behavior prior to committing malicious acts. If identified early, many risks can be mitigated before harm occurs.
Cybersecurity insider threats typically refer to an individual who, intentionally or unintentionally, uses their authorized access to an organization’s data and resources to harm the company’s equipment, information, networks, and systems. Insider threat behaviors can damage an organization through corruption, espionage, degradation of resources, sabotage, terrorism, and unauthorized information disclosure. These damaging behaviors may enable threat actors to launch subsequent cyberattacks and can lead to an organization suffering data loss or other security exploits.
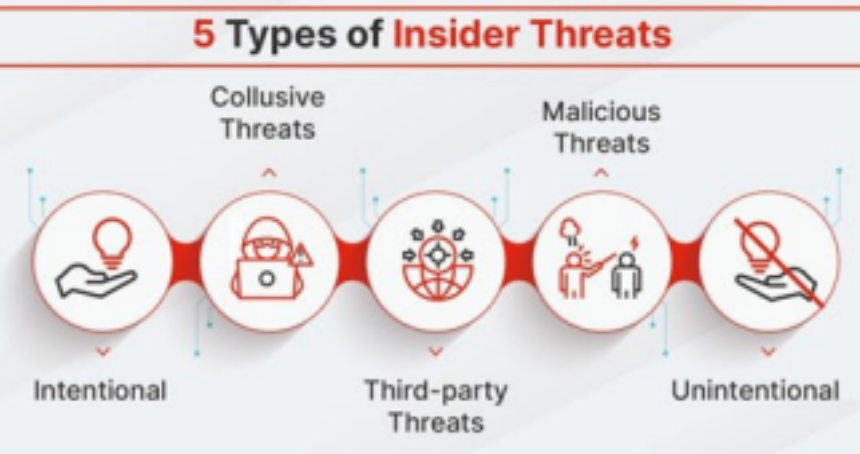
As shown in the picture above, the five general types of insider threats include intentional, unintentional, third-party, malicious, and collusive. Insider threats can be challenging to detect and may go unnoticed for months or years. Cybersecurity teams need to detect, investigate, and respond to these potentially damaging attacks quickly and effectively.
What do I do?
Warding Against Insider Threats:
Early Detection:
- Monitor employee behavior: Look for changes in access patterns, excessive overtime, sudden downloads, or unusual interactions.
- Track financial transactions: Watch for suspicious expenses or transfers, especially involving stolen data or trade secrets.
- Identify concerning behaviors: Be alert to signs of dissatisfaction, grievances, or financial stress among employees.
- Report suspicious activity: Encourage employees to report concerns confidentially through designated channels.
Bystander Engagement:
- Create a culture of trust: Encourage open communication and reporting of concerns without fear of retribution.
- Train employees on bystander intervention: Provide guidance on how to recognize and report potential insider threats.
- Empower employees to act: Offer confidential reporting channels and support when concerns are raised.
- Promote a positive work environment: Address employee grievances and foster a sense of belonging to mitigate risks.
By implementing these measures and fostering a culture of vigilance, organizations can significantly reduce the risk of insider threats and protect their valuable assets.