Observed TA2725 Phishing Campaigns
Malware,Scams
August 1, 2024
TA2725 is a financially motivated cyber threat actor that typically targets Latin America (LATAM) and some European countries. The group has its tactics and is now delivering Mispadu and Astaroth malware in phishing campaigns targeting the Garden State Network (GSN). TA2725 primarily targets finance, services, manufacturing, law firms, and commercial facilities and uses a multi-stage infection process. TA2725 historically exploited Windows SmartScreen vulnerabilities; however, their most recent campaign tactics include sending phishing emails with URLs that lead to malware download pages, distributing malware through zipped files (MSI, HTA, exe, etc.), and employing geofencing tactics. They typically target banking credentials, as well as credentials and payment data for popular consumer accounts such as Netflix and Amazon. Other banking malware distributed in past campaigns includes Ousaban Stealer and Grandoreiro trojans.
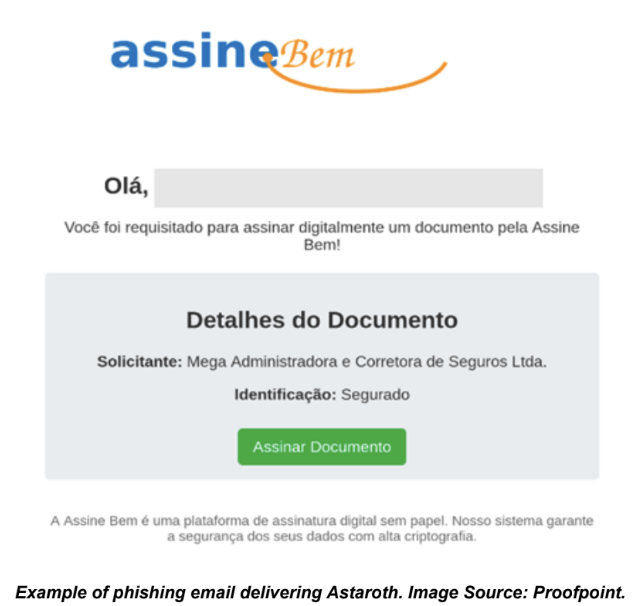
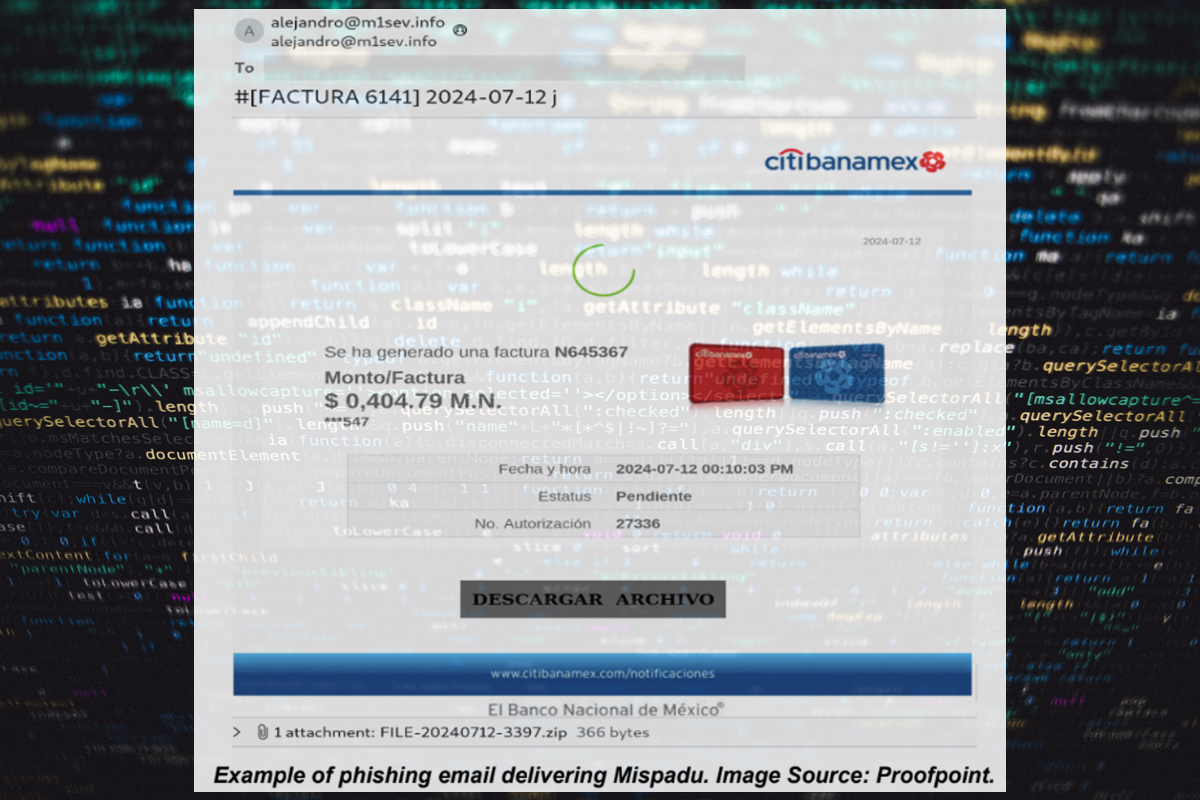
Phishing emails observed in this campaign use banking transaction lures in Spanish that include links to a zip file containing an HTA file. The final malware payload is Mispadu, a LATAM malware loader that typically drops banking malware and remote access trojans. HTA stands for HTML Applications and executes media files; however, it can also be used for malicious purposes without a GUI. In phishing campaigns delivering Astaroth, TA2725 uses emails with Portuguese language lures related to CENPROT shared documents and tax lures containing a zipped LNK file that leads to the Astaroth malware.
Recommendations
- Facilitate user awareness training to include these types of phishing-based techniques.
- Avoid clicking links and opening attachments in unsolicited emails.
- Confirm requests from senders via contact information obtained from verified and official sources.
- Review the Don’t Take the Bait! Phishing and Other Social Engineering Attacks NJCCIC product for more information on common phishing and social engineering attacks.
- Maintain robust and up-to-date endpoint detection tools on every endpoint.
- Consider leveraging behavior-based detection tools rather than signature-based tools.
- Phishing and other malicious cyber activity can be reported to the FBI’s IC3 and the NJCCIC.