Cyber Command
Cyber Command Corporation is an IRS approved 501(c)(3) nonprofit, public charity that offers cybersecurity awareness training and develops viable cybersecurity defense software.
Mission Statement
Cybersecurity concerns are one of the most critical threats facing the security of our nation, which impacts all United States citizens, including individuals, families, businesses of all sizes and verticals, and government organizations.
Our mission is to reduce threat risk by promoting cybersecurity education and awareness, facilitating research, advancing development, and enabling dissemination of cybersecurity defense products and services to USA individuals, public and private organizations.
Want to organize a free virtual or in-person cybersecurity class for seniors in your neighborhood? Please contact us below and we’ll get the process started!
Cybersecurity Intelligence Feed & Resources
This section contains free cybersecurity related articles and knowledge to help learn critical cybersecurity lessons.
Malicious Packages Hidden in PyPI
Python Package Index (PyPI) has recently observed several malicious packages hidden in its repository. PyPI hosts almost 600,000 projects written in the Python programming language. The original aiocpa package, self-described as a “synchronous & asynchronous Crypto Pay API Client”...
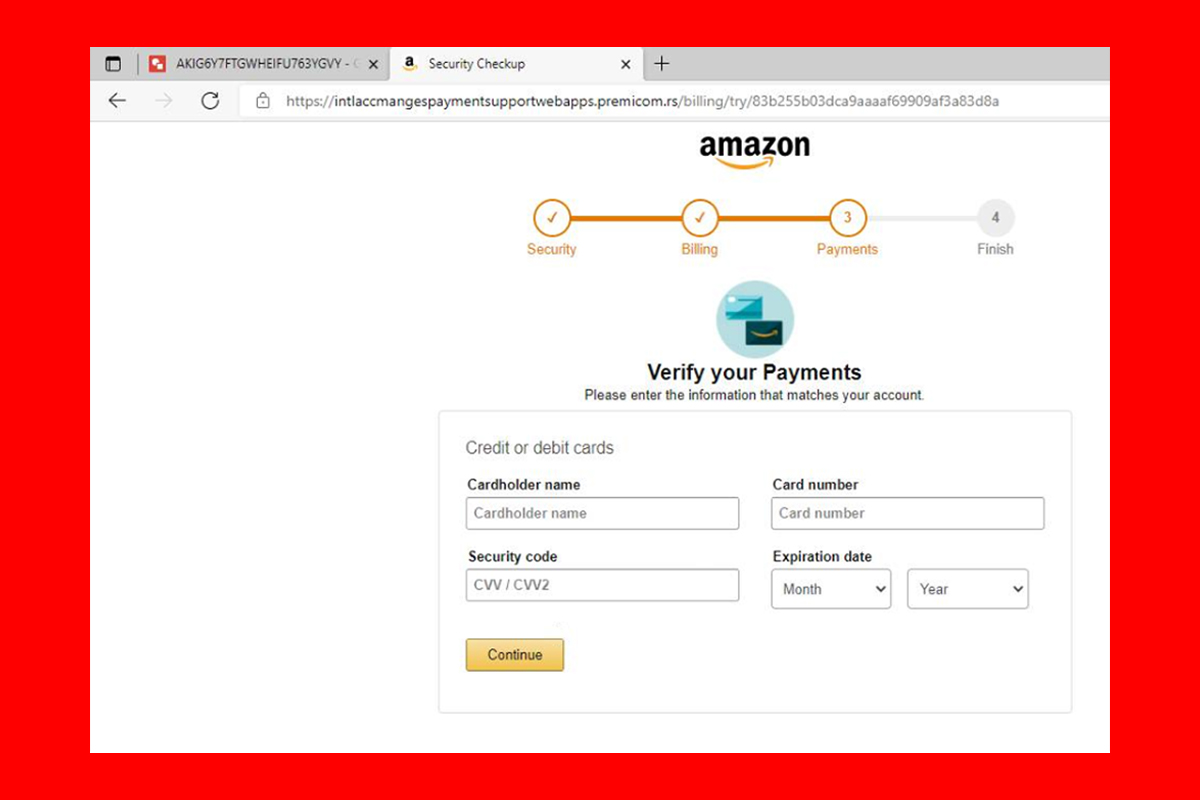
Amazon Impersonator Phishing Campaign
A recently observed phishing campaign impersonates Amazon and states that the recipient’s Prime membership is set to renew; however, their payment method needs updating. The email includes a link that leads to a webpage with a Google Docs URL, claiming to be from Amazon.
Beware: Holiday Season Threats
The holiday season presents an attractive target for financially motivated cybercriminals who seek to exploit online retailers and shoppers. Despite the challenges posed by high inflation rates, the National Retail Federation (NRF) predicts a three to four percent increase in retail sales...
Vulnerabilities in Mozilla Products
Multiple vulnerabilities have been discovered in Mozilla products, the most severe of which could allow for arbitrary code execution. Mozilla Firefox is a web browser used to access the Internet. Mozilla Firefox ESR is a version of the web browser to be deployed in large organizations.
In Depth: Top Exploited Vulnerabilities
In November 2024, a Joint Cybersecurity Advisory published by CISA, the FBI, and other partners detailed the most exploited vulnerabilities of 2023. These vulnerabilities garner urgency for remediation as these vulnerable systems are actively targeted.
Threat Actors Hijack Sitting Ducks
Threat actors continue to employ the “Sitting Ducks” technique to hijack legitimate domains for phishing and investment fraud. Analysts reported nearly 800,000 vulnerable domains in three months, with about 9 percent subsequently hijacked. This method exploits misconfigured DNS settings.
Volt Reestablishes KV Botnet
Analysts recently identified the resurgence of the KV botnet, an operational relay box (ORB) network associated with the Chinese APT group Volt Typhoon. Their modus operandi involves compromising outdated and end-of-life SOHO devices.
’Tis the Season for Infostealing
Threat actors actively seek methods to conceal their identities in information-stealing campaigns, aiming to lure individuals into downloading malicious software or revealing sensitive information. One recent campaign infects Windows devices with Lumma Stealer...
#StopRansomware: BianLian Data Extortion
This Joint Cybersecurity Advisory is part of an ongoing #StopRansomware effort to publish advisories for network defenders that detail various ransomware variants and ransomware threat actors. These advisories include recently and historically observed activity.
Our Services
C3 helps reduce the risk of compromise by promoting cybersecurity education and awareness, and by facilitating research, development and dissemination of viable cybersecurity defense products and services to individuals, public and private organizations in the United States.
In-Person Training Classes
Virtual Classes
Phishing Simulations
Security Posture Analysis
Credential Leak Checks
Policies, Procedures & Plans
Phishing Attack Prevention
Network Intrusion Protection
Actionable Intelligence
Cyber Command is a registered 501(c)(3) nonprofit, public charity. EIN 93-2718000.
Our Board of Directors

Joshua Weiss, President

Arthur Warady, Treasurer

Kelly Whitis, Secretary
Contact Us
We’d love to hear from you. Please use the contact form below to reach us.