Cyber Command
Cyber Command Corporation is an IRS approved 501(c)(3) nonprofit, public charity that offers cybersecurity awareness training and develops viable cybersecurity defense software.
Mission Statement
Cybersecurity concerns are one of the most critical threats facing the security of our nation, which impacts all United States citizens, including individuals, families, businesses of all sizes and verticals, and government organizations.
Our mission is to reduce threat risk by promoting cybersecurity education and awareness, facilitating research, advancing development, and enabling dissemination of cybersecurity defense products and services to USA individuals, public and private organizations.
Want to organize a free virtual or in-person cybersecurity class for seniors in your neighborhood? Please contact us below and we’ll get the process started!
Cybersecurity Intelligence Feed & Resources
This section contains free cybersecurity related articles and knowledge to help learn critical cybersecurity lessons.
Primary Mitigations to Reduce Cyber Threats
The Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI), the Environmental Protection Agency (EPA), and the Department of Energy (DOE)—hereafter referred to as “the authoring organizations”—are aware of cyber incidents...
Vulnerability in SonicWall SMA
A vulnerability has been discovered in SonicWall Secure Mobile Access (SMA) 100 Management Interface, which could allow for remote code execution. SonicWall Secure Mobile Access (SMA) is a unified secure access gateway used by organizations.
Multiple Vulnerabilities in Google Android OS
Multiple vulnerabilities have been discovered in Google Android OS, the most severe of which could allow for remote code execution with no additional execution privileges needed. Android is an operating system developed by Google for mobile devices, such as smartphones.
Commvault Vulnerability Exploited
Cyber threat actors are exploiting a Commvault vulnerability tracked as CVE-2025-3928. The flaw in the Commvault Web Server could allow an authenticated remote user to create and execute web shells. Commvault is widely used for data backup and management..
The Risks of Email Forwarding
The NJCCIC periodically receives reports of New Jersey users implementing mailbox forwarding rules that automatically forward messages from their work email to an external mailbox that is not monitored by their organization. Email forwarding to external non-work accounts...
Multiple Vulnerabilities in Mozilla Products
Multiple vulnerabilities have been discovered in Mozilla products, the most severe of which could allow for arbitrary code execution. Successful exploitation of the most severe of these vulnerabilities could allow for arbitrary code execution. Depending on the privileges associated...
Vulnerability in SAP NetWeaver
A vulnerability has been discovered in SAP NetWeaver Visual Composer, which could allow for remote code execution. SAP NetWeaver Visual Composer is SAP’s web-based software modelling tool. It enables business process specialists and developers to create...
Microsoft Exchange Server 2016 and 2019
Microsoft Exchange Server 2016 and 2019 will reach end-of-life status on October 14. While these systems will continue to run, they will no longer receive security patches or bug fixes. Additionally, extended support and Extended Security Updates will not be offered.
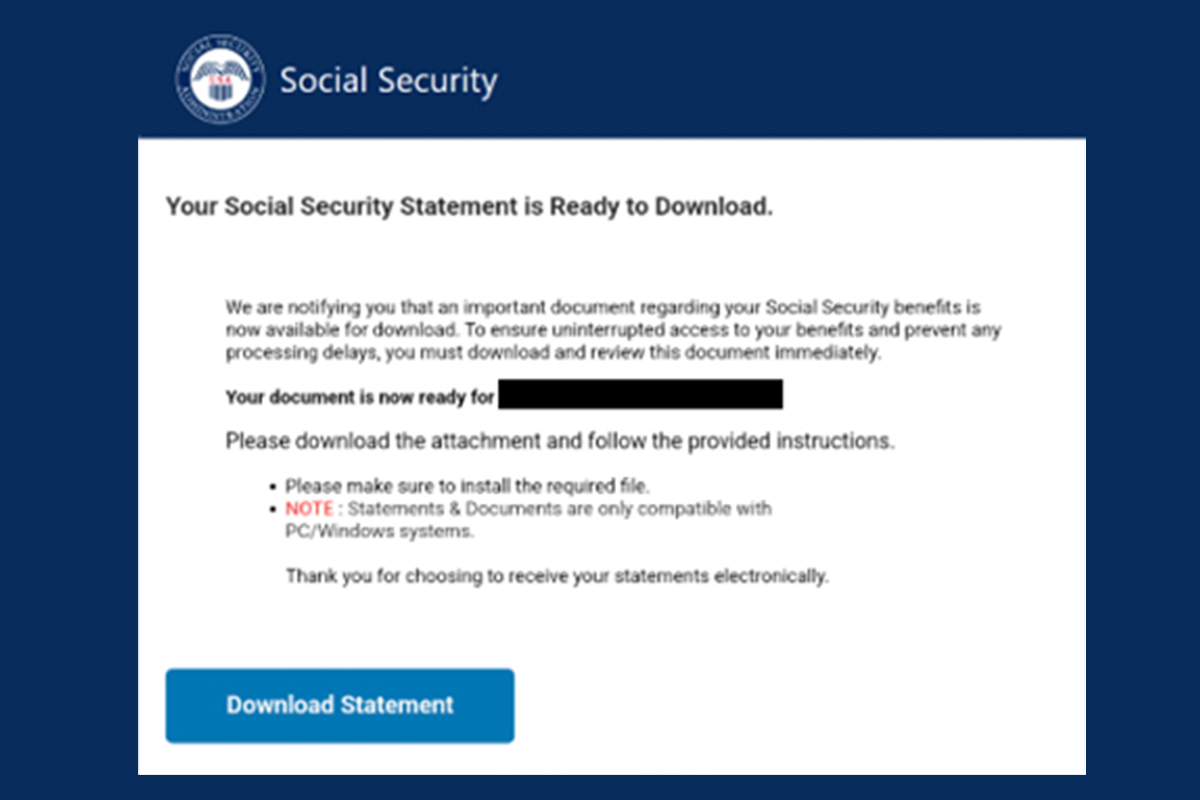
Social Security Phishing Emails
The NJCCIC received reports of Social Security Administration (SSA) phishing emails, consistent with the SSA’s scam alert earlier this month. The emails contain SSA branding to appear legitimate and claim to be from the SSA. However, upon further inspection, they were sent from...
Our Services
C3 helps reduce the risk of compromise by promoting cybersecurity education and awareness, and by facilitating research, development and dissemination of viable cybersecurity defense products and services to individuals, public and private organizations in the United States.
In-Person Training Classes
Virtual Classes
Phishing Simulations
Security Posture Analysis
Credential Leak Checks
Policies, Procedures & Plans
Phishing Attack Prevention
Network Intrusion Protection
Actionable Intelligence
Cyber Command is a registered 501(c)(3) nonprofit, public charity. EIN 93-2718000.
Our Board of Directors

Joshua Weiss, President

Arthur Warady, Treasurer

Kelly Whitis, Secretary
Contact Us
We’d love to hear from you. Please use the contact form below to reach us.