Payroll Phishing InfoStealer Malware
Malware
November 14, 2024
TThe NJCCIC email security system has uncovered a new campaign spreading XLoader and GuLoader malware. XLoader is a successor to Formbook infostealing malware and is categorized as malware-as-a-service (MaaS). XLoader has several capabilities, such as capturing screenshots, recording keystrokes, and accessing information stored on the clipboard. Additionally, it can steal credentials from browsers, email accounts, and messaging applications. GuLoader is a malware downloader that often utilizes Google Drive for payload storage. GuLoader allows for multiple download locations to establish redundancy.
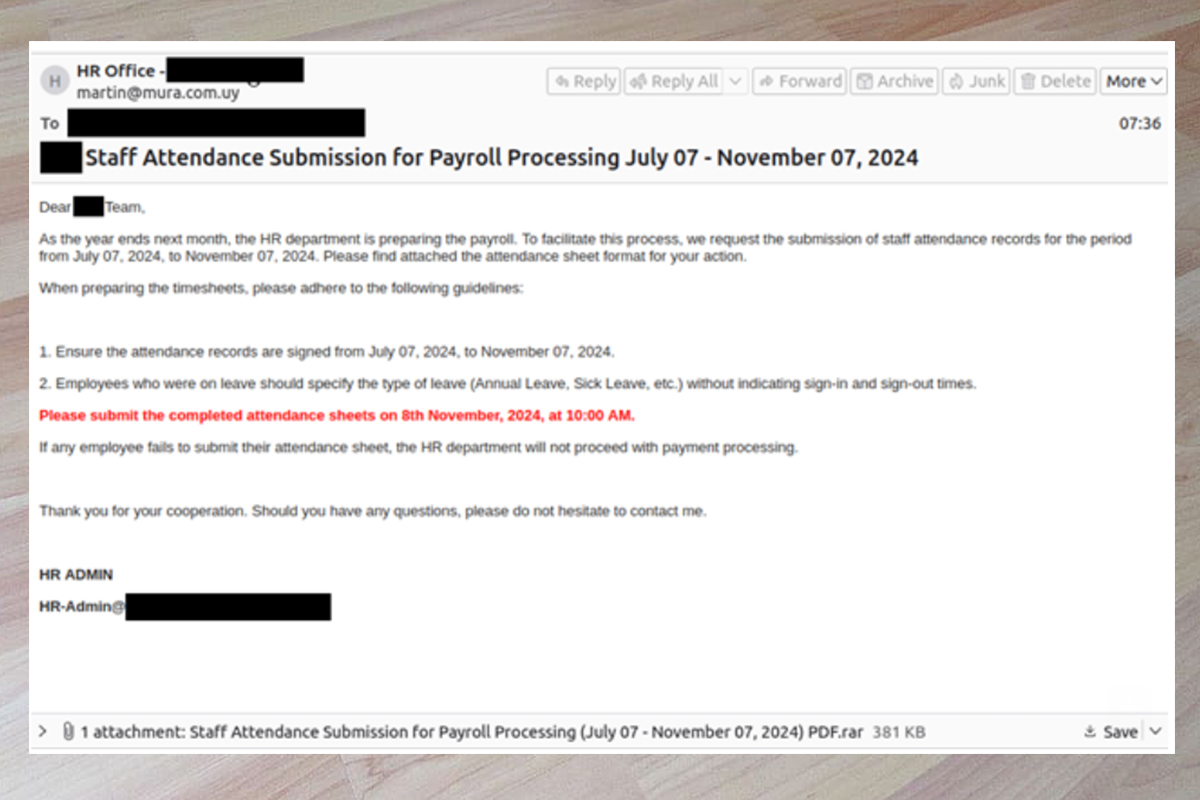
In this campaign, threat actors send emails containing compressed executable files. These messages purport to be sent from a generic HR administrator and claim that the attached staff attendance form must be completed by a specified deadline; otherwise, payments will not be processed. If users open and run the compressed executables, GuLoader and XLoader begin to install on the device.
Recommendations
- Avoid clicking links and opening attachments in unsolicited emails.
- Confirm requests from senders via contact information obtained from verified and official sources.
- Type official website URLs into browsers manually.
- Facilitate user awareness training to include these types of phishing-based techniques.
- Maintain robust and up-to-date endpoint detection tools on every endpoint.
- Consider leveraging behavior-based detection tools rather than signature-based tools.